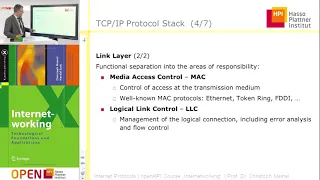
Quantum gates | Quantum information science
KLM protocol
The KLM scheme or KLM protocol is an implementation of linear optical quantum computing (LOQC), developed in 2000 by , Raymond Laflamme and Gerard J. Milburn. This protocol makes it possible to create universal quantum computers solely with linear optical tools. The KLM protocol uses linear optical elements, single-photon sources and photon detectors as resources to construct a quantum computation scheme involving only ancilla resources, quantum teleportations and error corrections. (Wikipedia).