IEEE 802.1aq
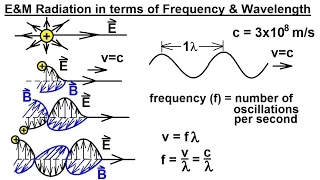
Shortest Path Bridging (SPB), specified in the IEEE 802.1aq standard, is a computer networking technology intended to simplify the creation and configuration of Ethernet networks while enabling multipath routing. It is the replacement for the older spanning tree protocols: IEEE 802.1D, IEEE 802.1w, IEEE 802.1s. These blocked any redundant paths that could result in a switching loop, whereas SPB allows all paths to be active with multiple equal cost paths, provides much larger layer-2 topologies, supports faster convergence times, and improves the efficiency by allowing traffic to load share across all paths of a mesh network. It is designed to preserve the plug-and-play nature that established Ethernet as the de facto protocol at layer 2. The technology provides VLANs on native Ethernet infrastructures using a link-state protocol to advertise both topology and VLAN membership. Packets are encapsulated at the edge either in MAC-in-MAC per IEEE 802.1ah or tagged per IEEE 802.1Q or IEEE 802.1ad and transported only to other members of VLAN. Unicast, multicast, and broadcast are supported and all routing is on symmetric shortest paths. The control plane is based on the Intermediate System to Intermediate System (IS-IS) routing protocol, leveraging a small number of extensions defined in RFC 6329. (Wikipedia).
.gif?width=300)