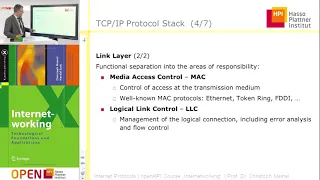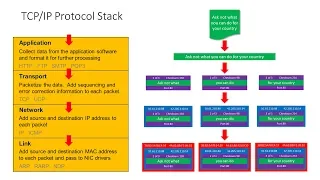
Computer Networks. Part Six: The TCP/IP Protocol Stack and Routers
This is the sixth in a series about computer networks. This video describes the role of a network protocol, and specifically details the TCP/IP suite of protocols. The need for a layered approach to networking software is discussed including the four layer TCP/IP stack and the relevance
From playlist Computer Networks

Leveraging OWASP in Open Source Projects - Aaron Weaver, David Ohsie, Bill Thompson
Leveraging OWASP in Open Source Projects - CAS AppSec Working Group - Aaron Weaver, David Ohsie, Bill Thompson The CAS AppSec Working Group is a diverse volunteer team of builders, breakers, and defenders that is working to improve the security of Jasig CAS, an open source WebSSO project.
From playlist AppSecUSA 2013

Transport Layer Security: Part 2 - TLS & HTTPS
Fundamental concepts of TLS are discussed. SSL is analyzed. HTTPS & SSH are presented.
From playlist Network Security

Ruby Conference 2007 Next-Gen VoIP Development with Adhearsion by Jay Phillips
Help us caption & translate this video! http://amara.org/v/FGdF/
From playlist Ruby Conference 2007

Intro to Priority Lists & Schedules
Worked out examples involving priority lists and schedules.
From playlist Discrete Math

Iliyan Peychev: HTTP 2.0 and QUIC - protocols of the (near) future | JSConf EU 2014
The new HTTP 2.0 and QUIC protocols are coming! HTTP 1.1 forced both developers and browser vendors to invent different tricks in order to make sites to load and run faster. HTTP 2.0 and QUIC will provide many significant improvements overt HTTP 1.1. In this talk I will give an introduct
From playlist JSConf EU 2014

Shmoocon 2010: WLCCP - Analysis of a Potentially Flawed Protocol 3/6
Clip 3/6 Speakers: Enno Rey & Oliver Roeschke The world of "Enterprise WLAN solutions" is full of obscure and "non-standard" elements and technologies. One prominent example is Cisco's Structured Wireless-Aware Network (SWAN) architecture, composed of autonomous access points combined
From playlist ShmooCon 2010

ElixirConf 2015 - Into Production by Jamie Winsor
The goal of this talk is to provide new and existing Elixir programmers with knowledge on how to get their application into production and, once it's there, how to tune it for scale. Help us caption & translate this video! http://amara.org/v/HOqZ/
From playlist ElixirConf 2015

Black Hat USA 2010: Burning Asgard: What Happens When Loki Breaks Free 5/5
Speakers: Enno Rey, Daniel Mende I personally remember the release of Yersinia at Black Hat Europe 2005. It was a ground breaking experience: a number of Layer 2 attacks regarded purely theoretical until then, was suddenly available in a mostly automated way. And those guys even showed so
From playlist BH USA 2010 - NETWORK

ShmooCon 2011: Stealing Sensitive Data from Thousands of Systems Simultaneously with OpenDLP
Speaker: Andrew Gavin Got domain admin to a couple of thousand Windows systems? Got an hour to spare? Steal sensitive data from all of these systems simultaneously in under an hour with OpenDLP. OpenDLP is an open source, agent-based, massively distributable, centrally managed data disc
From playlist ShmooCon 2011

Jelani Nelson: Private frequency estimation via projective geometry
CONFERENCE Recording during the thematic meeting : "Learning and Optimization in Luminy" the October 3, 2022 at the Centre International de Rencontres Mathématiques (Marseille, France) Filmmaker: Guillaume Hennenfent Find this video and other talks given by worldwide mathematicians on C
From playlist Mathematical Aspects of Computer Science

GRCon19 - Streaming with DPDK: Raising the Throughput Ceiling with Drivers in Use.. by Alex Williams
Streaming with DPDK: Raising the Throughput Ceiling with Drivers in Use Space by Alex Williams Software latency is the biggest impediment to high-speed streaming from a computer, and expensive kernel interactions are the primary source. System calls and buffer copying add to processing ti
From playlist GRCon 2019

Transport Layer Security: Part 1
Fundamental concepts of TLS are discussed. SSL is analyzed. HTTPS & SSH are presented.
From playlist Network Security

Secure Computation Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Engineering Ethics: Crash Course Engineering #27
We’ve talked about many important concepts for engineers, but today we’re going to discuss a hugely important one that you might not even realize is an engineering concept: ethics. We’ll talk about what a Code of Ethics is. We’ll explore engineering ethics and the ethical theories of utili
From playlist Engineering

Scheduling: The Critical Path Algorithm Version 1 (Part 1)
This lesson explains how to create a priority list using version 1 of the critical path algorithm. Site: http://mathispower4u.com
From playlist Scheduling