
A brief introduction to Python. Where to go to download Python and what to install.
From playlist Introduction to Pyhton for mathematical programming

Extending the capabilities of Python with the NumPy module
From playlist Introduction to Pyhton for mathematical programming

Setting up and solving ordinary differential equations with constant coefficients.
From playlist Introduction to Pyhton for mathematical programming
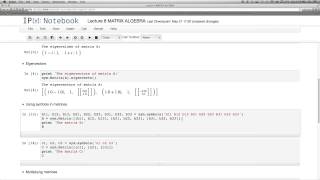
Various manipulations of matrices including teh caclulation of eigenvalues and eigenvectors.
From playlist Introduction to Pyhton for mathematical programming
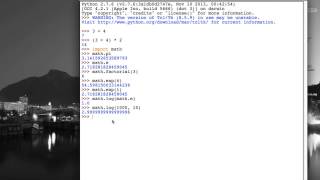
Extending the capabilities of Python with the Math module
From playlist Introduction to Pyhton for mathematical programming

Bitcoin Q&A: Optional Passphrases (Advanced Security Feature) and Seed Storage
Do optional passphrases protect against leaks or compromises of mnemonic seed words? Why are brain wallets usually insecure? Why should you not "roll your own crypto" and promote creative schemes that deviate from the standards (like BIP39), without at least getting peer review and testing
From playlist English Subtitles - aantonop Videos with subtitles in English

RedDotRuby 2014 - 80,000 Plaintext Passwords: An Open Source Love Story in 3 Acts by T.j. Schuck
fluffmuffin, peppercorn, gilligan — those are just a few of our users' plain text passwords. I have 80,000 more, and it only took me 87 seconds to gather them from our customer database in a white-hat attack. In Act I, we'll cover the history of secure password storage, examine the hack,
From playlist RedDotRuby 2014

DjangoCon US 2017 - hunter2: A Symphony of Password Horror by Lilly Ryan
DjangoCon US 2017 - hunter2: A Symphony of Password Horror by Lilly Ryan The year is 2017. We have hoverboards, jetpacks, solar-powered cars, and also so many awful passwords that it’s become trivial for pretty much anyone to have their accounts compromised. We’ve got passwords for our p
From playlist DjangoCon US 2017
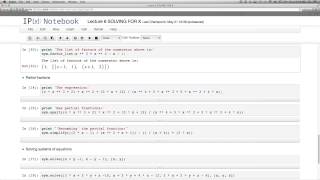
Using Sympy to solve algebraic expressions and equations.
From playlist Introduction to Pyhton for mathematical programming

DEFCON 20: Cryptohaze Cloud Cracking
Speaker: BITWEASIL LEAD DEVELOPER, CRYPTOHAZE TOOLS Bitweasil goes through the latest developments in the Cryptohaze GPU based password cracking suite. WebTables is a new rainbow table technology that eliminates the need to download rainbow tables before using them, and the new Cryptohaze
From playlist DEFCON 20

GoGaRuCo 2012 - Modern Cryptography
Modern Cryptography by: John Downey Once the realm of shadowy government organizations, cryptography now permeates computing. Unfortunately, it is difficult to get correct and most developers know just enough to be harmful for their projects. Together, we’ll go through the basics of moder
From playlist gogaruco 2012

Dealing with limits in Sympy.
From playlist Introduction to Pyhton for mathematical programming

0109 [ C++/React ] player registration
This is #109 in my series of live (Twitch) coding streams. This stream I implemented the PBKDF2 (Password-Based Key Derivation Function 2) specified in RFC 8018, for use in storing hashed player passwords in the game state. I also added a command and state object for storing player inf
From playlist Excalibur

More videos like this online at http://www.theurbanpenguin.com Password protecting the boot menu As with the legacy GRUB it is possible to edit menu entries during the boot process. This may not always desirable so this, as before can be secured using passwords but additionally usernames a
From playlist Learning Ubuntu Server

OpenGL with PyOpenGL Python and PyGame p.3 - Movement and Navigation
In this tutorial, we learn some more of the basics of OpenGL using PyOpenGL, which is a Python module for working with OpenGL, along with using PyGame, which is a popular gaming module for Python. PyOpenGL works with many other Python modules as well. In this example, we learn more about t
From playlist PyGame with Python 3 Game Development

Tim Taubert: Keeping secrets with JavaScript | JSConf EU 2014
With the web slowly maturing as a platform the demand for cryptography in the browser has risen, especially in a post-Snowden era. Many of us have heard about the upcoming Web Cryptography API but at the time of writing there seem to be no good introductions available. We will take a look
From playlist JSConf EU 2014

Rocky Mountain Ruby 2014 - 80,00 Plaintext Passwords
fluffmuffin, peppercorn, gilligan — those are just a few of our users' plaintext passwords. I have 80,000 more, and it only took me 87 seconds to gather them from our customer database in a white-hat attack. In Act I, we'll cover the history of secure password storage, examine the hack,
From playlist Rocky Mountain Ruby 2014

The next set of video lectures deals with Sympy.
From playlist Introduction to Pyhton for mathematical programming

Game Development in Python 3 With PyGame - 11 - Buttons p. 1
See http://pythonprogramming.net for sample code PyGame with Python 3 Playlist: http://www.youtube.com/playlist?list=PLQVvvaa0QuDdLkP8MrOXLe_rKuf6r80KO In this PyGame with Python 3 tutorial, we cover the idea of button creation with PyGame. At the time of me making this video, there is n
From playlist PyGame with Python 3 Game Development

Yes, You Too Can Break Crypto: Exploiting Common Crypto Mistakes
Cryptography is tricky. Sure, everybody knows not to roll out their own crypto, but is it enough? Are the standard algorithms, libraries, and utilities always used the right way? This is of course a rhetorical question! Humans keep making mistakes that other humans can exploit, and Murphy’
From playlist Security