
Clojure - the Reader and Evaluator (4/4)
Part of a series teaching the Clojure language. For other programming topics, visit http://codeschool.org
From playlist the Clojure language

Clojure - the Reader and Evaluator (2/4)
Part of a series teaching the Clojure language. For other programming topics, visit http://codeschool.org
From playlist the Clojure language

What is a Bézier curve? Programmers use them everyday for graphic design, animation timing, SVG, and more. #shorts #animation #programming Animated Bézier https://www.jasondavies.com/animated-bezier/
From playlist CS101

Source Boston 2010: Linux Kernel Exploitation: Earning Its Pwnie a Vuln at a Time 4/5
Clip 4/5 Speaker: Jon Oberheide, University of Michigan As userspace applications and services become increasingly hardened against traditional memory corruption exploits, operating system kernels have become a source for abundant exploitation opportunities. In particular, the Linux kerne
From playlist SOURCE Boston 2010
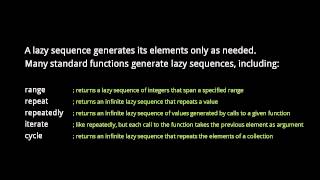
Part of a series teaching the Clojure language. For other programming topics, visit http://codeschool.org
From playlist the Clojure language

Top 10 GitHub Alternatives to Host Your Open Source Projects | #github #programming
Don’t forget to subscribe! This video is about the top 10 GitHub alternatives to host your open-source projects. GitHub is a collaborative, powerful open-source web-based platform that uses Git the open-source version control software. It is particularly well known as a development platfo
From playlist Programming Tutorials

Source Boston 2010: Linux Kernel Exploitation: Earning Its Pwnie a Vuln at a Time 3/5
Clip 3/5 Speaker: Jon Oberheide, University of Michigan As userspace applications and services become increasingly hardened against traditional memory corruption exploits, operating system kernels have become a source for abundant exploitation opportunities. In particular, the Linux kerne
From playlist SOURCE Boston 2010

An intro to the core protocols of the Internet, including IPv4, TCP, UDP, and HTTP. Part of a larger series teaching programming. See codeschool.org
From playlist The Internet

Cocaine Runners Caught | National Geographic
When this drug runner gets busted, his partner in crime gives him an ultimatum -- take the rap, or else. ➡ Subscribe: http://bit.ly/NatGeoSubscribe About National Geographic: National Geographic is the world's premium destination for science, exploration, and adventure. Through their worl
From playlist Locked Up Abroad: Season 1

Beyond the Gardens: The Plant Family Tree
The Herbarium at Kew is a vast Victorian maze filled with arcane books, learned scientists and cabinet after cabinet of dried catalogued plants. Tracing 160 years, Mark Chase, Head of the Jodrell Laboratory at Kew, reveals how the Herbarium has evolved from a modest collection of dried pl
From playlist American Museum of Natural History's Wonders of Nature

ShmooCon 2012: Android Mind Reading: Memory Acquisition and Analysis with DMD and Volatility (EN)
Speaker: Joe Sylve This talk will present the first methodology and toolset for acquisition and deep analysis of volatile physical memory from Android devices. We will discuss some of the challenges in performing Android memory acquisition, discuss our new kernel module for dumping memory
From playlist ShmooCon 2012

Star Wars: The Phantom Menace Review (Part 1 of 7)
ORIGINAL UPLOAD DATE: December 10, 2009 http://www.redlettermedia.com - Finally it's here! The truly epic review/critique/analysis/film making educational video of the 1999 film "Star Wars: The Phantom Menace" There was so much to discuss with this film it had to be long so please don't
From playlist Essential viewing

Source Boston 2010: Linux Kernel Exploitation: Earning Its Pwnie a Vuln at a Time 1/5
Clip 1/5 Speaker: Jon Oberheide, University of Michigan As userspace applications and services become increasingly hardened against traditional memory corruption exploits, operating system kernels have become a source for abundant exploitation opportunities. In particular, the Linux kerne
From playlist SOURCE Boston 2010

Source Boston 2010: Linux Kernel Exploitation: Earning Its Pwnie a Vuln at a Time 2/5
Clip 2/5 Speaker: Jon Oberheide, University of Michigan As userspace applications and services become increasingly hardened against traditional memory corruption exploits, operating system kernels have become a source for abundant exploitation opportunities. In particular, the Linux kerne
From playlist SOURCE Boston 2010

Source Boston 2010: Linux Kernel Exploitation: Earning Its Pwnie a Vuln at a Time 5/5
Clip 5/5 Speaker: Jon Oberheide, University of Michigan As userspace applications and services become increasingly hardened against traditional memory corruption exploits, operating system kernels have become a source for abundant exploitation opportunities. In particular, the Linux kerne
From playlist SOURCE Boston 2010

Operating System Full Course | Operating System Tutorials for Beginners
An operating system is system software that manages computer hardware and software resources and provides common services for computer programs. In this operating system full course you will be learning following topic in details. Hardware Resources Introduction
From playlist Operating System

Part of a series teaching the Clojure language. For other programming topics, visit http://codeschool.org
From playlist the Clojure language
How to Work with Wikipedia Sandbox
This is a short video that helps students or editors of Wikipedia to access and edit in the Sandbox of their user account. This was made for the Wiki Edu Project. I do not own or hold copyright over any aspect of the Wikipedia site or its pages. ***There is no audio***
From playlist Wikipedia Education Dashboard Tutorials

GCSE Maths: Probability Tree Diagrams
Learn how to use probability tree diagrams to calculate the probability of an event happening. Bobby introduces the topic, Susan uses an interactive tool on GeoGebra – go to https://www.geogebra.org/m/EEwVfExN to join in at home – and Tom applies what we’ve learned to a fictional FA Cup qu
From playlist Tom Rocks GCSE Maths Appeal
