
Evaluate the composition of sine and sine inverse
👉 Learn how to evaluate an expression with the composition of a function and a function inverse. Just like every other mathematical operation, when given a composition of a trigonometric function and an inverse trigonometric function, you first evaluate the one inside the parenthesis. We
From playlist Evaluate a Composition of Inverse Trigonometric Functions

Evaluating for the composition of sine and inverse sine
👉 Learn how to evaluate an expression with the composition of a function and a function inverse. Just like every other mathematical operation, when given a composition of a trigonometric function and an inverse trigonometric function, you first evaluate the one inside the parenthesis. We
From playlist Evaluate a Composition of Inverse Trigonometric Functions
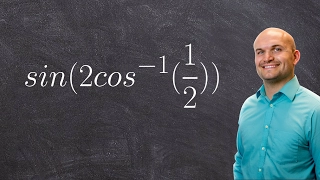
Learn how to evaluate the composition of a function and inverse function
👉 Learn how to evaluate an expression with the composition of a function and a function inverse. Just like every other mathematical operation, when given a composition of a trigonometric function and an inverse trigonometric function, you first evaluate the one inside the parenthesis. We
From playlist Evaluate a Composition of Inverse Trigonometric Functions

This video teaches students how to write the inverse of a conditional statement. In particular, this video goes into detail about how to negate the hypothesis and conclusion of a conditional statement. In addition, the concepts of truth value, negating statements and logical equivalence ar
From playlist Geometry
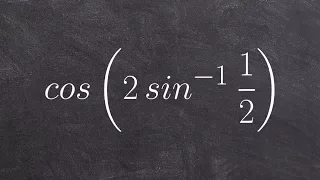
Evaluating the composition of cosine and sine inverse
👉 Learn how to evaluate an expression with the composition of a function and a function inverse. Just like every other mathematical operation, when given a composition of a trigonometric function and an inverse trigonometric function, you first evaluate the one inside the parenthesis. We
From playlist Evaluate a Composition of Inverse Trigonometric Functions

How to graph the inverse sine given the graph of sine
👉 Learn how to evaluate an expression with the composition of a function and a function inverse. Just like every other mathematical operation, when given a composition of a trigonometric function and an inverse trigonometric function, you first evaluate the one inside the parenthesis. We
From playlist Evaluate a Composition of Inverse Trigonometric Functions

One Ring to Bind Them - Mark McGranaghan
Ring is a tool for writing web applications in Clojure. It provides some functionality itself, but also acts as a binding between various other Clojure web libraries. In this talk I discuss how the Ring spec enables this interoperability, show examples of Ring-based libraries, and discuss
From playlist Clojure, Lisp

Speaker: Paul Böhm Writing your own flexible Userland TCP/IP Stack - Ninja Style!!! This talk will discuss design approaches for writing flexible userland tcp/ip stacks for network hacking tools. For more information visit: http://bit.ly/22c3_information To download the video visit: htt
From playlist 22C3: Private Investigations

LambdaConf 2015 - HTTP through Functional Programming Andrew Cherry
HTTP is a fascinating standard — one of those that we all use every day. But there are many different ways of reasoning about what HTTP "should" mean. We'll look at some of the approaches taken to model the HTTP layer, particularly in functional programming. Graphs, proofs, type systems —
From playlist LambdaConf 2015

chariotsolutions.com Alex Miller's Philly ETE 2013 screencast of "Clojure Enemy of the State"
From playlist Clojure, Lisp

Math tutorial for evaluating the composition of the sine and tangent function
👉 Learn how to evaluate an expression with the composition of a function and a function inverse. Just like every other mathematical operation, when given a composition of a trigonometric function and an inverse trigonometric function, you first evaluate the one inside the parenthesis. We
From playlist Evaluate a Composition of Inverse Trigonometric Functions

Richard Lassaigne: Introduction à la théorie de la complexité
Find this video and other talks given by worldwide mathematicians on CIRM's Audiovisual Mathematics Library: http://library.cirm-math.fr. And discover all its functionalities: - Chapter markers and keywords to watch the parts of your choice in the video - Videos enriched with abstracts, b
From playlist Mathematical Aspects of Computer Science

Ruby Conference 2007 Building Games with Ruby by Andrea O. K. Wright
Help us caption & translate this video! http://amara.org/v/FGd7/
From playlist Ruby Conference 2007

Evaluating the composition of sine and cosine functions
👉 Learn how to evaluate an expression with the composition of a function and a function inverse. Just like every other mathematical operation, when given a composition of a trigonometric function and an inverse trigonometric function, you first evaluate the one inside the parenthesis. We
From playlist Evaluate a Composition of Inverse Trigonometric Functions

Stanford Seminar - Bugs in Crypto Implementations
Whether it’s by email, text, or social media platform, the average person will send over 60 messages per day—that's 22,000 messages per year. With billions of messages sent around the world each day, how can you be sure that your messages are safe and secure? Join professor Dan Boneh, on
From playlist Stanford Seminars
"Netty - The async event-driven network application framework" by Norman Maurer
Netty - The async event-driven network application framework The internet and network is getting more important with every single day. So it may not be surprising to see that almost every application needs to interact over at least one of them these days. But writing high-performing netwo
From playlist Software Development Lectures

Evaluate the expression for the composition of inverse sine and cosine
👉 Learn how to evaluate an expression with the composition of a function and a function inverse. Just like every other mathematical operation, when given a composition of a trigonometric function and an inverse trigonometric function, you first evaluate the one inside the parenthesis. We
From playlist Evaluate a Composition of Inverse Trigonometric Functions

Stanford Seminar - The TLS 1.3 Protocol
"The TLS 1.3 Protocol" - Eric Rescorla of Mozilla and RTFM, Inc. About the talk: Transport Layer Security (TLS) is used for securing everything from Web transactions (HTTPS) to voice and video calls (DTLS-SRTP). However, the basic design of TLS dates back to the mid 1990s and the protocol
From playlist Engineering
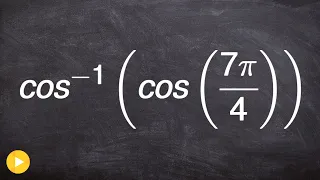
How to evaluate for the composition of two trigonometric functions
👉 Learn how to evaluate an expression with the composition of a function and a function inverse. Just like every other mathematical operation, when given a composition of a trigonometric function and an inverse trigonometric function, you first evaluate the one inside the parenthesis. We
From playlist Evaluate a Composition of Inverse Trigonometric Functions

Maurice Herlihy: Distributed Computing through Combinatorial Topology
The lecture was held within the framework of the Hausdorff Trimester Program : Applied and Computational Algebraic Topology Models and techniques borrowed from classical combinatorial algebraic topology have yielded a variety of new lower bounds and impossibility results for distributed a
From playlist HIM Lectures: Special Program "Applied and Computational Algebraic Topology"