
Extending the capabilities of Python with the NumPy module
From playlist Introduction to Pyhton for mathematical programming
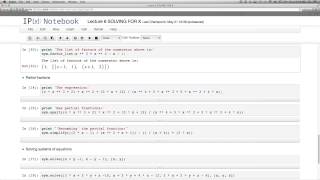
Using Sympy to solve algebraic expressions and equations.
From playlist Introduction to Pyhton for mathematical programming

GCSE Revision Video 8 - Pythagoras
Powered by https://www.numerise.com/ GCSE Revision Video 8 - Pythagoras
From playlist GCSE Quick Revision List

8ECM Plenary Lecture: János Pach
From playlist 8ECM Plenary Lectures

A Cheeky Proof of Pythagoras! MUST LEARN GCSE MATHS FORMULAE: https://youtu.be/wbh3fZYz3ko Hey guys! It's my mission to help you as much as I can with your maths and get the grades you deserve (and need!) I'll focus mostly on the new GCSE 9-1 specification, higher and foundation, as no
From playlist Pythagoras GCSE 9-1 Maths
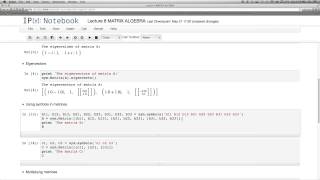
Various manipulations of matrices including teh caclulation of eigenvalues and eigenvectors.
From playlist Introduction to Pyhton for mathematical programming
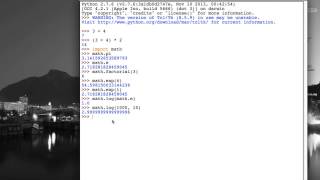
Extending the capabilities of Python with the Math module
From playlist Introduction to Pyhton for mathematical programming

For more information visit: http://bit.ly/28C3_information To download the video visit: http://bit.ly/28C3_videos Playlist 28C3: http://bit.ly/28C3_playlist Speaker: Sebastian Schinzel Exploiting Timing Side Channel Vulnerabilities on the Web Timing side channel attacks are non-
From playlist 28C3: Behind Enemy Lines

0432 - Rust: rewriting game front-end using Yew
This is #432 in my series of live (Twitch) coding streams. This stream I got the admin authentication system up and running in the Rust rewrite of my game. Notebook page: https://tinyurl.com/4sfsy752 -- Watch live at https://www.twitch.tv/rhymu8354
From playlist Excalibur

Setting up and solving ordinary differential equations with constant coefficients.
From playlist Introduction to Pyhton for mathematical programming

Kernel Recipes 2017 - Modern Key Management with GPG - Werner Koch
Although GnuPG 2 has been around for nearly 15 years, the old 1.4 version was still in wide use. With Debian and others making 2.1 the default, many interesting things can now be done. In this talk he will explain the advantages of modern key algorithms, like ed25519, and why gpg relaxed s
From playlist Kernel Recipes 2017

Poisons and Venoms and Toxins, Oh My!
From daffodils to dangerous snakes, toxins are everywhere. Here's a collection of episodes about our favorite poisonous, venomous, and generally toxic organisms. Hosted by: Stefan Chin SciShow has a spinoff podcast! It's called SciShow Tangents. Check it out at http://www.scishowtangents
From playlist Uploads

Introduction to Chemical Biology 128. Lecture 18. Terpenes and Cell Signaling, Part 2
UCI Chem 128 Introduction to Chemical Biology (Winter 2013) Lec 18. Introduction to Chemical Biology -- Terpenes and Cell Signaling -- Part 2 View the complete course: http://ocw.uci.edu/courses/chem_128_introduction_to_chemical_biology.html Instructor: Gregory Weiss, Ph.D. License: Creat
From playlist Chem 128: Intro to Chem Biology

A brief introduction to Python. Where to go to download Python and what to install.
From playlist Introduction to Pyhton for mathematical programming

Amir Hay - DNA-PK impedes DNA demage-induced transcription of stress response genes
Organisms are continuously exposed to sublethal stresses, but how they respond to such stresses at the molecular level is still largely unknown. One known mechanism is genetic regulation of stress response proteins, such as HSP72 -which is encoded by both HSPA1A and HSPA1B ge
From playlist From Molecules and Cells to Human Health : Ideas and concepts
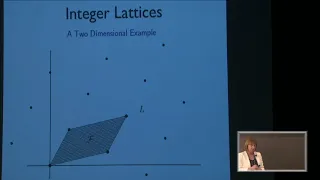
Mathematical Ideas in Lattice Based Cryptography - Jill Pipher
2018 Program for Women and Mathematics Topic: Mathematical Ideas in Lattice Based Cryptography Speaker: Jill Pipher Affiliation: Brown University Date: May 21, 2018 For more videos, please visit http://video.ias.edu
From playlist Mathematics

Computational Aspects in the Braid Group and Applications to Cryptography - Mina Teicher
Mina Teicher Bar-Ilan University; Member, School of Mathematics March 12, 2012 The braid group on n strands may be viewed as an infinite analog of the symmetric group on n elements with additional topological phenomena. It appears in several areas of mathematics, physics and computer scien
From playlist Mathematics
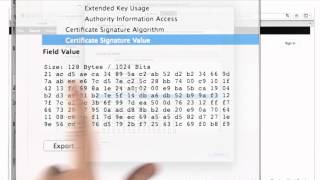
Certificates And Signatures - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Dealing with limits in Sympy.
From playlist Introduction to Pyhton for mathematical programming

This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography