
This video is part of an online course, Intro to Algorithms. Check out the course here: https://www.udacity.com/course/cs215.
From playlist Introduction to Algorithms

From playlist Week 9: Social Networks

Network Analysis. Course introduction.
Introduction to the Social Network Analysis course.
From playlist Structural Analysis and Visualization of Networks.
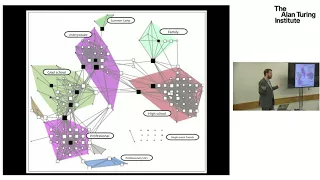
Social network analysis - Introduction to structural thinking: Dr Bernie Hogan, University of Oxford
Social networks are a means to understand social structures. This has become increasingly relevant with the shift towards mediated interaction. Now we can observe and often analyse links at a scale that far outpaces what was possible only decades ago. While this prompts new methodologies,
From playlist Data science classes

In the Company of Scholars Lecture Series: "Using Social Networks for Good"
Human beings choose their friends, neighbors, and co-workers, and we inherit our relatives; and each of the people to whom we are connected also does the same, such that, in the end, we humans assemble ourselves into vast, face-to-face social networks. These networks are the human equivale
From playlist In The Company Of Scholars
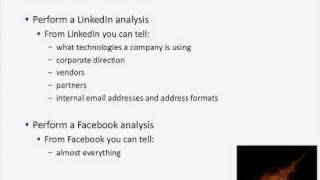
O'Reilly Webcast: Information Security and Social Networks
Social networks are an information security game changer, and enterprises and their management are struggling to understand and deal with the security risks of social networks. Traditional information security protected your corporate IT perimeter. But that won't help in the web 2.0 era
From playlist O'Reilly Webcasts

Jennifer Tour Chayes (Microsoft Research New England and Microsoft Research New York City) URL: https://www.icts.res.in/lecture/4/details/1644/ Description: Everywhere we turn these days, we find that networks can be used to describe relevant interactions.In the high tech world, we see th
From playlist Distinguished Lectures

Protection Of Information Assets | CISA Training Videos
Certified Information System Auditor (CISA) Protection of Information Assets Objectives: • Understand and provide assurance that the enterprise’s security policies, standards, procedures and controls ensure the confidentiality, integrity and availability of information assets • Detail the
From playlist CISA Training Videos

Next Generation Red Teaming - Robert Wood
Too often organizations conduct assessments within a vacuum: physical, network, social, or application-layer. Attackers do not confine themselves similarly and avail themselves of whatever combination of techniques most effectively achieves their desired impact. Red team assessments aim to
From playlist AppSec California 2014

Introduction to SNA. Lecture 1. Introduction to Network Science
Lecture slides: http://www.leonidzhukov.net/hse/2015/sna/lectures/lecture1.pdf Introduction to network science. Examples.
From playlist Introduction to SNA

NIPS 2011 Big Learning - Algorithms, Systems, & Tools Workshop: Towards Human Behavior...
Big Learning Workshop: Algorithms, Systems, and Tools for Learning at Scale at NIPS 2011 Invited Talk: Towards Human Behavior Understanding from Pervasive Data: Opportunities and Challenges Ahead by Nuria Oliver Nuria Oliver is currently the Scientific Director for the Multimedia, HCI
From playlist NIPS 2011 Big Learning: Algorithms, System & Tools Workshop

Ethical Hacking Tutorial For Beginners | Ethical Hacking Course | Ethical Hacking Training | Edureka
🔥Edureka Cyber Security Course: https://www.edureka.co/cybersecurity-certification-training 🔵 Edureka Cyber Security Masters Program: https://bit.ly/3pfHHIN This Edureka "Ethical Hacking Tutorial" video will give you an introduction to Ethical Hacking. This video will give you an exhaustiv
From playlist Cyber Security Training for Beginners | Edureka

In this video Professor Chris Bail discusses text networks-- an automated technique for analyzing text data that combines the principles of network analysis and natural language processing. Link to slides: https://compsocialscience.github.io/summer-institute/2020/materials/day3-text-analys
From playlist SICSS 2020

Ethical Hacking Tutorial Basics-Why, what, how? | Ethical Hacking Training | Edureka Ethical Hacking
🔥Edureka Online Training: https://www.edureka.co/cybersecurity-certification-training This Edureka "Ethical Hacking Tutorial" LIVE session will give you an introduction to Ethical Hacking. This video will give you an exhaustive video on key topics of Ethical Hacking for beginners! 🔵 PGP
From playlist Edureka Live Classes 2020



