
IDEspinner Buffer Overflows pt1
This movie tries to show how you can create a bufferoverflow Credits go out to IDEspinner
From playlist Buffer overflow

From playlist Buffer overflow

Tutorial: GeoHTTP Remote Buffer Overflow and DoS
A real example of a Buffer Overflow/Denial of Service attack! My favorite video: http://www.youtube.com/watch?v=z00kuZIVXlU Visit http://binslashshell.wordpress.com and join our forum community!!! This is a video showing what a Buffer Overflow Aattck can do to a Web Server. For th
From playlist Denial of Service attacks

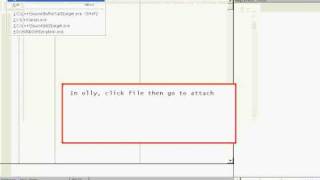
Bufferoverflow part 3 - exploit coding for a commandline attack vector 1/2
Credits go out to IDEspinner, checkout his website: http://www.crackingislife.com/ clip 1/2
From playlist Buffer overflow

In this video, we take a look at how you can quickly create the LaTeX logo on overleaf.
From playlist Tech Ideas
Bufferoverflow part 3 - exploit coding for a commandline attack vector 2/2
Credits go out to IDEspinner, checkout his website: http://www.crackingislife.com/ clip 2/2
From playlist Buffer overflow

Stack Overflow Inverted Index | MapReduce Use Case | MapReduce Design Patterns Tutorial | Edureka
Watch Sample Class recording: http://www.edureka.co/mapreduce-design-patterns?utm_source=youtube&utm_medium=referral&utm_campaign=stackover-mapreduce-design Stack overflow occurs if the stack pointer exceeds the stack bound. The call stack may consist of a limited amount of address space,
From playlist MapReduce Design Patterns Tutorial Videos

Bufferoverflow part 2- machine shellcoding 2/2
Credits go out to IDEspinner, checkout his website: http://www.crackingislife.com/ clip 2/2
From playlist Buffer overflow

Bufferoverflow part 2- machine shellcoding 1/2
Credits go out to IDEspinner, checkout his website: http://www.crackingislife.com/ clip 1/2
From playlist Buffer overflow

ELEC2141 Digital Circuit Design - Lecture 25
ELEC2141 Week 9 Lecture 3: Arithmetic Circuits
From playlist ELEC2141 Digital Circuit Design

NES Emulator Part #2: The CPU (6502 Implementation)
In this video I build a 6502 emulation in C++. I pay close attention to the instructions that can cause problems, ADC and SBC. Then I build a lightweight application to analyze running 6502 programs. Source: https://github.com/OneLoneCoder/olcNES YouTube: https://www.youtube.com/javidx9
From playlist NES Emulator From Scratch

28C3: Post Memory Corruption Memory Analysis (en)
For more information visit: http://bit.ly/28C3_information To download the video visit: http://bit.ly/28C3_videos Playlist 28C3: http://bit.ly/28C3_playlist Speaker: endrazine Automating exploitation of invalid memory writes Pmcma is a tool aimed at automating the most time cons
From playlist 28C3: Behind Enemy Lines

0037 (part 1) - Custom C++ Web Server: refactoring
This is #37 in my series of live (Twitch) coding streams, working on writing my own web server and service framework in C++. This stream I worked on more refactoring: * Removing std::shared_ptr where I don't really need it. * Use SHA-1 to calculate entity tags. * Clean up lifecycle method
From playlist Excalibur

Embedded Systems - Chap 5b - Timers - Professor E. Ambikairajah - UNSW Sydney
Electrical Systems Design (Embedded Systems Design) - Timers - Computer Interfacing - Microcontrollers - Electronic Whiteboard-Based Lecture - Lecture notes available from: http://eemedia.ee.unsw.edu.au/contents/elec2117/LectureNotes/
From playlist Introduction to Embedded Systems - by Professor Eliathamby Ambikairajah UNSW Sydney

How Computers Calculate - the ALU: Crash Course Computer Science #5
Today we're going to talk about a fundamental part of all modern computers. The thing that basically everything else uses - the Arithmetic and Logic Unit (or the ALU). The ALU may not have to most exciting name, but it is the mathematical brain of a computer and is responsible for all the
From playlist Computer Science

From playlist CS50 Sections 2012

RubyConf 2017: Buuuuugs iiiiin Spaaaaace! by Colin Fulton
RubyConf 2017: Buuuuugs iiiiin Spaaaaace! by Colin Fulton Space is really cool. From precision electronics, to giant rockets, spacecraft can represent the best of engineering. But sometimes things go wrong. Terribly wrong. What do exploding Soviet rockets have to do with Agile developmen
From playlist RubyConf 2017

DEFCON 15: (un)Smashing the Stack: Overflows, Countermeasures, and the Real World
Speaker: Shawn Moyer Chief Researcher, SpearTip Technologies As of today, Vista, XP, 2K03, OS X, every major Linux distro, and each of the BSD's either contain some facet of (stack|buffer|heap) protection, or have one available that's relatively trivial to implement/enable. So, this shoul
From playlist DEFCON 15

LESSON 30: Advanced Software Interrupt Techniques for Reading Serial Data on Arduino
You guys can help me out over at Patreon, and that will keep this high quality content coming: https://www.patreon.com/PaulMcWhorter This lesson shows how to use software interrupts to read serial data on the Arduino. This is demonstrated using the adafruit ultimate gps. You can follow t
From playlist Arduino Lessons

An general explanation of the underactive thyroid.
From playlist For Patients