Learn how to transmit audio over a laser beam. And incase you are wondering. Yes. This is true. The CIA has been using this technology for decades.
From playlist Cool Science Tricks

28C3: Building a Distributed Satellite Ground Station Network - A Call To Arms (en)
For more information visit: http://bit.ly/28C3_information To download the video visit: http://bit.ly/28C3_videos Playlist 28C3: http://bit.ly/28C3_playlist Speakers:Andreas -horn- Hornig | hadez Hackers need satellites. Hackers need internet over satellites. Satellites require g
From playlist 28C3: Behind Enemy Lines

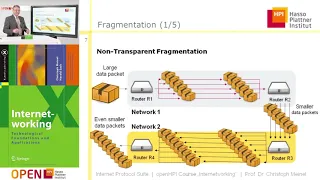
An intro to the core protocols of the Internet, including IPv4, TCP, UDP, and HTTP. Part of a larger series teaching programming. See codeschool.org
From playlist The Internet

Secure Computation Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

23C3: An Introduction to Traffic Analysis
Speaker: George Danezis Attacks, Defences and Public Policy Issues... This talk will present an overview of traffic analysis techniques, and how they can be used to extract data from 'secure' systems. We will consider both state of the art attacks in the academic literature, but also pr
From playlist 23C3: Who can you trust

Lecture 2 - Types of Wireless communication
Lecture Series on Wireless Communications by Dr.Ranjan Bose, Department of Electrical Engineering, IIT Delhi. For more details on NPTEL, visit http://nptel.iitm.ac.in
From playlist Wireless Communication

DEFCON 16: The emergence (and use) of Open Source Warfare
Speaker: Peter Berghammer, CEO, Copernio Holding Company The presentation will deal briefly (20 minutes) with the concepts surrounding Open Source Warfare (OSW) and broader adoption for use not only within the context of war fighting, but also its uses within the political arena in order
From playlist DEFCON 16

VPN - Virtual Private Networking
Follow the Insanity at: https://www.FailedNormal.com Downloadable Podcasts at: https://failednormal.podbean.com iTunes: https://itunes.apple.com/us/podcast/failed-normal/id1349818284?mt=2
From playlist Information theory and Coding

Lec 15 | Special Topics in Supply Chain Management
RFID Systems and Applications Beyond the Supply Chain Steve Miles, MIT (Moderator) Zhiwen Zhang, Ministry of Science and Technology, China Peter Friess, European Commission Daeyoung Kim, ICU Jin Hee Yoon, SK Telecom View the complete course at: http://ocw.mit.edu/ESD-290S05 Li
From playlist MIT ESD.290 Special Topics in Supply Chain Management

Network Security, Part 1 : Basic Encryption Techniques
Fundamental concepts of network security are discussed. It provides a good overview of secret Key and public key Encryption. Important data encryption standards are presented.
From playlist Network Security

DeepSec 2007: The Business Case for removing your perimeter
Thanks to the DeepSec organisation for making these videos available and let me share the videos on YouTube. Speaker: Paul Simmonds, Global Information Security Director, ICI, Jericho Forum The days of the corporate network, completely isolated with a well secured outer shell are long go
From playlist DeepSec 2007

IMT4306: Anonymous communication protocols
IMT4306: Research in Mobile/Decentralised technologies Anonymity, privacy, anonymous communication protocols.
From playlist Archive - Research in Mobile/Wearable Tech

Top 5 Alien Cover-Ups by the US Government | Ancient Aliens
The following are the top 5 instances of government cover-ups regarding alien activity. 00:00 The Navy, Nuclear Weapons and UFOs 04:15 Inexplicable Flying Objects 08:41 US Government Sees More than We Know 12:34 Project Blue Book Attempts to Prove UFO Phenomenon 16:47 The Roswell In
From playlist Ancient Aliens: Official Series Playlist | New Episodes Fridays at 9/8c | History

Shmoocon 2010: honeyM: A Framework For Virtual Mobile Device Honeyclients 2/4
Clip 2/4 Speakers: Navas, K - Cadet, US Military Academy, Brasefield, D - Cadet, US Military Academy, Grunzweig, N - Cadet, US Military Academy, OConnor, T - Faculty Advisor, US Military Academy This talk will discuss an implementation of a honeyclient framework for mobile devices. In
From playlist ShmooCon 2010

100 Seconds to Midnight - https://aperture.gg/seconds Bulletin of the Atomic Scientists: https://thebulletin.org/ Merch: https://aperture.gg/merch Stay connected with Aperture: Website: https://aperture.gg/ Instagram: https://www.instagram.com/theapertureyt/ Twitter: https://twitter.com/
From playlist Science & Technology 🚀

CERIAS Security: Security in Infrastructureless and Decentralized Communication Networks 3/5
Clip 3/5 Speaker: Andre Koenig · Technical University Darmstadt Infrastructureless and decentralized communication substrates such as mobile ad hoc networks and peer-to-peer systems enable setting up communication services beyond borders of contemporary wired or cellular client/server sy
From playlist The CERIAS Security Seminars 2009

Understanding Modulation! | ICT #7
Modulation is one of the most frequently used technical words in communications technology. One good example is that of your FM radio, where FM stands for frequency modulation. In this video we are going to learn the basics of modulation techniques and see how they are applied in modern ce
From playlist Internet & Telecommunication Technology