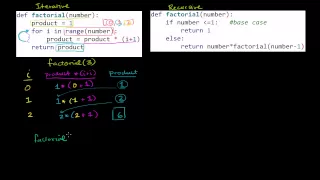
Comparing Iterative and Recursive Factorial Functions
Comparing iterative and recursive factorial functions
From playlist Computer Science
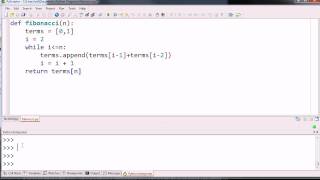
Iterative Fibonacci Function Example
One way to write a Fibonacci function iteratively
From playlist Computer Science

11_3_1 The Gradient of a Multivariable Function
Using the partial derivatives of a multivariable function to construct its gradient vector.
From playlist Advanced Calculus / Multivariable Calculus

C07 Homogeneous linear differential equations with constant coefficients
An explanation of the method that will be used to solve for higher-order, linear, homogeneous ODE's with constant coefficients. Using the auxiliary equation and its roots.
From playlist Differential Equations

Am I attracted to the Sierpinski triangle?
Broadcasted live on Twitch -- Watch live at https://www.twitch.tv/simuleios
From playlist research

SynFlow: Pruning neural networks without any data by iteratively conserving synaptic flow
The Lottery Ticket Hypothesis has shown that it's theoretically possible to prune a neural network at the beginning of training and still achieve good performance, if we only knew which weights to prune away. This paper does not only explain where other attempts at pruning fail, but provid
From playlist Papers Explained

Elizaveta Rebrova - Low-rank tensor recovery from memory-efficient measurements - IPAM at UCLA
Recorded 01 December 2022. Elizaveta Rebrova of Princeton University presents "Low-rank tensor recovery from memory-efficient measurements" at IPAM's Multi-Modal Imaging with Deep Learning and Modeling Workshop. Abstract: Abstract: Recovery of sparse vectors and low-rank matrices from a sm
From playlist 2022 Multi-Modal Imaging with Deep Learning and Modeling

Aymeric Dieuleveut - Federated Learning with Communication Constraints: Challenges in (...)
In this presentation, I will present some results on optimization in the context of federated learning with compression. I will first summarise the main challenges and the type of results the community has obtained, and dive into some more recent results on tradeoffs between convergence an
From playlist 8th edition of the Statistics & Computer Science Day for Data Science in Paris-Saclay, 9 March 2023

Broadcasted live on Twitch -- Watch live at https://www.twitch.tv/simuleios
From playlist research

CERIAS Security: Recent Attacks on MD5 2/6
Clip 2/6 Speaker: John Black · University of Colorado at Boulder Cryptology is typically defined as cryptography (the construction of cryptographic algorithms) and cryptanalysis (attacks on these algorithms). Both are important, but the latter is more fun. Cryptographic hash functions
From playlist The CERIAS Security Seminars 2006

Simon Foucart: Essentials of Compressive Sensing (Lecture 1)
Compressive Sensing has recently had a tremendous impact in science and engineering, because it revealed the theoretical possibility of acquiring structured high-dimensional objects using much less information than previously expected, and more importantly because it provided practical pro
From playlist HIM Lectures: Trimester Program "Mathematics of Signal Processing"

Michael E. Davies: Inexact gradient projection and fast data driven compressed sensing
Abstract: We consider the convergence of the iterative projected gradient (IPG) algorithm for arbitrary (typically nonconvex) sets and when both the gradient and projection oracles are only computed approximately. We consider different notions of approximation of which we show that the Pro
From playlist Probability and Statistics

Special Relativity C2 Length Contraction
Relativistic length contraction.
From playlist Physics - Special Relativity

Yingzhou Li - Fast Algorithms for FCI excited states - IPAM at UCLA
Recorded 02 May 2022. Yingzhou Li of Duke University presents "Fast Algorithms for FCI excited states" at IPAM's Large-Scale Certified Numerical Methods in Quantum Mechanics Workshop. Abstract: Fast algorithms are proposed for the electronic structure excited-state calculation in the confi
From playlist 2022 Large-Scale Certified Numerical Methods in Quantum Mechanics

Stanley Osher: "Compressed Sensing: Recovery, Algorithms, and Analysis"
Graduate Summer School 2012: Deep Learning, Feature Learning "Compressed Sensing: Recovery, Algorithms, and Analysis" Stanley Osher, UCLA Institute for Pure and Applied Mathematics, UCLA July 20, 2012 For more information: https://www.ipam.ucla.edu/programs/summer-schools/graduate-summe
From playlist GSS2012: Deep Learning, Feature Learning

Solving a system of equations with infinite many solutions
👉Learn how to solve a system (of equations) by elimination. A system of equations is a set of equations which are collectively satisfied by one solution of the variables. The elimination method of solving a system of equations involves making the coefficient of one of the variables to be e
From playlist Solve a System of Equations Using Elimination | Medium