
Find the critical values of an absolute value function
👉 Learn how to find the critical values of a function. The critical values of a function are the points where the graph turns. They are also called the turning points of a function. To obtain the critical points of a function, first, we obtain the first derivative of the function. Next, w
From playlist Find the Critical Values of a Function

Solving an Absolute Value Equation and Checking for Extraneous Solutions
Learn how to solve absolute value equations with extraneous solutions. Absolute value of a number is the positive value of the number. For instance, the absolute value of 2 is 2 and the absolute value of -2 is also 2. To solve an absolute value problem, we first isolate the absolute value
From playlist Solve Absolute Value Equations

Learn How To Solve an Absolute Value Equation and Check Your Answers
Learn how to solve absolute value equations with extraneous solutions. Absolute value of a number is the positive value of the number. For instance, the absolute value of 2 is 2 and the absolute value of -2 is also 2. To solve an absolute value problem, we first isolate the absolute value
From playlist Solve Absolute Value Equations

Ex: Evaluate a Function and Solve for a Function Value Given a Table
The video explains how to determine a function value and solve for x given a function value when the function is given as a table. Site: http://mathispower4u.com Blog: http://mathispower4u.wordpress.com
From playlist Determining Function Values

Math 023 Fall 2022 090722 Absolute Values (continued)
Recall: what is the definition of the absolute value? Exercise: what is |-x| if x is negative? What is |x| if x is negative? Properties of the absolute value. Examples. Geometric interpretation of |x-y| as the distance between x and y. Examples: using that interpretation to describe
From playlist Course 1: Precalculus (Fall 2022)

DEFCON 20: No More Hooks: Detection of Code Integrity Attacks
Speakers: XENO KOVAH THE MITRE CORPORATION COREY KALLENBERG THE MITRE CORPORATION Hooking is the act of redirecting program control flow somewhere other than it would go by default. For instance code can be "inlined hooked" by rewriting instructions to unconditionally transfer to other co
From playlist DEFCON 20

What Is Checksum Error Detection? | What Is Checksum And How It Works? | Simplilearn
"In this video on 'What Is Checksum?', we will look at one of the most applied error-detection methods of the network domain, the checksum method, along with details and the working steps of the checksum method. Topics covered in this video on 'What Is Checksum?' are as follows: 00:00:00
From playlist Networking

How To Solve an Absolute Value Equation and Test Our Solutions when They Do Not Work
Learn how to solve absolute value equations with extraneous solutions. Absolute value of a number is the positive value of the number. For instance, the absolute value of 2 is 2 and the absolute value of -2 is also 2. To solve an absolute value problem, we first isolate the absolute value
From playlist Solve Absolute Value Equations

CS105: Introduction to Computers | 2021 | Lecture 20.2 Computer Security: Mechanisms
Patrick Young Computer Science, PhD This course is a survey of Internet technology and the basics of computer hardware. You will learn what computers are and how they work and gain practical experience in the development of websites and an introduction to programming. To follow along wi
From playlist Stanford CS105 - Introduction to Computers Full Course

Discrete Structures: Random number generators, checksums, hashing
Learn about random number generators, checksums, and hashing. We'll start with the von Neumann random number generator and the contemporary linear congruential generator. Then we'll go over the Luhn algorithm used for credit card number validation and then introduce hash functions such as
From playlist Discrete Structures, Spring 2022

Cryptocurrency. Part Five: Transaction Validation
This computer science lesson is the fifth in a series about cryptocurrency and non-fungible tokens, also known as NFTs. The series examines some of the technologies underlying various cryptocurrencies such as Bitcoin, as well as some the ethical, cultural and legal implications of these d
From playlist Cryptocurrency

Determine Linear Function Values and Express as Ordered Pairs
This video explains how to determine linear function values. Each function value is also expressed as an ordered pair. http://mathispower4u.com
From playlist Determining Function Values
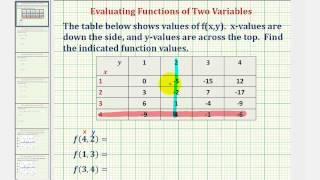
Ex: Function Values of a Function of Two Variables Using a Table
This video provides an example of how to evaluate a function of two variables using a table of values. Site: http://mathispower4u.com
From playlist Functions of Several Variables

DeepSec 2009: Keykeriki: Universal Wireless Keyboard Sniffing For The Masses
Thanks to the DeepSec organisation for making these videos available and let me share the videos on YouTube. Speakers: Thorsten Schröder | Max Moser You probably know or even use one of these wireless keyboards for your computer. If you do, you might be interested in hearing how the key
From playlist DeepSec 2009

CERIAS Security: Fake Picassos, Tampered History, and Digital Forgery 3/6
Clip 3/6 Speaker: Ragib Hasan · University of Illinois at Urbana-Champaign As increasing amounts of valuable information are produced and persist digitally, the ability to determine the origin of data becomes important. In science, medicine, commerce, and government, data provenance trac
From playlist The CERIAS Security Seminars 2009

DeepSec 2009: Reversing and Exploiting an Apple Firmware Update
Thanks to the DeepSec organisation for making these videos available and let me share the videos on YouTube. Speaker: K. Chen K. Chen explains how to use an Apple firmware update to get a foothold on the system. For more information visit: http://bit.ly/DeepSec_2009_information To down
From playlist DeepSec 2009

Iron Sword ※ Cracking Videogame Passwords S1e13 (Wizards & Warriors II)
In the advent of 1990 I played NES games a lot. Knowing nothing about programming but being geekish by nature, I obsessed over cracking the password systems in those games. In this series we will study some of these systems. Become a member: https://youtube.com/Bisqwit/join Twitter: http
From playlist Cracking Videogame Passwords Season 1

Solving Absolute Value Equations Using Multi Steps
Learn how to solve absolute value equations with extraneous solutions. Absolute value of a number is the positive value of the number. For instance, the absolute value of 2 is 2 and the absolute value of -2 is also 2. To solve an absolute value problem, we first isolate the absolute value
From playlist Solve Absolute Value Equations

Bitcoin Multisig and P2SH Transactions with Andreas Antonopoulos - 01/13/14
Bitcoin SF Devs Multisig Transaction class with Andreas Antonopoulos covering simple transactions,simple multisig transactions and P2SH transactions in bitcoin A RAW PPT of this presentation can be downloaded here: https://www.dropbox.com/s/gta94uux5n4p1vy/Bitcoin_Multi-sig-Transactions_A
From playlist Bitcoin Talks by Andreas M. Antonopoulos
