
A14 Nonhomegeneous linear systems solved by undetermined coefficients
There are two methods for solving nonhomogeneous systems. The first uses undetermined coefficients.
From playlist A Second Course in Differential Equations

NP: How Non-determinism Relates to Verifiable Proofs
There are multiple, surprisingly different, ways to think of NP problems. Let's talk about these different definitions and why they're equivalent. Created by: Cory Chang Produced by: Vivian Liu Script Editor: Justin Chen, Zachary Greenberg, Elaine Chang Twitter: https://twitter.com/UBeha
From playlist P vs NP

Lecture 12A : The Boltzmann Machine learning algorithm
Neural Networks for Machine Learning by Geoffrey Hinton [Coursera 2013] Lecture 12A : The Boltzmann Machine learning algorithm
From playlist Neural Networks for Machine Learning by Professor Geoffrey Hinton [Complete]

Samuel Fiorini: Integer programs with bounded subdeterminants and two nonzeros per row
We give a strongly polynomial-time algorithm for integer linear programs defined by integer coefficient matrices whose subdeterminants are bounded by a constant and that contain at most two nonzero entries in each row. The core of our approach is the first polynomial-time algorithm for the
From playlist Workshop: Parametrized complexity and discrete optimization

Theory of Computation 8. CFGs and NPDMs ADUni
From playlist [Shai Simonson]Theory of Computation
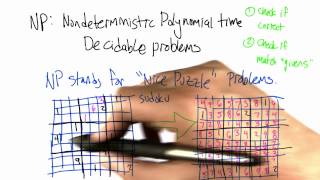
Non-deterministic Polynomial Time Decidable Problem - Intro to Algorithms
This video is part of an online course, Intro to Algorithms. Check out the course here: https://www.udacity.com/course/cs215.
From playlist Introduction to Algorithms

What is the negation of a statement and examples
👉 Learn how to find the negation of a statement. The negation of a statement is the opposite of the statement. It is the 'not' of a statement. If a statement is represented by p, then the negation is represented by ~p. For example, The statement "It is raining" has a negation of "It is not
From playlist Negation of a Statement

Determining the negation of a hypothesis and conclusion from a statement
👉 Learn how to find the negation of a statement. The negation of a statement is the opposite of the statement. It is the 'not' of a statement. If a statement is represented by p, then the negation is represented by ~p. For example, The statement "It is raining" has a negation of "It is not
From playlist Negation of a Statement

Non-negatively Weighted #CSPs: An Effective Complexity Dichotomy - Xi Chen
Xi Chen Columbia University March 28, 2011 We prove a complexity dichotomy theorem for all non-negatively weighted counting Constraint Satisfaction Problems (#CSP). This caps a long series of important results on counting problems including unweighted and weighted graph homomorphisms and t
From playlist Mathematics

Cyber Security Week Day - 1 |Cryptography Full Course | Cryptography & Network Security| Simplilearn
🔥Advanced Executive Program In Cybersecurity: https://www.simplilearn.com/pgp-advanced-executive-program-in-cyber-security 🔥Caltech Cybersecurity Bootcamp(US Only): https://www.simplilearn.com/cybersecurity-bootcamp This video on Cryptography full course will acquaint you with cryptograph
From playlist Simplilearn Live

Cryptography Full Course | Cryptography And Network Security | Cryptography | Simplilearn
🔥Advanced Executive Program In Cybersecurity: https://www.simplilearn.com/pgp-advanced-executive-program-in-cyber-security?utm_campaign=CryptographyFCAug17&utm_medium=DescriptionFirstFold&utm_source=youtube 🔥Caltech Cybersecurity Bootcamp(US Only): https://www.simplilearn.com/cybersecurity
From playlist Simplilearn Live

Thresholds in Recovery of Sparse Stochastic Block Models by Allan Sly
COLLOQUIUM THRESHOLDS IN RECOVERY OF SPARSE STOCHASTIC BLOCK MODELS SPEAKER: Allan Sly ( Princeton University) DATE: Wed, 13 February 2019, 15:00 to 16:00 VENUE: Madhava Lecture Hall, ICTS Campus, Bangalore RESOURCES ABSTRACT The stochastic block model is an inhomogeneous random gra
From playlist ICTS Colloquia

🔥Cryptography And Network Security Full Course 2022 | Cryptography | Network Security | Simplilearn
🔥Free Cyber Security Course With Completion Certificate: https://www.simplilearn.com/learn-cyber-security-basics-skillup?utm_campaign=CryptographyNetworkSecurityFC4Aug22&utm_medium=DescriptionFirstFold&utm_source=youtube This video on the Cryptography and network security full course will
From playlist Simplilearn Live

Top Hashing Algorithms In Cryptography | MD5 and SHA 256 Algorithms Explained | Simplilearn
In this video on Top Hashing Algorithms In Cryptography, we will cover the technical aspects of hashing while going through some well-known hash functions and algorithms at the end. We cover the basics of cryptography and its applications. We also have detailed MD5 and SHA265 Explained sec
From playlist Cyber Security Playlist [2023 Updated]🔥

Chao Yang - Practical Quantum Circuits for Block Encodings of Sparse Matrices - IPAM at UCLA
Recorded 27 January 2022. Chao Yang of Lawrence Berkeley National Laboratory presents "Practical Quantum Circuits for Block Encodings of Sparse Matrices" at IPAM's Quantum Numerical Linear Algebra Workshop. Abstract: Many standard linear algebra problems can be solved on a quantum computer
From playlist Quantum Numerical Linear Algebra - Jan. 24 - 27, 2022

Cyber Security Interview Questions Part - 5 | Cryptography Interview Questions | Simplilearn
This video on cybersecurity interview questions part 5 focuses on questions from cryptography. This video will walk you through several questions related to encryption, decryption, public key infrastructure, and many more. 🔥Enroll for Free Cyber Security Course & Get Your Completion Certif
From playlist Cyber Security Playlist [2023 Updated]🔥

Algorithmic invariant theory - Visu Makam
Optimization, Complexity and Invariant Theory Topic: Algorithmic invariant theory Speaker: Visu Makam Affiliation: University of Michigan Date: June 6. 2018 For more videos, please visit http://video.ias.edu
From playlist Mathematics

From playlist k-Nearest Neighbor Algorithm

Factorization-based Sparse Solvers and Preconditions, Lecture 4
Xiaoye Sherry Li's (from Lawrence Berkeley National Laboratory) lecture number four on Factorization-based sparse solves and preconditioners
From playlist Gene Golub SIAM Summer School Videos
