
Causal Inference is a set of tools used to scientifically prove cause and effect, very commonly used in economics and medicine. This series will go over the basics that any data scientist should understand about causal inference - and point them to the tools they would need to perform it.
From playlist Causal Inference - The Science of Cause and Effect

Inferences: Implicature - Semantics in Linguistics
In this video on #semantics/#pragmatics in #linguistics, we talk about our second type of inference: implicature, and do a few examples with the defeasability / cancellation test and the reinforcement test. Join this channel to get access to perks: https://www.youtube.com/channel/UCGYSfZb
From playlist Semantics in Linguistics

2 Sample t Test v Paired t Test
Identifying the difference between situations when a 2-sample t Test is appropriate and when a paired t Test is appropriate, including the recognition of paired dependent data versus independent samples.
From playlist Unit 9: t Inference and 2-Sample Inference
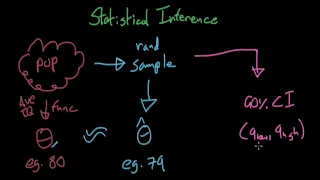
Brief Introduction to Statistical Inference - Causal Inference
In this video, I briefly introduce the topic of Statistical Inference and go over its most fundamental concepts - those that we will use in this series. If you want to learn more about this stuff, check out this link to my entire series on Statistical Inference: https://www.youtube.com/pla
From playlist Causal Inference - The Science of Cause and Effect

Ideal Experiment - Causal Inference
In this video, I give you more details about the fundamental question and the fundamental problem of causal inference with the help of an example (our ideal experiment).
From playlist Causal Inference - The Science of Cause and Effect

t Test Write Up of a Hypothesis Test of an Unknown Population Mean
How to perform and write up a hypothesis test [t test] of an unknown population mean [In accordance with AP Statistics requirements]
From playlist Unit 9: t Inference and 2-Sample Inference
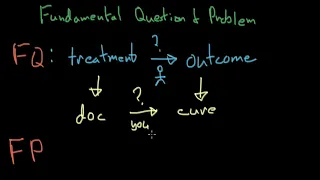
Fundamental Question - Causal Inference
In this video, I define the fundamental question and problem of causal inference and use an example to further explain the concept.
From playlist Causal Inference - The Science of Cause and Effect
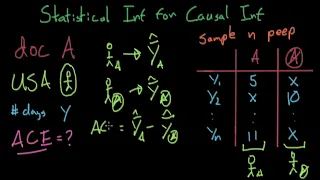
Statistical Inference for Causal Inference - Causal Inference
In this video I explain the concept of statistical inference for causal inference through a realistic group ideal experiment example. Enjoy! Here's the link to my previous Statistical Inference Introduction video if you haven't watched it yet: https://youtu.be/fEGc8ZqveXM
From playlist Causal Inference - The Science of Cause and Effect

On Privacy Implications of Machine Unlearning
A Google TechTalk, presented by Mohammad Mahmoody, 2022/06/08 Differential Privacy for ML seminar series.
From playlist Differential Privacy for ML

Secure Self-supervised Learning
A Google TechTalk, presented by Neil Gong, 2022/05/25 Differential Privacy for ML series.
From playlist Differential Privacy for ML

Cronus: Robust Knowledge Transfer for Federated Learning
A Google TechTalk, 2020/7/29, presented by Reza Shokri, National University of Singapore ABSTRACT: Federated learning is vulnerable to many known privacy and security attacks. Shared parameters leak a significant amount of information about the participants’ private datasets, as they conti
From playlist 2020 Google Workshop on Federated Learning and Analytics
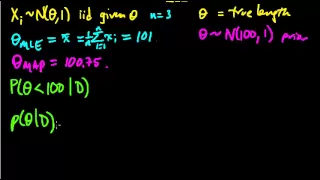
(ML 7.1) Bayesian inference - A simple example
Illustration of the main idea of Bayesian inference, in the simple case of a univariate Gaussian with a Gaussian prior on the mean (and known variances).
From playlist Machine Learning

Experimenting w/ Local & Central Differential Privacy for Both Robustness & Privacy in Fed.Learning
A Google TechTalk, presented by Emiliano De Cristofaro, University College London, at the 2021 Google Federated Learning and Analytics Workshop, Nov. 8-10, 2021. For more information about the workshop: https://events.withgoogle.com/2021-workshop-on-federated-learning-and-analytics/#conte
From playlist 2021 Google Workshop on Federated Learning and Analytics

CERIAS Security: Clouseau: A IP spoofing defense through route-based filtering 5/6
Clip 5/6 Speaker: Jelena Mirkovic · University of Delaware IP spoofing accompanies many malicious activities and is even means for performing reflector DDoS attacks. Route-based filtering (RBF) enables a router to filter spoofed packets based on their incoming interface - this informa
From playlist The CERIAS Security Seminars 2005 (2)

Day 2 Lightning Talks: Privacy & Security
A Google TechTalk, Lightning Talks presented by 7 Speakers, 2021/11/9 ABSTRACT: Each talk is 7 min. plus Q&A. Track 1 - Session Chair: Peter Kairouz (Privacy & Security) 1. Andreas Haeberlen - Privacy-Preserving Federated Analytics with Billions of Users 2. Li Xiong - Federated Learning w
From playlist 2021 Google Workshop on Federated Learning and Analytics

CERIAS Security: Clouseau: A IP spoofing defense through route-based filtering 6/6
Clip 6/6 Speaker: Jelena Mirkovic · University of Delaware IP spoofing accompanies many malicious activities and is even means for performing reflector DDoS attacks. Route-based filtering (RBF) enables a router to filter spoofed packets based on their incoming interface - this informa
From playlist The CERIAS Security Seminars 2005 (2)

Semantic Adversarial Attacks for Privacy Protection
A Google TechTalk, 2020/7/30, presented byAli Shahin Shamsabadi, Ricardo Sanchez-Matilla, Andrea Cavallaro, Queen Mary University of London ABSTRACT: Images shared on social media are routinely analyzed by machine learning models for content annotation and user profiling. These automatic
From playlist 2020 Google Workshop on Federated Learning and Analytics

TensorFuzz: Debugging Neural Networks with Coverage-Guided Fuzzing | AISC
For slides and more information on the paper, visit https://aisc.ai.science/events/2019-08-26 Discussion lead: Tahseen Shabab Motivation: Machine learning models are notoriously difficult to interpret and debug. This is particularly true of neural networks. In this work, we introduce a
From playlist Architecture Tuning

DEFCON 15: Analyzing Intrusions & Intruders
Speaker: Sean M. Bodmer Savid Technologies, Inc. Intrusion Analysis has been primarily reserved for network junkies and bit biters. However, due to the advances in network systems automation we now have time to pay more attention to subtle observations left by attackers at the scene of th
From playlist DEFCON 15

Thanks so much for watching! Please comment below on what topics you'd like to see covered next!
From playlist Causal Inference - The Science of Cause and Effect