
One Time Pad - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

This video introduces big strings and provides the formulas need to determine the total number of n-bit strings and how to determine the number of n-bit strings with a given weight.
From playlist Counting (Discrete Math)
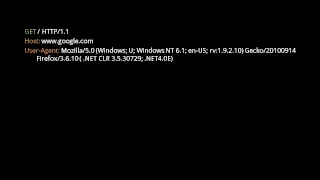
An intro to the core protocols of the Internet, including IPv4, TCP, UDP, and HTTP. Part of a larger series teaching programming. See codeschool.org
From playlist The Internet
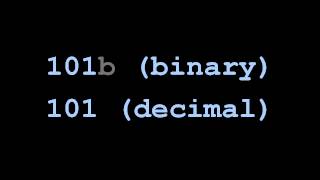
How we represent numbers in computers. Part of a larger series teaching programming. Visit codeschool.org Twitter: @brianwill
From playlist Numbers as bits

In this video, you’ll learn more about using Messages in LinkedIn. Visit https://edu.gcfglobal.org/en/linkedin/keeping-up-with-linkedin/1/ for our text-based lesson. We hope you enjoy!
From playlist LinkedIn

Ex: Linear Equation Application with One Variable - Number Problem
This video provides and example of how to solve a number problem using a linear equation with one variable. One number is a multiple of the other. The difference is a constant. Find the two numbers. Library: http://mathispower4u.com Search: http://mathispower4u.wordpress.com
From playlist Whole Number Applications

How To Add and Subtract Binary Numbers
This video explains how to add and subtract binary numbers. The full version of this video contains extra examples of subtracting, multiplying, and dividing binary numbers. Full 43 Minute Video: https://www.youtube.com/watch?v=eAdWDu3s8xM
From playlist Number Systems
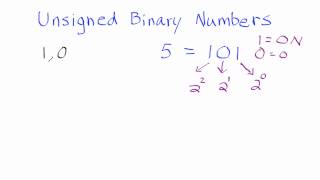
1. Unsigned Binary Numbers - How to Convert From Unsigned Binary Numbers to Whole Numbers
This tutorial shows how to convert from an unsigned binary number to a whole number. Join this channel to get access to perks: https://www.youtube.com/channel/UCn2SbZWi4yTkmPUj5wnbfoA/join :)
From playlist Binary Numbers

Definition, horizontal line test, and examples! Facebook: https://www.facebook.com/braingainzofficial Instagram: https://www.instagram.com/braingainzofficial Thanks for watching! Comment below with any questions / feedback and make sure to like / subscribe if you enjoyed!
From playlist Precalculus
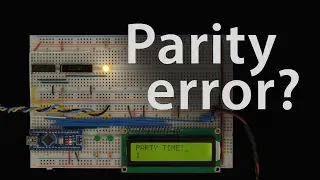
Error detection: Parity checking
Parity checking is a basic technique for detecting errors in data transmission. This video explains how it works and walks through building hardware to compute and check parity. The hardware is based on my previous video: https://youtu.be/eq5YpKHXJDM Code from this video: https://github.
From playlist Error detection
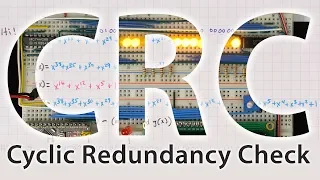
CRC (cyclic redundancy check) is one of the most common methods of error detection. It uses some interesting mathematical tricks to guarantee that it can catch certain kinds of errors. How does it work? Support these videos on Patreon: https://www.patreon.com/beneater or https://eater.net
From playlist Error detection

Jonathan Katz - Introduction to Cryptography Part 1 of 3 - IPAM at UCLA
Recorded 25 July 2022. Jonathan Katz of the University of Maryland presents "Introduction to Cryptography I" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: This lecture will serve as a "crash course" in modern cryptography for those with no prior exposure
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

The History of Cryptography: Block Cyphers, Stream Cyphers, Public Keys and more!
Alice and Bob have secrets they want to talk about without Eve being able to listen in. Worse yet, the mischievous Mallory delights in changing messages sent between parties. In such a hostile environment how can Alice talk to Bob without their messages being overheard and how can she be
From playlist Talks

Lec 22 | MIT 6.033 Computer System Engineering, Spring 2005
Authentication View the complete course at: http://ocw.mit.edu/6-033S05 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.033 Computer System Engineering, Spring 2005

Stanford Seminar - Bugs in Crypto Implementations
Whether it’s by email, text, or social media platform, the average person will send over 60 messages per day—that's 22,000 messages per year. With billions of messages sent around the world each day, how can you be sure that your messages are safe and secure? Join professor Dan Boneh, on
From playlist Stanford Seminars

Lecture 32: Steganography (hidden messages) - Richard Buckland UNSW
Extension lecture introducing steganography (hidden messages). Security via obscurity. Hidden messages in book Godel Escher Bach. In film Starship Troopers. In games. In cryptography. In teaching. Digital watermarking. SETI. Are we in a simulation? Extension lectures are for firs
From playlist CS1: Higher Computing - Richard Buckland UNSW

Apollo Comms Part 14: Sending Commands to the Spacecraft
Our sponsor PCBWay: fast turn PCBs, https://www.pcbway.com We send digital commands to the spacecraft. We can even hear how they sound! Apollo Comms Playlist: https://www.youtube.com/watch?v=v49ucdZcx9s&list=PL-_93BVApb58SXL-BCv4rVHL-8GuC2WGb Chapters: 0:00 Intro 2:10 Ken's automated rev
From playlist Space Hardware

Lec 10 | MIT 6.033 Computer System Engineering, Spring 2005
Layering and Link Layer View the complete course at: http://ocw.mit.edu/6-033S05 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.033 Computer System Engineering, Spring 2005

From playlist Week 0 2015 Shorts

NOTACON 2: Recent Attacks Against Hash Functions
Speaker: Matthew Fanto In recent months, a large amount of research into the security of cryptographic hash functions has revealed serious flaws in every widely used hash function, including MD4, MD5, RIPEMD, HAVAL, SHA-0, and SHA-1. These flaws have far reaching consequences, as hash fun
From playlist Notacon 2