National Institute of Cryptology Research and Development
National Institute of Cryptology Research and Development (NICRD) is a national-level research center for cryptologic education and research. (Wikipedia).
National Institute of Cryptology Research and Development (NICRD) is a national-level research center for cryptologic education and research. (Wikipedia).

Few other Cryptanalytic Techniques
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Cryptanalysis of Classical Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security
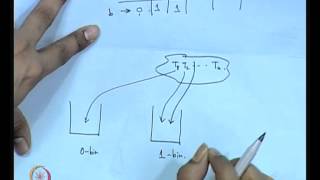
Side Channel Analysis of Cryptographic Implementations
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Overview on Modern Cryptography
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Some Comments on the Security of RSA
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

What Is the Future of Cryptography?
Historically, as advances were made in the fields of engineering, mathematics, and physics, so the field of cryptography has advanced with them—usually by leaps and bounds. Where is it headed next? Science journalist Simon Singh concedes that the science of secrecy tends to be secret, so w
From playlist Technology

Computer History "Engineering Research Associates" ERA 1101, UNIVAC, Cryptology, 1946 Sperry Rand
Vintage Computer History; Cryptology; Navy Intelligence: This unique presentation provides an introduction to the origin and history of ENGINEERING RESEARCH ASSOCIATES (“ERA”) a pioneering and influential computer company founded in Minnesota in 1946. Formed and staffed by former members
From playlist Computer History: UNIVAC, Remington Rand, Sperry Rand

Overview on S-Box Design Principles
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Computer History: Origin of the UNIVAC 1103A Scientific Computer (1953, 1956) ERA, Sperry Rand
UNIVAC: This presentation explores the history of the UNIVAC 1103A SCIENTIFIC COMPUTER, the most powerful scientific computer of its time. Used by the U.S. Navy, Air Force, National Security Agency, NASA and many others. Rare films and high quality photos show the development of the mach
From playlist Computer History: UNIVAC, Remington Rand, Sperry Rand

Lecture - 32 Basic Cryptographic Concepts Part : I
Lecture Series on Internet Technologies by Prof.I.Sengupta, Department of Computer Science & Engineering ,IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Cryptography, Security

Group Theory for Cryptology by Carlo Scoppola
PROGRAM GROUP ALGEBRAS, REPRESENTATIONS AND COMPUTATION ORGANIZERS: Gurmeet Kaur Bakshi, Manoj Kumar and Pooja Singla DATE: 14 October 2019 to 23 October 2019 VENUE: Ramanujan Lecture Hall, ICTS Bangalore Determining explicit algebraic structures of semisimple group algebras is a fund
From playlist Group Algebras, Representations And Computation

DeepSec 2010: Mobile VoIP Steganography: From Framework to Implementation
Thanks to the DeepSec organisation for making these videos available and let me share the videos on YouTube. Speakers: Rainer Poisel | Marcus Nutzinger, Institute of IT Security Research, St. Polten University of Applied Sciences, Austria The need for steganography has arisen from scenar
From playlist DeepSec 2010

Election Technology: Voting by App in 2020?
For many, the next step in election technology is online voting. But is it safe? The issues surrounding online voting encompass all the aspects of secure cryptography: encryption, integrity, privacy, and nonrepudiation. Is my message secret? Is it my message? Do the pollers know to check m
From playlist Technology

Computer History: PHILCO TRANSAC 2000 Mainframe (NORAD, NASA, SOLO, Philco-Ford)
A brief introduction to PHILCO and its early computers: Through vintage films & photos we explore some memorable product developments at PHILCO. Although we barely scratch the surface of PHILCO’s many achievements, this may bring back some fond memories for former PHILCO and Philco-Ford
From playlist Computer History: RCA, PHILCO, GE

Keeping Secrets: Cryptography In A Connected World
Josh Zepps, Simon Singh, Orr Dunkelman, Tal Rabin, and Brian Snow discuss how, since the earliest days of communication, clever minds have devised methods for enciphering messages to shield them from prying eyes. Today, cryptography has moved beyond the realm of dilettantes and soldiers to
From playlist Explore the World Science Festival

A Tour of Bitcoin, Blockchains, Attacks and More.. by Sushmita Ruj
DISCUSSION MEETING : FOUNDATIONAL ASPECTS OF BLOCKCHAIN TECHNOLOGY ORGANIZERS : Pandu Rangan Chandrasekaran DATE : 15 to 17 January 2020 VENUE : Madhava Lecture Hall, ICTS, Bangalore Blockchain technology is among one of the most influential disruptive technologies of the current decade.
From playlist Foundational Aspects of Blockchain Technology 2020

Panel Discussion on Predictions for FinTech & Asset Management
National Meeting of Women in Financial Mathematics Panel Discussion on Predictions for FinTech & Asset Management - Karyn Williams: Two Sigma Investments - panel chair - Darcy Pauken: Western Asset Management - Anjun Zhou: Mellon Capital - Tanya Beder: SBCC Group Inc. & IPAM Trustee Inst
From playlist National Meeting of Women in Financial Mathematics 2017

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

DEFCON 20: The Christopher Columbus Rule and DHS
Speaker: MARK WEATHERFORD DEPUTY UNDERSECRETARY FOR CYBERSECURITY FOR THE NATIONAL PROTECTION AND PROGRAMS DIRECTORATE (NPPD) AT THE UNITED STATES DEPARTMENT OF HOMELAND SECURITY. "Never fail to distinguish what's new, from what's new to you." This rule applies to a lot people when they t
From playlist DEFCON 20