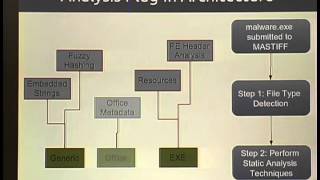
ShmooCon 2013: astiff: Automated Static Analysis Framework
For more information and to download the video visit: http://bit.ly/shmoocon2013 Playlist ShmooCon 2013: http://bit.ly/Shmoo13 Speaker: Tyler Hudak Malware analysis consists of two phases -- static and dynamic analysis. Dynamic analysis, or analyzing the behavior of a sample, has already
From playlist ShmooCon 2013

Malware Analysis Bootcamp - Introduction To Static Analysis
Welcome to the Malware Analysis Bootcamp. We will be covering everything you need to know to get started in Malware Analysis professionally. In this video, we will introduce you to static analysis and the static analysis techniques we will be using. Link to slides: https://docs.google.com
From playlist Malware Analysis

DeepSec 2010: Circumventing common Pitfalls when auditing sourcecode for Security Vulnerabilities
Thanks to the DeepSec organisation for making these videos available and let me share the videos on YouTube. Speakers: Aljosha Judmaier | David White, SEC Consult There comes the time where a true security expert has to look at some source code. Everybody knows that ----real men---- use
From playlist DeepSec 2010

DevOpsDays Baltimore 2018 - Integrating Infrastructure as Code into a Continuous Delivery Pipeline
Integrating Infrastructure as Code into a Continuous Delivery Pipeline by Adarsh Shah & Matthew Kuritz Infrastructure as Code (IaC) is the approach that takes proven coding techniques used by software systems and extends them to infrastructure. It is one of the key DevOps practices that e
From playlist DevOpsDays Baltimore 2018

Malware Analysis Bootcamp - Extracting Strings
Welcome to the Malware Analysis Bootcamp. We will be covering everything you need to know to get started in Malware Analysis professionally. In this video, we will be taking a look at how to extract strings from malware samples, and how they can help us understand the functionality of the
From playlist Malware Analysis

Advanced TypeScript Tooling at Scale
Tooling has always been a focus for TypeScript and a large reason for its success. TypeScript code intelligence is available across many editors and even web-based tools, all provided by the same service TypeScript ships out-of-the-box with the compiler itself. This presentation gives a to
From playlist TypeScript

Write the Docs Portland 2017: Treating Documentation like Code: a Practical Account by Jodie Putrino
Write the Docs 2017: Treating Documentation like Code: a Practical Account by Jodie Putrino Are you interested in developing docs like code? Are you frustrated by the lack of available information as to what that really means and how exactly you're supposed to do it? Welcome to the club!
From playlist Write The Docs 2017

GTAC 2009 - Even Better Than the Real Thing - Lessons Learne
Google Tech Talk October 21, 2009 ABSTRACT Even Better Than the Real Thing - Lessons Learned from Testing GWT Applications. Presented by Nicolas Wettstein at the 4th Annual Google Test Automation Conference, October 21st, 22nd, 2009, Zurich, CH Web applications are hard to write
From playlist GTAC 2009

DEFCON 14: Bridging the Gap Between Static and Dynamic Reversing
Speaker: Luis Miras, Vulnerability Researcher, Intrusion Inc. Abstract: Reverse engineering continues to evolve, or rather REvolve. The reverse engineering toolset primarily consists of disconnected disassemblers and debuggers. Without symbol information or data acquired from disassembly
From playlist DEFCON 14

How to Simulate Multiple Scenarios and Convert Models to Fixed Point | MATLAB & Simulink Developers
The Fixed-Point Tool in Simulink® can automatically explore compression choices to optimize your design based on high-level behavior constraints. The tool also uses multiple scenarios for simulation and verification. In this video, you will learn how the Fixed Point Tool can: combine full
From playlist Tips and Tricks from MATLAB and Simulink Developers

Malware Analysis Bootcamp - Generating Malware Hashes
Welcome to the Malware Analysis Bootcamp. We will be covering everything you need to know to get started in Malware Analysis professionally. In this video, we will be taking a look at what malware hashing is, the importance of malware hashing and the tools that are used for malware hashing
From playlist Malware Analysis

GRCon19 -Striving for SDR Performance Portability in the Era of Heterogeneous SoCs by Jeffrey Vetter
Striving for SDR Performance Portability in the Era of Heterogeneous SoCs by Jeffrey Vetter, Mehmet Belviranli, Seyong Lee, Roberto Gioiosa, Abdel-Kareem Moadi Future heterogeneous DSSoCs will be extraordinarily complex in terms of processors, memory hierarchies, and interconnection netwo
From playlist GRCon 2019

OWASP AppSecUSA 2012: The Magic of Symbiotic Security: Creating an Ecosystem of Security Systems
Speakers: Dan Cornell and Josh Sokol Throw out everything that you know about security tools today. No more six-figure appliances that only do one thing marginally well. No more proprietary protocols. We deserve better and we demand better. Envision a world where your security tools talk
From playlist OWASP AppSecUSA 2012

O'Reilly Radar 3/12/12: Hadoop, big data vs analytics, and video data graphics
Special edition of the Radar Show from the 2012 Strata Conference in California 00:15 - Hadoop creator Doug Cutting discussing the similarities between Linux and the big data world. 7:04 - Max Gadney from After the Flood explains the benefits of video data graphics. 13:46 -- Kaggle's Je
From playlist O'Reilly Radar Shows

Malware Analysis Bootcamp - Understanding The PE Header
Welcome to the Malware Analysis Bootcamp. We will be covering everything you need to know to get started in Malware Analysis professionally. In this video, we will be taking a look at the PE header, why it is important for static analysis and the sections. Link to slides: https://drive.go
From playlist Malware Analysis

DevOps Test Automation | DevOps Tutorial For Beginners | DevOps Tutorial | Simplilearn
🔥DevOps Engineer Master Program (Discount Code: YTBE15): https://www.simplilearn.com/devops-engineer-masters-program-certification-training?utm_campaign=DevOpsTestAutomation-otP35qZ_kmk&utm_medium=Descriptionff&utm_source=youtube 🔥Post Graduate Program In DevOps: https://www.simplilearn.c
From playlist DevOps Tutorial For Beginners 🔥 | Simplilearn [Updated]

DevOpsDays Philly 2017 - A Better Technical Interview by Sam Jones
DevOpsDays Philly 2017 - A Better Technical Interview by Sam Jones Let’s make a valuable interview by setting better expectations and creating better evaluation techniques. Let’s make an honest interview by asking instead of assuming, and treating candidates like they’ll be treated on th
From playlist DevOpsDays Philadelphia 2017

Malware Analysis Bootcamp - Introduction To Malware Analysis
Welcome to the Malware Analysis Bootcamp. We will be covering everything you need to know to get started in Malware Analysis professionally. In this video, we will introduce you to malware analysis, the objectives of malware analysis and the various types of malware analysis. Link to slid
From playlist Malware Analysis

Black Hat USA 2010: Finger Pointing for Fun Profit and War 1/5
Speaker: Tom Parker Recent incidents commonly thought to be linked to state sponsored activities have given rise to much discussion over the reliability of technical analysis as a source for adversary attribution - specifically in regards to what is commonly termed as the Advanced Persist
From playlist Black Hat USA 2010
