
DSLR cameras for video capture
Introduction to DSLR cameras to use as video capturing devices for lectures.
From playlist Creating video tutorials - a series for academic personnel
If you are interested in learning more about this topic, please visit http://www.gcflearnfree.org/ to view the entire tutorial on our website. It includes instructional text, informational graphics, examples, and even interactives for you to practice and apply what you've learned.
From playlist Machine Learning

This video discusses the mean (average) as a balancing point. Diagrams model how to find values that allow the balancing point to be maintained.
From playlist EngageNY Grade 6 Module 6

If you are interested in learning more about this topic, please visit http://www.gcflearnfree.org/ to view the entire tutorial on our website. It includes instructional text, informational graphics, examples, and even interactives for you to practice and apply what you've learned.
From playlist Microsoft Excel

ShmooCon 2014: Timing-Based Attestation: Sexy Defense, or the Sexiest?
For more information visit: http://bit.ly/shmooc14 To download the video visit: http://bit.ly/shmooc14_down Playlist Shmoocon 2014: http://bit.ly/shmooc14_pl Speakers: Xeno Kovah | Corey Kallenberg | John Butterworth What if I told you it's possible to ask a drunk person if he's drunk -
From playlist ShmooCon 2014

DEFCON 20: No More Hooks: Detection of Code Integrity Attacks
Speakers: XENO KOVAH THE MITRE CORPORATION COREY KALLENBERG THE MITRE CORPORATION Hooking is the act of redirecting program control flow somewhere other than it would go by default. For instance code can be "inlined hooked" by rewriting instructions to unconditionally transfer to other co
From playlist DEFCON 20

If you are interested in learning more about this topic, please visit http://www.gcflearnfree.org/ to view the entire tutorial on our website. It includes instructional text, informational graphics, examples, and even interactives for you to practice and apply what you've learned.
From playlist Making Decisions

Introduction to Programming and Computer Science - Full Course
In this course, you will learn basics of computer programming and computer science. The concepts you learn apply to any and all programming languages and will be a good base onto which you can build your skills. This video is meant for those who are interested in computer science and pro
From playlist Computer Science Concepts

Introduction to Classification Models
Ever wonder what classification models do? In this quick introduction, we talk about what classifications models are, as well as what they are used for in machine learning. In machine learning there are many different types of models, all with different types of outcomes. When it comes t
From playlist Introduction to Machine Learning

An Introduction to Programming
Welcome to An Introduction to Programming. In this lecture-style series, we will be taking you through the basics of computer science and giving you the tools required to delve into any programming language you would like to learn. This video hopes to give you a good base onto which you ca
From playlist Software Development

Hacktivity 2010: Buffer Overflow step II .- ASLR and DEP Eveasion Techniques
Speaker: András Kabai
From playlist Hacktivity 2010

Introduction to Precision, Recall and F1 | Classification Models
You may have come across the terms "Precision, Recall and F1" when reading about Classification Models and machine learning. In this Data Science in Minutes tutorial, we will explain what Precision, Recall and F1 are, and when you can use each for measuring the accuracy of your model! Lea
From playlist Introduction to Machine Learning

Security Vulnerability Mitigations
Security vulnerabilities allow software to be manipulated in such a way that it misbehaves to the benefit of an attacker - security vulnerability mitigations work to thwart attempts to successfully exploit such a vulnerability. This landscape is continually changing in both the types of at
From playlist Security
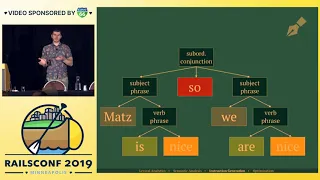
RailsConf 2019 - Pre-evaluation in Ruby by Kevin Deisz
RailsConf 2019 - Pre-evaluation in Ruby by Kevin Deisz _______________________________________________________________________________________________ Cloud 66 - Pain Free Rails Deployments Cloud 66 for Rails acts like your in-house DevOps team to build, deploy and maintain your Rails ap
From playlist RailsConf 2019

AI Weekly Update #11 - November 4th, 2019
https://deepmind.com/blog/article/AlphaStar-Grandmaster-level-in-StarCraft-II-using-multi-agent-reinforcement-learning https://www.microsoft.com/en-us/research/blog/pipedream-a-more-effective-way-to-train-deep-neural-networks-using-pipeline-parallelism/ https://ai.googleblog.com/2019/10/le
From playlist AI Research Weekly Updates

RubyConf 2015 - Inside Ruby's VM: The TMI Edition. by Aaron Patterson
Inside Ruby's VM: The TMI Edition. by Aaron Patterson This is about Ruby's Virtual Machine. Specifically MRI's Virtual Machine. We will take a dive in to how your Ruby code is compiled in to byte code and how that byte code is executed. Once we get a grip on how the VM works, we'll see ho
From playlist RubyConf 2015

Test-Time Augmentation In Machine Learning.
Most people think of data augmentation as a technique to improve their model during training. Starting from an initial dataset, you can generate synthetic copies of each sample that will make a model resilient to variations in the data. Test-time augmentation is a technique where you can
From playlist Machine Learning Techniques

If you are interested in learning more about this topic, please visit http://www.gcflearnfree.org/ to view the entire tutorial on our website. It includes instructional text, informational graphics, examples, and even interactives for you to practice and apply what you've learned.
From playlist The Internet

Stanford Seminar - Concatenative Programming: From Ivory to Metal
EE380: Computer Systems Colloquium Seminar Concatenative Programming: From Ivory to Metal Speaker: Jon Purdy, Microsoft Concatenative programming is a relatively new programming paradigm built on a simple yet powerful tool: function composition. In this talk I will give an overview of con
From playlist Stanford EE380-Colloquium on Computer Systems - Seminar Series
