
Causal Inference is a set of tools used to scientifically prove cause and effect, very commonly used in economics and medicine. This series will go over the basics that any data scientist should understand about causal inference - and point them to the tools they would need to perform it.
From playlist Causal Inference - The Science of Cause and Effect
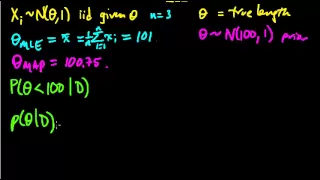
(ML 7.1) Bayesian inference - A simple example
Illustration of the main idea of Bayesian inference, in the simple case of a univariate Gaussian with a Gaussian prior on the mean (and known variances).
From playlist Machine Learning
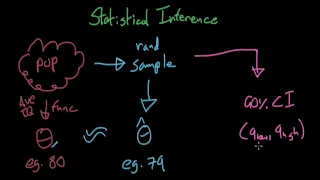
Brief Introduction to Statistical Inference - Causal Inference
In this video, I briefly introduce the topic of Statistical Inference and go over its most fundamental concepts - those that we will use in this series. If you want to learn more about this stuff, check out this link to my entire series on Statistical Inference: https://www.youtube.com/pla
From playlist Causal Inference - The Science of Cause and Effect
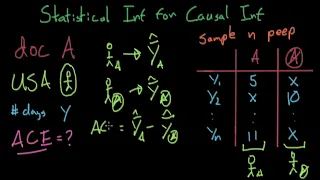
Statistical Inference for Causal Inference - Causal Inference
In this video I explain the concept of statistical inference for causal inference through a realistic group ideal experiment example. Enjoy! Here's the link to my previous Statistical Inference Introduction video if you haven't watched it yet: https://youtu.be/fEGc8ZqveXM
From playlist Causal Inference - The Science of Cause and Effect

Double Blind - Causal Inference
In this video, I talk about the double blind assumption (both placebo effects and scientist preference effects) which serves as a good segue to causal diagrams, which I also go over. Enjoy!
From playlist Causal Inference - The Science of Cause and Effect
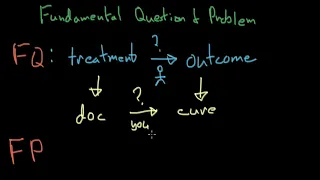
Fundamental Question - Causal Inference
In this video, I define the fundamental question and problem of causal inference and use an example to further explain the concept.
From playlist Causal Inference - The Science of Cause and Effect

Ideal Experiment - Causal Inference
In this video, I give you more details about the fundamental question and the fundamental problem of causal inference with the help of an example (our ideal experiment).
From playlist Causal Inference - The Science of Cause and Effect
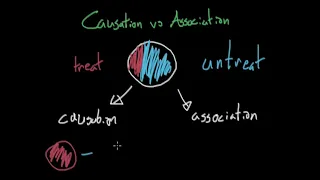
Causation vs. Association - Causal Inference
In this video I talk about the difference between causation and association and explain each of these concepts through an example. Enjoy!
From playlist Causal Inference - The Science of Cause and Effect

Assumptions - Causal Inference
In this video, I introduce the most important assumptions in casual inference that we use in order to avoid mistakes such as presuming association and causation to be one and the same, among others: - Positivity - SUTVA - Large Sample Size - Double Blinded - No Measurement Error - Exchan
From playlist Causal Inference - The Science of Cause and Effect
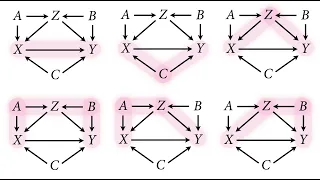
Statistical Rethinking 2022 Lecture 06 - Good & Bad Controls
Slides and other course materials: https://github.com/rmcelreath/stat_rethinking_2022 Intro video: https://www.youtube.com/watch?v=6erBpdV-fi0 Intro music: https://www.youtube.com/watch?v=Pc0AhpjbV58 Chapters: 00:00 Introduction 01:23 Parent collider 08:13 DAG thinking 27:48 Backdoor cri
From playlist Statistical Rethinking 2022

Kernel Recipes 2018 - Mitigating Spectre and Meltdown vulnerabilities - David Woodhouse
The Spectre and Meltdown vulnerabilities are part of a class of hardware flaws which have existed for years, but which have only recently been discovered. David will describe the problems, and explain the techniques used for mitigating them in software — from improvements in the CPU thro
From playlist Kernel Recipes 2018

12. Ch. 4, Section 4.7. Introduction to Logic, Philosophy 10, UC San Diego - BSLIF
Video lecture corresponding to _Basic Sentential Logic and Informal Fallacies_, Chapter 4, Section 4.7. This is for the class Introduction to Logic, Philosophy 10, UC San Diego.
From playlist UC San Diego: PHIL 10 - Introduction to Logic | CosmoLearning.org Philosophy

Erik Bollt - Identify Interactions in Complex Networked Dynamical Systems through Causation Entropy
Recorded 30 August 2022. Erik Bollt of Clarkson University Math/ECE presents "Identifying Interactions in Complex Networked Dynamical Systems through Causation Entropy" at IPAM's Reconstructing Network Dynamics from Data: Applications to Neuroscience and Beyond. Abstract: Inferring the cou
From playlist 2022 Reconstructing Network Dynamics from Data: Applications to Neuroscience and Beyond

Case Study: Wolfram's Symbolic ERP Project
To learn more about Wolfram Technology Conference, please visit: https://www.wolfram.com/events/technology-conference/ Speaker: Daniel Bigham & Todd Reichert Wolfram developers and colleagues discussed the latest in innovative technologies for cloud computing, interactive deployment, mob
From playlist Wolfram Technology Conference 2018

CERIAS Security: Categories of Digital Forensic Investigation Techniques 3/6
Clip 3/6 Speaker: Brian Carrier · Purdue University This talk examines formal concepts of digital forensic investigations. To date, the field has had an applied focus and little theory exists to formally define analysis techniques and requirements. This work defines an extended finite
From playlist The CERIAS Security Seminars 2006

Stanford Seminar - Exploiting modern microarchitectures: Meltdown, Spectre, & other hardware attacks
EE380: Computer Systems Colloquium Seminar Exploiting modern microarchitectures: Meltdown, Spectre, and other hardware attacks Speaker: Jon Masters, Redhat Recently disclosed vulnerabilities against modern high performance computer microarchitectures known as 'Meltdown' and 'Spectre' are
From playlist Stanford EE380-Colloquium on Computer Systems - Seminar Series

Introduction to Primordial Black Hole Dark Matter (Lecture 1) by Ely D. Kovetz
PROGRAM LESS TRAVELLED PATH OF DARK MATTER: AXIONS AND PRIMORDIAL BLACK HOLES (ONLINE) ORGANIZERS: Subinoy Das (IIA, Bangalore), Koushik Dutta (IISER, Kolkata / SINP, Kolkata), Raghavan Rangarajan (Ahmedabad University) and Vikram Rentala (IIT Bombay) DATE: 09 November 2020 to 13 Novemb
From playlist Less Travelled Path of Dark Matter: Axions and Primordial Black Holes (Online)

Hervé Isambert: Learning interpretable networks from multivariate information in biological and...
The reconstruction of graphical models (or networks) has become ubiquitous to analyze the rapidly expanding, information-rich data of biological or clinical interest. I will outline some network reconstruction methods and applications to large scale datasets. In particular, our group has d
From playlist Probability and Statistics
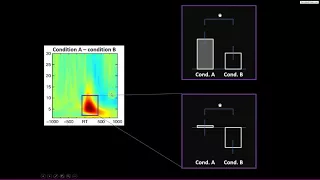
Discussions of circular inference (a.k.a. biased selection, a.k.a. double-dipping) and how to avoid it during statistical analyses. For more online courses about programming, data analysis, linear algebra, and statistics, see http://sincxpress.com/
From playlist OLD ANTS #8) Statistics

26C3: Privacy-Enhanced Event Scheduling 1/6
Clip 1/6 Speaker: Benjamin Kellermann Event schedulers, well-known from groupware and social software, typically share the problem that they disclose detailed availability patterns of their users. This talk distinguishes event scheduling from electronic voting and proposes a privacy-e
From playlist 26C3: Here be dragons day 3