
From playlist everything

PHYS 126 | Lecture 2CD | 2021 | Superposition, Interference and Beats
Superposition, Interference, and a little bit of Beats
From playlist PHYS 126 | 2021 Pandemic Lectures

PHYS 126 | Lecture14CD | Radioactive Decay
LAST ONE!!!!!!!
From playlist PHYS 126 | 2021 Pandemic Lectures

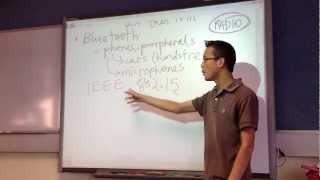
GRCon20 - Security Analysis of Zigbee Networks with Zigator and GNU Radio
Presented by Dimitrios-Georgios Akestoridis, Madhumitha Harishankar, Michael Weber and Patrick Tague at GNU Radio Conference 2020 https://gnuradio.org/grcon20 Zigbee is a wireless communication protocol that is based on the IEEE 802.15.4 standard and is commonly used in smart homes. Numer
From playlist GRCon 2020

25c3: FAIFA: A first open source PLC tool
Speakers: Florian, Xavier Carcelle PowerLineCommunications has now their open source tool PLC (PowerLineCommunications) had been widely used currently for the in-home LANs and for Internet access over PowerLineCommunications based on the market standard called HomePlug. Electricity is a
From playlist 25C3: Nothing to hide
From playlist Communications & Network Systems

Wireless Network Security: Part 2
Fundamental concepts of IEEE 802.11 WLAN are discussed. IEEE 802.11i WLAN security is Reviewed. WAP is presented. Wireless transport layer security is analyzed. IEEE 802.11 Wireless LAN Overview Legacy 802.11 Security: WEP IEEE 802.11i Wireless LAN Security: WPA, WPA2 Wireless Application
From playlist Network Security

Wireless Network Security: Part 1
Fundamental concepts of IEEE 802.11 WLAN are discussed. IEEE 802.11i WLAN security is Reviewed. WAP is presented. Wireless transport layer security is analyzed. IEEE 802.11 Wireless LAN Overview Legacy 802.11 Security: WEP IEEE 802.11i Wireless LAN Security: WPA, WPA2 Wireless Application
From playlist Network Security

Wireless Network Security: Part 3 - WAP
Fundamental concepts of IEEE 802.11 WLAN are discussed. IEEE 802.11i WLAN security is Reviewed. WAP is presented. Wireless transport layer security is analyzed. IEEE 802.11 Wireless LAN Overview Legacy 802.11 Security: WEP IEEE 802.11i Wireless LAN Security: WPA, WPA2 Wireless Application
From playlist Network Security
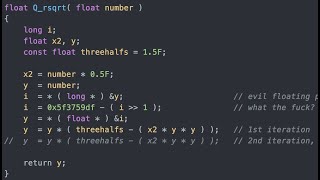
Fast Inverse Square Root — A Quake III Algorithm
In this video we will take an in depth look at the fast inverse square root and see where the mysterious number 0x5f3759df comes from. This algorithm became famous after id Software open sourced the engine for Quake III. On the way we will also learn about floating point numbers and newton
From playlist Summer of Math Exposition Youtube Videos

My #MegaFavNumber – double precise!
The challenge: https://www.youtube.com/watch?v=R2eQVqdUQLI&list=PLar4u0v66vIodqt3KSZPsYyuULD5meoAo A fool's computations of astronomic proportions: https://youtu.be/P_R-CFRRsu4 More interesting things to devote your attention to: https://youtu.be/wOZosStBo40 https://youtu.be/31rMVDu0PKU
From playlist MegaFavNumbers

RubyConf 2022: 1.5 is the Midpoint Between 0 and Infinity by Peter Zhu
What’s the midpoint between 0 and infinity? Well, the answer differs depending on whether you are asking a mathematician, philosopher, or a Ruby developer. I’m not a mathematician or a philosopher, but I am a Ruby developer, so I can tell you that 1.5 is the midpoint between 0 and infinity
From playlist RubyConf 2022: Mini and Houston

DeepSec 2009: Key Management Death Match? Competing KM Standards Technical Deep Dive
Thanks to the DeepSec organisation for making these videos available and let me share the videos on YouTube. Speaker: Marc Massar Key management is a cornerstone of managing and deploying cryptographic devices. Marc Massar discusses the problems connected to key management and standards
From playlist DeepSec 2009






