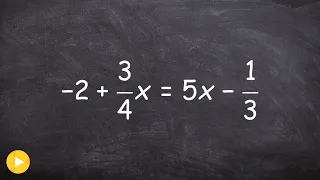
Solve an equation for x by clearing fractions with multiple steps
👉 Learn how to solve multi-step equations with variable on both sides of the equation. An equation is a statement stating that two values are equal. A multi-step equation is an equation which can be solved by applying multiple steps of operations to get to the solution. To solve a multi-s
From playlist How to Solve Multi Step Equations with Variables on Both Sides

Solving an equation with variables on both side and one solution
👉 Learn how to solve multi-step equations with variable on both sides of the equation. An equation is a statement stating that two values are equal. A multi-step equation is an equation which can be solved by applying multiple steps of operations to get to the solution. To solve a multi-s
From playlist Solve Multi-Step Equations......Help!
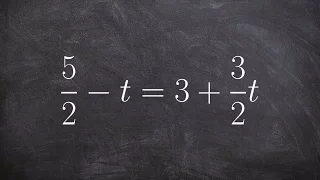
Solving a multi-step equation by multiplying by the denominator
👉 Learn how to solve multi-step equations with variable on both sides of the equation. An equation is a statement stating that two values are equal. A multi-step equation is an equation which can be solved by applying multiple steps of operations to get to the solution. To solve a multi-s
From playlist How to Solve Multi Step Equations with Variables on Both Sides
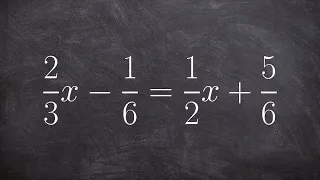
Solving a multi-step equation with fractions and variable on both sides
👉 Learn how to solve multi-step equations with variable on both sides of the equation. An equation is a statement stating that two values are equal. A multi-step equation is an equation which can be solved by applying multiple steps of operations to get to the solution. To solve a multi-s
From playlist How to Solve Multi Step Equations with Variables on Both Sides
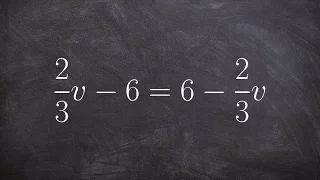
How to solve a multi step equation with fractions
👉 Learn how to solve multi-step equations with variable on both sides of the equation. An equation is a statement stating that two values are equal. A multi-step equation is an equation which can be solved by applying multiple steps of operations to get to the solution. To solve a multi-s
From playlist How to Solve Multi Step Equations with Variables on Both Sides

Black Hat USA 2010: WPA Migration Mode: WEP is Back to Haunt You 1/4
Speakers: Leandro Meiners, Diego Sor Cisco access points support WPA migration mode, which enables both WPA and WEP clients to associate to an access point using the same Service Set Identifier (SSID). If WEP clients are still around, we can use the traditional WEP cracking arsenal agains
From playlist BH USA 2010 - NETWORK
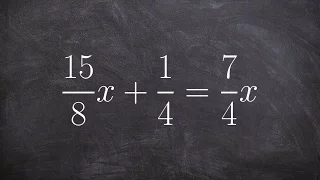
Solving an equation with fraction where your variable is on both sides
👉 Learn how to solve multi-step equations with variable on both sides of the equation. An equation is a statement stating that two values are equal. A multi-step equation is an equation which can be solved by applying multiple steps of operations to get to the solution. To solve a multi-s
From playlist How to Solve Multi Step Equations with Variables on Both Sides

What is Man-in-the-Middle Attack | MITM Attack Explained | Edureka | Cybersecurity Rewind - 4
🔥Edureka Cyber Security Course: https://www.edureka.co/cybersecurity-certification-training This Edureka video on "What is Man-in-the-Middle Attack" will help you understand what is Man-in-the-Middle Attack and how you can prevent it. Cybersecurity Training Playlist: https://bit.ly/2NqcTQ
From playlist Edureka Live Classes 2020

Cybersecurity Tutorial | Demo On Man In The Middle Attack | Cybersecurity Training | Edureka
🔵Edureka Cyber Security Masters Program: https://bit.ly/3pfHHIN 🔥Edureka CompTIA Security+ Certification Training: https://bit.ly/3nxeVRl This "Cybersecurity tutorial" video presented by edureka gives an indepth information about the Cyber Security world and talks about its basic concepts.
From playlist Cyber Security Training for Beginners | Edureka

RailsConf 2019 - Automate your Home with Ruby by Karl Entwistle
RailsConf 2019 - Automate your Home with Ruby by Karl Entwistle _______________________________________________________________________________________________ Cloud 66 - Pain Free Rails Deployments Cloud 66 for Rails acts like your in-house DevOps team to build, deploy and maintain your
From playlist RailsConf 2019

Top 10 Networking Interview Questions And Answers | Networking Interview Preparation | Simplilearn
🔥Advanced Executive Program In Cybersecurity: https://www.simplilearn.com/pgp-advanced-executive-program-in-cyber-security?utm_campaign=NetworkingIQsMar28-N1dAIFGakxY&utm_medium=Descriptionff&utm_source=youtube 🔥Caltech Cybersecurity Bootcamp(US Only): https://www.simplilearn.com/cybersecu
From playlist Cyber Security Playlist [2023 Updated]🔥

Black Hat USA 2010: WPA Migration Mode: WEP is Back to Haunt You 2/4
Speakers: Leandro Meiners, Diego Sor Cisco access points support WPA migration mode, which enables both WPA and WEP clients to associate to an access point using the same Service Set Identifier (SSID). If WEP clients are still around, we can use the traditional WEP cracking arsenal agains
From playlist BH USA 2010 - NETWORK

22C3: Attacking the IPv6 Protocol Suite
Speaker: van Hauser After a short introduction on the differences of IPv4 to IPv6, the weaknesses in IPv6 will be shown. Highlight of the talk is the presentation of the THC-IPV6 Attack Toolkit, which includes all IPv6 attacks as well as a low level packet library for easy crafting packet
From playlist 22C3: Private Investigations
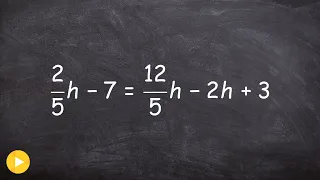
How to solve multi step equations with fractional coefficients
👉 Learn how to solve multi-step equations with variable on both sides of the equation. An equation is a statement stating that two values are equal. A multi-step equation is an equation which can be solved by applying multiple steps of operations to get to the solution. To solve a multi-s
From playlist How to Solve Multi Step Equations with Variables on Both Sides

Local linearity for a multivariable function
A visual representation of local linearity for a function with a 2d input and a 2d output, in preparation for learning about the Jacobian matrix.
From playlist Multivariable calculus

Solving an equation with variables on both sides no solution
👉 Learn how to solve multi-step equations with variable on both sides of the equation. An equation is a statement stating that two values are equal. A multi-step equation is an equation which can be solved by applying multiple steps of operations to get to the solution. To solve a multi-s
From playlist How to Solve Multi Step Equations with Variables on Both Sides

27c3: Recent advances in IPv6 insecurities (en)
Speaker: vanHauser New protocol features have been proposed and implemented in the last 5 years and ISPs are now slowly starting to deploy IPv6. This talk starts with a brief summary of the issues presented five years ago, and then expands on the new risks. Discovered implemention secu
From playlist 27C3: We come in peace

27c3: Recent advances in IPv6 insecurities
Speaker: vanHauser New protocol features have been proposed and implemented in the last 5 years and ISPs are now slowly starting to deploy IPv6. This talk starts with a brief summary of the issues presented five years ago, and then expands on the new risks. Discovered implemention securit
From playlist 27C3: We come in peace

Clip 1/4 Speaker: Md Sohail Ahmad Manager R&D, AirTight Networks WPA2 is the most robust security configuration available today for WiFi networks. It is widely used to secure enterprise WLANs. Interestingly, it is also being used to secure guest, municipal and public WiFi networks. In
From playlist DEFCON 18-1
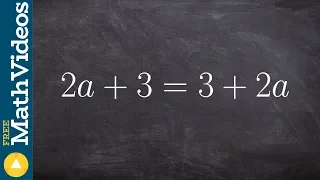
Solving an equation with infinite many solutions 2a+3=3+2a
👉 Learn how to solve multi-step equations with variable on both sides of the equation. An equation is a statement stating that two values are equal. A multi-step equation is an equation which can be solved by applying multiple steps of operations to get to the solution. To solve a multi-s
From playlist How to Solve Multi Step Equations with Variables on Both Sides