
This video introduced fair division. Site: http://mathispower4u.com
From playlist Fair Division

Francisco Criado: The dual 1-fair packing problem and applications to linear programming
Proportional fairness (also known as 1-fairness) is a fairness scheme for the resource allocation problem introduced by Nash in 1950. Under this scheme, an allocation for two players is unfair if a small transfer of resources between two players results in a proportional increase in the ut
From playlist Workshop: Tropical geometry and the geometry of linear programming

Any function proportional to a PMF or PDF uniquely determines it. Using proportionality is a extremely useful trick when doing Bayesian inference.
From playlist Machine Learning

Sebastian Pokutta: A distributed accelerated algorithm for the 1-fair packing problem
The proportional fair resource allocation problem is a major problem studied in flow control of networks, operations research, and economic theory, where it has found numerous applications. This problem, defined as the constrained maximization of ∑_i log x_i, is known as the packing propor
From playlist Workshop: Continuous approaches to discrete optimization

Fair Division: The Sealed Bid Method
This video explains and provides examples of how to apply the sealed bid method. Site: http://mathispower4u.com
From playlist Fair Division

CERIAS Security: Exploiting Opportunistic Scheduling in Cellular Data Networks 1/5
Clip 1/5 Speaker: Hao Chen · Assistant Professor · University of California, Davis Third Generation (3G) cellular networks utilize time-varying and location-dependent channel conditions to provide broadband services. They employ opportunistic scheduling to efficiently utilize spectrum un
From playlist The CERIAS Security Seminars 2008

Weighted Voting: Coalitions and Critical Players
This lesson defines and gives examples of coalitions and critical players in a weighted voting system. Site: http://mathispower4u.com
From playlist Weighted Voting

CERIAS Security: Exploiting Opportunistic Scheduling in Cellular Data Networks 4/5
Clip 4/5 Speaker: Hao Chen · Assistant Professor · University of California, Davis Third Generation (3G) cellular networks utilize time-varying and location-dependent channel conditions to provide broadband services. They employ opportunistic scheduling to efficiently utilize spectrum un
From playlist The CERIAS Security Seminars 2008

Voting Theory: Fairness Criterion
This video define 4 Fairness Criterion for determining the winner of an election. Site: http://mathispower4u.com
From playlist Voting Theory

CERIAS Security: Exploiting Opportunistic Scheduling in Cellular Data Networks 5/5
Clip 5/5 Speaker: Hao Chen · Assistant Professor · University of California, Davis Third Generation (3G) cellular networks utilize time-varying and location-dependent channel conditions to provide broadband services. They employ opportunistic scheduling to efficiently utilize spectrum un
From playlist The CERIAS Security Seminars 2008

CERIAS Security: Exploiting Opportunistic Scheduling in Cellular Data Networks 2/5
Clip 2/5 Speaker: Hao Chen · Assistant Professor · University of California, Davis Third Generation (3G) cellular networks utilize time-varying and location-dependent channel conditions to provide broadband services. They employ opportunistic scheduling to efficiently utilize spectrum un
From playlist The CERIAS Security Seminars 2008
2. Data Collection Techniques and Program Design
MIT 1.258J Public Transportation Systems, Spring 2017 Instructor: Nigel Wilson, Gabriel Sanchez-Martinez, Neema Nassir View the complete course: https://ocw.mit.edu/1-258JS17 YouTube Playlist: https://www.youtube.com/playlist?list=PLUl4u3cNGP62AU7iNniqVoMl8C64tIOVk This lecture discussed
From playlist MIT 1.258J Public Transportation Systems, Spring 2017

P Sreekumar: Astrosat: Project and science
PROGRAM: NUMERICAL RELATIVITY DATES: Monday 10 Jun, 2013 - Friday 05 Jul, 2013 VENUE: ICTS-TIFR, IISc Campus, Bangalore DETAL Numerical relativity deals with solving Einstein's field equations using supercomputers. Numerical relativity is an essential tool for the accurate modeling of a wi
From playlist Numerical Relativity

Lecture 1 | The Fourier Transforms and its Applications
Lecture by Professor Brad Osgood for the Electrical Engineering course, The Fourier Transforms and its Applications (EE 261). Professor Osgood provides an overview of the course, then begins lecturing on Fourier series. The Fourier transform is a tool for solving physical problems. In
From playlist Fourier

Stanford Seminar - Sensor Tracking Behavior in the Workplace
Gloria Mark University of California, Irvine Dynamic professionals sharing their industry experience and cutting edge research within the human-computer interaction (HCI) field will be presented in this seminar. Each week, a unique collection of technologists, artists, designers, and act
From playlist Stanford CS547 - Human-Computer Interaction Seminar Series

Unit 5 - practice problem 1 question
From playlist Courses and Series

Kernel Recipes 2015 - Linux kernel IO subsystem - by Jan Kara
Understanding how Linux kernel IO subsystem works is a key to analysis of a wide variety of issues occurring when running a Linux system. This talk is aimed at helping Linux users understand what is going on and how to get more insight into what is happening. First we present an overview
From playlist Kernel Recipes 2015
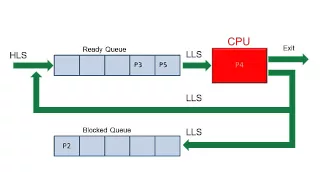
An animation showing the main features of a process scheduling system including the ready queue, blocked queue, high level scheduler and low level scheduler. It explains the principle of a round robin scheduling algorithm.
From playlist Operating Systems

