
Speaker: Luka Perkov provisioning behind the scene This talk is aimed to give an insight into CPE WAN Management Protocol (CWMP) and its GPLv2 implementations that were developed in the past year. CWMP (often called only TR-069) enables ISP to remotely configure, manage, upgrade and trou
From playlist 29C3: Not my department

Black Hat USA 2010: Attacking Kerberos Deployments 4/4
Speakers: Scott Stender, Brad Hill & Rachel Engel The Kerberos protocol is provides single sign-on authentication services for users and machines. Its availability on nearly every popular computing platform - Windows, Mac, and UNIX variants - makes it the primary choice for enterprise aut
From playlist BH USA 2010 - OS WARS
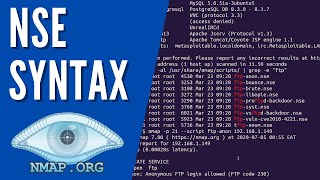
In this video, I explain and demonstrate how to use the Nmap scripting engine (NSE). Nmap is used to discover hosts and services on a computer network by sending packets and analyzing the responses. Nmap provides a number of features for probing computer networks, including host discovery
From playlist Nmap

Nmap - HTTP Enumeration - Detecting HTTP Methods
In this video, I demonstrate how to detect the active HTTP methods on a web server with Nmap. Nmap is used to discover hosts and services on a computer network by sending packets and analyzing the responses. Nmap provides a number of features for probing computer networks, including host d
From playlist Nmap

Supermicro E300-9D-4CN8TP with Intel Xeon D-2123IT Review
STH Main Site Article: https://www.servethehome.com/supermicro-e300-9d-4cn8tp-review-a-4x-10gbe-and-4x-1gbe-server/ STH Merch on Teespring: https://the-sth-merch-shop.myteespring.co/ STH Top 5 Weekly Newsletter: https://eepurl.com/dryM09 In our Supermicro E300-9D-4C8TP review, we see what
From playlist Cool Server Hardware Series

In this video, I demonstrate how to perform SMB enumeration with Nmap. Nmap is used to discover hosts and services on a computer network by sending packets and analyzing the responses. Nmap provides a number of features for probing computer networks, including host discovery and service an
From playlist Nmap

Introduction to TCP/IP and Sockets, part 2: Example code Walk-Through
This is a walk-through of example C++ code for using Sockets to send and receive messages between programs using the Internet protocols. This is part 2 of the series. Part 1 is here: https://youtu.be/C7CpfL1p6y0 Here is a link to all the code: https://github.com/rhymu8354/SocketTutori
From playlist Introduction to TCP/IP and Sockets

MPC in the Head With Applications to Blockchain (Lecture 2) by Carmit Hazay
DISCUSSION MEETING : FOUNDATIONAL ASPECTS OF BLOCKCHAIN TECHNOLOGY ORGANIZERS : Pandu Rangan Chandrasekaran DATE : 15 to 17 January 2020 VENUE : Madhava Lecture Hall, ICTS, Bangalore Blockchain technology is among one of the most influential disruptive technologies of the current decade.
From playlist Foundational Aspects of Blockchain Technology 2020

A Tutorial on Network Protocols
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Communications and Network Security | CISSP Training Videos
🔥 Enroll for FREE CISSP Course & Get your Completion Certificate: https://www.simplilearn.com/learn-cloud-security-basics-skillup?utm_campaign=CCSP&utm_medium=DescriptionFirstFold&utm_source=youtube Communication and Network Security : Domain 4 of the CISSP certification course offered by
From playlist Cyber Security Playlist [2023 Updated]🔥

The information cost of quantum memoryless protocols - M. Lauriere - Main Conference - CEB T3 2017
Mathieu Lauriere (NYU Shanghai) / 12.12.2017 Title: The information cost of quantum memoryless protocols Abstract: In this talk, we will consider memoryless quantum communication protocols, where the two parties do not possess any memory besides their classical input and they take turns
From playlist 2017 - T3 - Analysis in Quantum Information Theory - CEB Trimester

Selective Repeat ARQ Explained | Selective Repeat Protocol | Networking Tutorial | Simplilearn
🔥Advanced Executive Program In Cybersecurity: https://www.simplilearn.com/pgp-advanced-executive-program-in-cyber-security?utm_campaign=SelectiveRepeatARQExplained-dUX8A6VTqdk&utm_medium=Descriptionff&utm_source=youtube🔥Caltech Cybersecurity Bootcamp(US Only): https://www.simplilearn.com/c
From playlist Cyber Security Playlist [2023 Updated]🔥

WebAssembly: The What, Why and How
WebAssembly is a portable, size, and load-time efficient binary format for the web. It is an emerging standard being developed in the WebAssembly community group, and supported by multiple browser vendors. This talk details what WebAssembly is, the problems it is trying to solve, exciting
From playlist Talks

Black Hat USA 2010: Burning Asgard: What Happens When Loki Breaks Free 2/5
Speakers: Enno Rey, Daniel Mende I personally remember the release of Yersinia at Black Hat Europe 2005. It was a ground breaking experience: a number of Layer 2 attacks regarded purely theoretical until then, was suddenly available in a mostly automated way. And those guys even showed so
From playlist BH USA 2010 - NETWORK

29C3: The future of protocol reversing and simulation applied on ZeroAccess botnet (EN)
Speakers: Frédéric Guihéry | Georges Bossert Mapping your enemy Botnet with Netzob Have you ever been staring for nights at binary or hexadecimal data flows extracted from an USB channel? Don't you remember yourself searching for some patterns and similarities in this fuc*g mess of zeros
From playlist 29C3: Not my department




