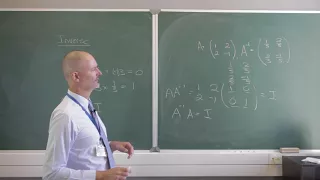
The inverse of a matrix is a similarly sized matrix such that the multiplication of the two matrices results in the identity matrix. In this video we look at an example of this. You can learn more about Mathematica on my Udemy course at https://www.udemy.com/mathematica/ PS! Wait until
From playlist Introducing linear algebra

In this video we finish with three more example of calculating the null space of a matrix. These three example help us gain an even deeper insight into the null space by consider how many special cases we will get. Remember that the linear combinations of the special cases give us the nu
From playlist Introducing linear algebra

Secure computation with RAMs - Dr Mariana Raykova, Yale University
Secure computation with RAMs: revisiting square root ORAM and low leakage secure Boolean queries Hiding memory access patterns is required for secure computation, but remains prohibitively expensive for many interesting applications. This talk presents two works addressing this question:
From playlist Turing Seminars

This shows an interactive illustration that explains that parallel vectors can have either the same or opposite directions. The clip is from the book "Immersive Linear Algebra" at http://www.immersivemath.com
From playlist Chapter 2 - Vectors

NES Emulator Part #3: Buses, RAMs, ROMs & Mappers
In this video I explain how I've "glued" together the different components of my NES emulation, looking at how the cartridge is loaded, and how the CPU and other devices interact with each other in a flexible way, through the use of Mappers. Source: https://github.com/OneLoneCoder/olcNES
From playlist NES Emulator From Scratch

Determine if the Vectors are Orthogonal
Please Subscribe here, thank you!!! https://goo.gl/JQ8Nys Determine if the Vectors are Orthogonal
From playlist Calculus

Lec 24 | MIT 6.046J / 18.410J Introduction to Algorithms (SMA 5503), Fall 2005
Lecture 24: Advanced Topics (cont.) View the complete course at: http://ocw.mit.edu/6-046JF05 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.046J / 18.410J Introduction to Algorithms (SMA 5503),

O'Reilly MySQL CE 2010: Bradley C. Kuszmaul, "What is a Performance Model for SSDs?"
Bradley C. Kuszmaul (Tokutek), "What is a Performance Model for SSDs?"
From playlist O'Reilly MySQL Conference & Expo 2010

iPhone Forensics: Bypassing the iPhone Passcode - O'Reilly Webcast
In this video from a live webcast, iPhone hacker and data forensics expert Jonathan Zdziarski guides you through the steps used by law enforcement agencies to bypass the iPhone 3G's passcode lock by creating a custom firmware bundle. Author of the upcoming book, iPhone Forensics, Jonathan
From playlist iPhone - Hacking, Development, Forensics, Tool Chain

Bitcoin Q&A: What is the Role of Nodes?
The role that full nodes play in security of the network. People focus a lot on mining, which has a fundamental role in the network but is not necessarily the most interesting feature of the constellation of technologies involved. The Border Gateway Protocol (BGP) is the most essential pro
From playlist Bitcoin Q&A

Inverse matrices | Lecture 6 | Matrix Algebra for Engineers
Definition of an inverse matrix. Computation of the inverse of a two-by-two matrix. Join me on Coursera: https://www.coursera.org/learn/matrix-algebra-engineers Lecture notes at http://www.math.ust.hk/~machas/matrix-algebra-for-engineers.pdf Subscribe to my channel: http://www.youtube
From playlist Matrix Algebra for Engineers

Some Secure Computation concepts by Manoj Prabhakaran
DISCUSSION MEETING : FOUNDATIONAL ASPECTS OF BLOCKCHAIN TECHNOLOGY ORGANIZERS : Pandu Rangan Chandrasekaran DATE : 15 to 17 January 2020 VENUE : Madhava Lecture Hall, ICTS, Bangalore Blockchain technology is among one of the most influential disruptive technologies of the current decade.
From playlist Foundational Aspects of Blockchain Technology 2020
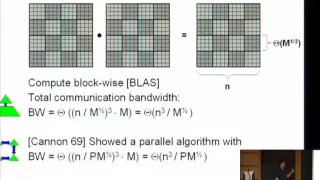
Expanders and Communication-Avoiding Algorithms - Oded Schwartz
Oded Schwartz Technical University Berlin January 25, 2010 Algorithms spend time on performing arithmetic computations, but often more on moving data, between the levels of a memory hierarchy and between parallel computing entities. Judging by the hardware evolution of the last few decades
From playlist Mathematics

Dynamic Graph Algorithms and Their Implementation
Abstract: While many algorithmic graph problems have been solved for static graphs, graphs that are used as models in various applications often change dynamically and, thus, require algorithms that can adapt quickly to the deletion and insertion of edges. I will start with providing an ov
From playlist SIAG-ACDA Online Seminar Series

Finding the inverse of a 2x2 matrix
In this video I show you one method of calculating the inverse of a square matrix. We can use this inverse to solve for a system of linear equations. Mathematica has a function called Inverse that easily calculates the inverse of a matrix. You can learn more about Mathematica on my Udem
From playlist Introducing linear algebra
This shows an small game that illustrates the concept of a vector. The clip is from the book "Immersive Linear Algebra" at http://www.immersivemath.com
From playlist Chapter 2 - Vectors

This shows an interactive illustration that explains equivalent vectors. The clip is from the book "Immersive Linear Algebra" at http://www.immersivemath.com
From playlist Chapter 2 - Vectors

An Almost-Linear-Time Algorithm for Approximate Max Flow in Undirected Graphs... - Jonathan Kelner
Jonathan Kelner Massachusetts Institute of Technology February 24, 2014 In this talk, I will describe a new framework for approximately solving flow problems in capacitated, undirected graphs, and I will apply it to find approximately maximum s-t flows in almost-linear time, improving on t
From playlist Mathematics

The Empty Set or the Null Set , Intermediate Algebra , Lesson 27
This tutorial explains the simple concept of the empty set, otherwise known as the null set. Join this channel to get access to perks: https://www.youtube.com/channel/UCn2SbZWi4yTkmPUj5wnbfoA/join :)
From playlist Intermediate Algebra