
Staysafe.org: Protect your computer
The Internet is a global network that connects us to limitless information and opportunities. But there are risks involved with connecting to the Internet, such as downloading viruses and spyware onto computers and devices. Watch this video for four easy steps to help protect your computer
From playlist awareness

Fundamental concepts of intrusion detection are discussed. Various types of intrusion are analyzed. Password management is explained.
From playlist Network Security

Fundamental concepts of intrusion detection are discussed. Various types of intrusion are analyzed. Password management is explained.
From playlist Network Security

Network Security, Part 1 : Basic Encryption Techniques
Fundamental concepts of network security are discussed. It provides a good overview of secret Key and public key Encryption. Important data encryption standards are presented.
From playlist Network Security

How to use Facebook anonymously | Stop Facebook tracking | Protect yourself from hackers and doxxing
Do you know how to use Facebook anonymously? Facebook tracks you all over the web and to regain your online privacy, you need stop Facebook tracking mechanisms. In this video, you'll learn how to stop Facebook tracking. How much Facebook knows about you? Everything: https://youtu.be/9sFl
From playlist TUTORIALS & HOW TO's
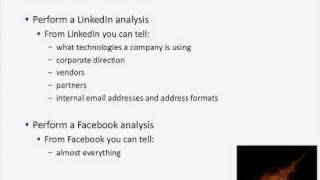
O'Reilly Webcast: Information Security and Social Networks
Social networks are an information security game changer, and enterprises and their management are struggling to understand and deal with the security risks of social networks. Traditional information security protected your corporate IT perimeter. But that won't help in the web 2.0 era
From playlist O'Reilly Webcasts

MIT 15.S50 Poker Theory and Analysis, IAP 2015 View the complete course: http://ocw.mit.edu/15-S50IAP15 Instructor: Kevin Desmond In this session Kevin Desmond discusses the tournament life cycle, flop-turn-river play, poker psychology, bankroll management, and the class league results.
From playlist MIT 15.S50 Poker Theory and Analysis, IAP 2015

What do we mean by device security? Why should we care about this?
Keep your smart devices safe! Learn what device security is, and how it protects your phones, tablets, and computers from being accessed and exploited by cybercriminals.
From playlist Internet Safety

Jason England- Cheating Devices Old and New - G4G12 April 2016
A brief look at some classic cheating devices used in poker, blackjack, craps and roulette.
From playlist G4G12 Videos

Why saying "I don't know" is a key to success | Poker champion Annie Duke | Big Think
Why saying "I don't know" is a key to success Watch the newest video from Big Think: https://bigth.ink/NewVideo Join Big Think Edge for exclusive videos: https://bigth.ink/Edge ---------------------------------------------------------------------------------- In the earliest stages of o
From playlist Best Videos | Big Think

30C3: Thwarting Evil Maid Attacks (EN)
For more information and to download the video visit: http://bit.ly/30C3_info Playlist 30C3: http://bit.ly/30c3_pl Speakers: Eric Michaud | Ryan Lackey ncreasingly, users and their computing hardware are exposed a range of software and hardware attacks, ranging from disk imaging to hardw
From playlist 30C3

Speaker: PAUL WILSON REAL HUSTLER The Art of the Con. Paul Wilson is the writer and star of "The Real Hustle" and creator of "The Takedown" on Court TV and "Scammed" on The History Channel. He is one of the world's finest magicians and an expert on cons, scams, casino cheating and gambli
From playlist DEFCON 20

What Jamie Did on Halloween - Still Untitled: The Adam Savage Project - 12/8/15
In this episode we recorded before Adam went on tour, the gang shares their reactions to the most recent Episode VII trailer and theatrical posters, talk poker stories, and take two more questions from listeners. Plus, Adam reveals what Jamie did on this past Halloween! To subscribe to S
From playlist The Adam Savage Project

How To Protect Your Online Privacy With A Threat Model | Tutorial 2022
Privacy tutorial with a threat model methodology. This will help you achieve strong privacy consistently and reliably. Support independent research: https://www.patreon.com/thehatedone Privacy tools are inconsistent. The inventory of recommended countermeasures changes all the time. On t
From playlist Security by compartmentalization - learn to protect your privacy effectively

Measuring information | Journey into information theory | Computer Science | Khan Academy
How can we quantify/measure an information source? Watch the next lesson: https://www.khanacademy.org/computing/computer-science/informationtheory/moderninfotheory/v/markov_chains?utm_source=YT&utm_medium=Desc&utm_campaign=computerscience Missed the previous lesson? https://www.khanacade
From playlist Journey into information theory | Computer Science | Khan Academy

Does it really matter what browser I choose?
You have a choice of browsers to select from. What makes a browser more - or less - secure? Learn some ways to assess a browser's security.
From playlist Internet Safety

Rimworld Version 1.0 - Rimworld Ice Sheet Tribal Ep. 33 [Rimworld 1.0 Ice Sheet Challenge]
After many Alpha and Beta versions, Rimworld 1.0 is finally here! We continue our Ice Sheet Tribal Challenge with a look at the latest changes in version 1.0 out on the Ice Sheet on Randy Random Extreme difficulty.► Full Playlist: https://goo.gl/q3Cx7t We return to the Ice Sheet in Rimwor
From playlist Pete Completes: Rimworld Ice Sheet Tribal Challenge - Starting with nothing [Rimworld Randy Random Extreme/Merciless]

MIT 15.S50 How to Win at Texas Hold 'Em, January IAP 2016 View the complete course: http://ocw.mit.edu/15-S50IAP16 Instructor: Will Ma In this lecture, Will Ma outlines the differences between playing in tournaments and cash games. License: Creative Commons BY-NC-SA More information at h
From playlist MIT 15.S50 How to Win at Texas Hold 'Em, IAP 2016

How adding your phone number and 2-factor authentication helps protect your account
Ever had to use a code that was texted to your phone to log into a website? Then you’ve used two-factor authentication. Learn more about why it’s so important, and how it creates an extra layer of security to protect your accounts and your information.
From playlist Internet Safety

7. An In-depth Combinatorial Hand Analysis in Cash Games
MIT 15.S50 How to Win at Texas Hold 'Em, January IAP 2016 View the complete course: http://ocw.mit.edu/15-S50IAP16 Instructor: Will Ma In this session, the instructor walks the students through an in-depth analysis of various hands, and conclude with some general thoughts about the game o
From playlist MIT 15.S50 How to Win at Texas Hold 'Em, IAP 2016