
List-Decoding Multiplicity Codes - Swastik Kopparty
Swastik Kopparty Rutgers University April 10, 2012 We study the list-decodability of multiplicity codes. These codes, which are based on evaluations of high-degree polynomials and their derivatives, have rate approaching 1 while simultaneously allowing for sublinear-time error-correction.
From playlist Mathematics

Improved List-Decoding and Local List-Decoding Algorithms for Polynomial Codes - Swastik Kopparty
More videos on http://video.ias.edu
From playlist Mathematics

C Programming: Sorting and searching arrays of structs
In this session we learn how to sort an array of structs, then search it using the built-in binary search (bsearch) function.
From playlist C Programming

Dynamic Random Access Memory (DRAM). Part 3: Binary Decoders
This is the third in a series of computer science videos is about the fundamental principles of Dynamic Random Access Memory, DRAM, and the essential concepts of DRAM operation. This video covers the role of the row address decoder and the workings of generic binary decoders. It also expl
From playlist Random Access Memory

(IC 5.7) Decoder for arithmetic coding (infinite-precision)
Pseudocode for the arithmetic coding algorithm, assuming addition and multiplication can be done exactly (i.e. with infinite precision). Later we modify this to work with finite precision. A playlist of these videos is available at: http://www.youtube.com/playlist?list=PLE125425EC837021F
From playlist Information theory and Coding
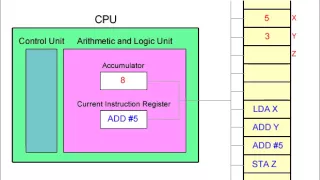
Fetch Decode Execute Cycle and the Accumulator
This (silent) video illustrates the fetch decode execute cycle. A simplified view of the CPU focusses on the role of the accumulator register when a program runs. For simplicity, the machine code commands being executed are represented by assembly language code. This assembly language co
From playlist Computer Hardware and Architecture

Learn how to read key-value pairs from a text file into a HashMap.
From playlist Intermediate Java

(IC 2.4) Decoding - prefix versus non-prefix
Examples to illustrate the ease of decoding a prefix code versus a non-prefix code. A playlist of these videos is available at: http://www.youtube.com/playlist?list=PLE125425EC837021F
From playlist Information theory and Coding

Locally testable and locally correctable codes approaching the GV bound - Shubhangi Saraf
Computer Science/Discrete Mathematics Seminar I Topic: Locally testable and locally correctable codes approaching the Gilbert-Varshamov bound Speaker: Shubhangi Sara Affiliation: Rutgers University Date: November 27, 2017 For more videos, please visit http://video.ias.edu
From playlist Mathematics
From playlist Week 3 2015 Shorts

Fetching Weather Data with Swift
►► Get my Python Programming Bootcamp Series for $9.99 ( Expires April 8th ) : bit.ly/SavePython6 (SEE HOW TO GET THE COURSE FOR $1 BELOW) ►► Highest Rated Python Udemy Course + 23 Hrs + 99 Videos + New Videos Every Week Get the Code Here : bit.ly/WeatherSwift Part #1 of this Series : ht
From playlist iOS Development

Algorithmizing the Multiplicity Schwartz-Zippel Lemma - Prahladh Harsha
Computer Science/Discrete Mathematics Seminar I Topic: Algorithmizing the Multiplicity Schwartz-Zippel Lemma Speaker: Prahladh Harsha Affiliation: Tata Institute of Fundamental Research Date: January 31, 2022 The degree mantra states that any non-zero univariate polynomial of degree at
From playlist Mathematics

From playlist fastai v2 code walk-thrus

From playlist fastai v2 code walk-thrus
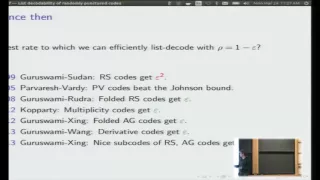
List decodability of randomly punctured codes - Mary Wootters
Mary Wootters University of Michigan March 24, 2014 We consider the problem of the list-decodability of error correcting codes. The well-known Johnson bound implies that any code with good distance has good list-decodability, but we do not know many structural conditions on a code which gu
From playlist Mathematics

List decoding with double samplers - Inbal Livni-Navon
Computer Science/Discrete Mathematics Seminar I Topic: List decoding with double samplers Speaker: Inbal Livni-Navon Affiliation: Weizmann Institute Date: December 6, 2021 The ABNNR encoding is a classical encoding scheme that amplifies the distance of an error correcting code. The enco
From playlist Mathematics
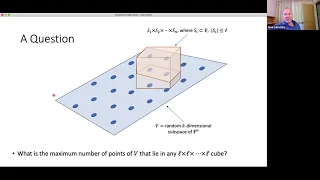
Thresholds for Random Subspaces, aka, LDPC Codes Achieve List-Decoding Capacity - Mary Wootters
Computer Science/Discrete Mathematics Seminar I Topic: Thresholds for Random Subspaces, aka, LDPC Codes Achieve List-Decoding Capacity Speaker: Mary Wootters Affiliation: Stanford University Date: November 30, 2020 For more video please visit http://video.ias.edu
From playlist Mathematics

Deep Learning for Audio and Natural Language Processing
In the third webinar in the Machine Learning webinar series, learn to use machine learning for audio analysis with some real-world applications of neural net models. Also featured is a demonstration of using neural net models for natural language processing.
From playlist Machine Learning Webinar Series

How To Build A Image Inpainting and Super Resolution Tool | Session 02 | #keras | #python
Don’t forget to subscribe! Ever thought of creating a tool that can perform Image Inpainting and Super Resolution? This project will teach you how to create an Image Inpainting Tool using Keras. This series will cover all the details (resources, tools, languages, etc) that are necessary
From playlist Image Inpainting & Super Resolution Tool
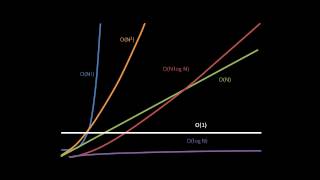
Searching and Sorting Algorithms (part 4 of 4)
Introductory coverage of basic searching and sorting algorithms, as well as a rudimentary overview of Big-O algorithm analysis. Part of a larger series teaching programming at http://codeschool.org
From playlist Searching and Sorting Algorithms