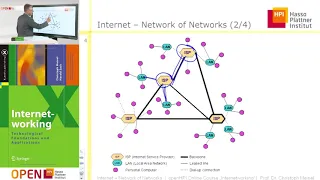
From playlist Communications & Network Systems

An intro to the core protocols of the Internet, including IPv4, TCP, UDP, and HTTP. Part of a larger series teaching programming. See codeschool.org
From playlist The Internet
Computer Literacy - (unit 4) - the internet - 1 of 4
Forth unit of a series for newbie computer users. See http://proglit.com/computer-skills/ for additional information and material.
From playlist Computer Literacy - (unit 4) - the internet

Computer Literacy - (unit 4) - the internet - 2 of 4
Forth unit of a series for newbie computer users. See http://proglit.com/computer-skills/ for additional information and material.
From playlist Computer Literacy - (unit 4) - the internet

An intro to the core protocols of the Internet, including IPv4, TCP, UDP, and HTTP. Part of a larger series teaching programming. See codeschool.org
From playlist The Internet

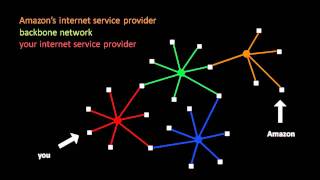
We're busy people who learn to code, then practice by building projects for nonprofits. Learn Full-stack JavaScript, build a portfolio, and get great references with our open source community. Join our community at https://freecodecamp.com Follow us on twitter: https://twitter.com/freecod
From playlist Networks
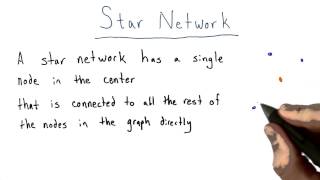
Star Network - Intro to Algorithms
This video is part of an online course, Intro to Algorithms. Check out the course here: https://www.udacity.com/course/cs215.
From playlist Introduction to Algorithms

Network Security, Part 1 : Basic Encryption Techniques
Fundamental concepts of network security are discussed. It provides a good overview of secret Key and public key Encryption. Important data encryption standards are presented.
From playlist Network Security

MIT 6.02 Introduction to EECS II: Digital Communication Systems, Fall 2012 View the complete course: http://ocw.mit.edu/6-02F12 Instructor: Hari Balakrishnan This lecture focuses on shared media networks and shared communications channels. Measures for optimization such as utilization, fa
From playlist MIT 6.02 Introduction to EECS II: Digital Communication Systems, Fall 2012

Lec 8 | MIT 6.033 Computer System Engineering, Spring 2005
Performance View the complete course at: http://ocw.mit.edu/6-033S05 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.033 Computer System Engineering, Spring 2005

23C3: How to squeeze more performance out of your wifi
Speaker: Achim Friedland Cross-layer optimization strategies for long-range IEEE 802.11e based radio (mesh) networks Most of today's long-range wireless mesh or point-to-point links suffer from a high overhead during channel access, frequent link failtures and the lack of taking a real
From playlist 23C3: Who can you trust

Increasing AI productivity and efficiency (sponsored by Habana Labs) - Eitan Medina
Eitan Medina details transformational advances made possible with AI processors designed from the ground up to address AI-specific computing requirements, chief among them increasing AI throughput speeds while lowering power consumption. This new class of AI processing brings significantly
From playlist The O'Reilly Artificial Intelligence Conference 2019, Beijing, China

CERIAS Security: Exploiting Opportunistic Scheduling in Cellular Data Networks 4/5
Clip 4/5 Speaker: Hao Chen · Assistant Professor · University of California, Davis Third Generation (3G) cellular networks utilize time-varying and location-dependent channel conditions to provide broadband services. They employ opportunistic scheduling to efficiently utilize spectrum un
From playlist The CERIAS Security Seminars 2008

CERIAS Security: Exploiting Opportunistic Scheduling in Cellular Data Networks 1/5
Clip 1/5 Speaker: Hao Chen · Assistant Professor · University of California, Davis Third Generation (3G) cellular networks utilize time-varying and location-dependent channel conditions to provide broadband services. They employ opportunistic scheduling to efficiently utilize spectrum un
From playlist The CERIAS Security Seminars 2008

GRCon20 - Data Streaming from SDR to Servers for Cognitive Radar and EW
Presented by Abhay Samant and David Asplund at GNU Radio Conference 2020 https://gnuradio.org/grcon20 GPUs are becoming increasingly popular as the compute platform for digital signal processing algorithms in cognitive radar and EW applications. Traditionally, it has been challenging to c
From playlist GRCon 2020

22. Sliding window analysis, Little's law
MIT 6.02 Introduction to EECS II: Digital Communication Systems, Fall 2012 View the complete course: http://ocw.mit.edu/6-02F12 Instructor: Hari Balakrishnan This lecture continues with an analysis of sliding window protocol and how it handles packet loss. Little's Law is introduced to re
From playlist MIT 6.02 Introduction to EECS II: Digital Communication Systems, Fall 2012

MIT 6.02 Introduction to EECS II: Digital Communication Systems, Fall 2012 View the complete course: http://ocw.mit.edu/6-02F12 Instructor: Hari Balakrishnan This lecture covers implementation of TCP and providing reliable data transfer. The stop-and-wait and sliding window protocols are
From playlist MIT 6.02 Introduction to EECS II: Digital Communication Systems, Fall 2012

Yafeng Yin: "Rhythmic Traffic Management and Control in Fully Automated Vehicle Environment"
Mathematical Challenges and Opportunities for Autonomous Vehicles 2020 Workshop III: Large Scale Autonomy: Connectivity and Mobility Networks "Rhythmic Traffic Management and Control in Fully Automated Vehicle Environment" Yafeng Yin - University of Michigan Abstract: In this talk, we pr
From playlist Mathematical Challenges and Opportunities for Autonomous Vehicles 2020