
Sensitivity (Electrical Engineering)
https://www.patreon.com/edmundsj If you want to see more of these videos, or would like to say thanks for this one, the best way you can do that is by becoming a patron - see the link above :). And a huge thank you to all my existing patrons - you make these videos possible. In this video
From playlist Advanced Circuit Design

04-2 Sensitivity Analysis Global
Sobol' and regionalized sensitivity analysis
From playlist QUSS GS 260
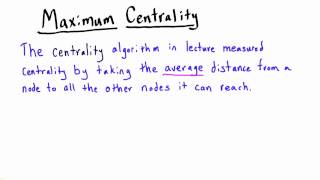
Centrality - Intro to Algorithms
This video is part of an online course, Intro to Algorithms. Check out the course here: https://www.udacity.com/course/cs215.
From playlist Introduction to Algorithms

Cryptographic Hash Function - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Overview of various methods for sensitivity analysis in the UQ of subsurface systems
From playlist Uncertainty Quantification

Mathematica How To: How to Use the Input Assistant
Learn how to use Mathematica's Input Assistant, which helps you automatically complete code, discover functions and options, and reduce oversights and typographical errors while coding. To learn more about the Input Assistant, please visit: http://www.wolfram.com/mathematica/new-in-9/con
From playlist Getting Started with Mathematica 9

Sensitivity Analysis for Financial Models in Excel
If you like this video, drop a comment, give it a thumbs up and consider subscribing here: https://www.youtube.com/c/HowToBeAnAdult?sub_confirmation=1 Music from: YouTube Audio Library Check out our new project: https://magnimetrics.com The Online Platform for Automated Analysis Random
From playlist Excel Tutorials

Differentially Private Algorithms: Some Primitives and Paradigms - Kunal Talwar
Differential Privacy Symposium: Four Facets of Differential Privacy Saturday, November 12, 2016 https://www.ias.edu/differential-privacy More videos on http://video.ias.edu
From playlist Differential Privacy Symposium - November 12, 2016
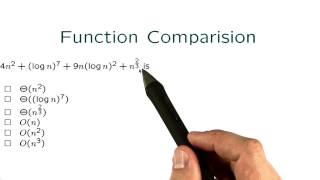
Function Comparision - Intro to Algorithms
This video is part of an online course, Intro to Algorithms. Check out the course here: https://www.udacity.com/course/cs215.
From playlist Introduction to Algorithms

Covariance-Aware Private Mean Estimation Without Private Covariance Estimation
A Google TechTalk, presented by Lydia Zakynthinou, 2021/11/3 Privacy in MLSeminars - ABSTRACT: We present two differentially private mean estimators for multivariate (sub)Gaussian distributions with unknown covariance. Our estimators are accurate with respect to the Mahalanobis loss and
From playlist Differential Privacy for ML
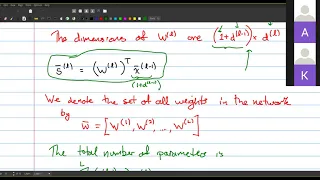
Neural Networks: Forward and Back propagation
From playlist MachineLearning

CERIAS Security: Safely Analyzing Sensitive Network Data 3/6
Clip 3/6 Speaker: Gerome Miklau · University of Massachusetts, Amherst Our recent work investigates the properties of a network that can be accurately studied without threatening the privacy of individuals and their connections. We adopt the rigorous condition of differential privacy, an
From playlist The CERIAS Security Seminars 2009

A short tutorial on differential privacy: Dr Borja Balle, Amazon Research
Differential privacy is a robust mathematical framework for designing privacy-preserving computations on sensitive data. In this tutorial we will cover the key definitions and intuitions behind differential privacy and introduce the core building blocks used by most differentially private
From playlist Turing Seminars

Differentially Private Multi-party Data Release for Linear Regression
A Google TechTalk, presented by Ruihan Wu, 2022/08/31 Differential Privacy for ML Series.
From playlist Differential Privacy for ML

Recent progress in query complexity I & II - Pei Wu
Computer Science/Discrete Mathematics Seminar II Topic: Recent progress in query complexity I & II Speaker: Pei Wu Affiliation: Member, School of Mathematics Date: October 5, 2021 The query model is one of the most basic computational models. In contrast to the Turing machine model, fu
From playlist Mathematics

DeepMind x UCL | Deep Learning Lectures | 8/12 | Attention and Memory in Deep Learning
Attention and memory have emerged as two vital new components of deep learning over the last few years. This lecture by DeepMind Research Scientist Alex Graves covers a broad range of contemporary attention mechanisms, including the implicit attention present in any deep network, as well a
From playlist Learning resources

!!Con 2017: Finding Friends in High Dimensions... by Aaron Levin
Finding Friends in High Dimensions: Locality-Sensitive Hashing For Fun and Friendliness! by Aaron Levin
From playlist !!Con 2017

Private Algorithms with Minimal Space
A Google TechTalk, 2020/7/29, presented by Adam Smith, Boston University ABSTRACT: We show that a classic algorithm for counting distinct elements in small space is differentially private with only small modifications. The result is an algorithm with the same space guarantee as in the nonp
From playlist 2020 Google Workshop on Federated Learning and Analytics
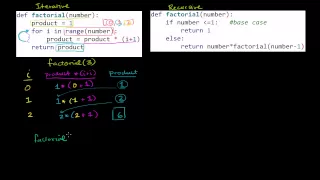
Comparing Iterative and Recursive Factorial Functions
Comparing iterative and recursive factorial functions
From playlist Computer Science
