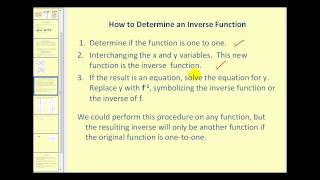
(New Version Available) Inverse Functions
New Version: https://youtu.be/q6y0ToEhT1E Define an inverse function. Determine if a function as an inverse function. Determine inverse functions. http://mathispower4u.wordpress.com/
From playlist Exponential and Logarithmic Expressions and Equations

Verify two rational functions are inverses of each other
👉 Learn how to show that two functions are inverses. The composition of two functions is using one function as the argument (input) of another function. In simple terms composition of two functions is putting one function inside another function. The composition of two functions that are i
From playlist Find the Inverse of a Function
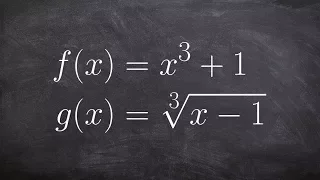
How to verify the power and root function are inverses of each other
👉 Learn how to show that two functions are inverses. The composition of two functions is using one function as the argument (input) of another function. In simple terms composition of two functions is putting one function inside another function. The composition of two functions that are i
From playlist Find the Inverse of a Function

Proving two functions are inverses of each other
👉 Learn how to show that two functions are inverses. The composition of two functions is using one function as the argument (input) of another function. In simple terms composition of two functions is putting one function inside another function. The composition of two functions that are i
From playlist Find the Inverse of a Function

Proving that two functions are not inverses of each other
👉 Learn how to show that two functions are inverses. The composition of two functions is using one function as the argument (input) of another function. In simple terms composition of two functions is putting one function inside another function. The composition of two functions that are i
From playlist Find the Inverse of a Function

Learn how to prove two functions are inverses of each other
👉 Learn how to show that two functions are inverses. The composition of two functions is using one function as the argument (input) of another function. In simple terms composition of two functions is putting one function inside another function. The composition of two functions that are i
From playlist Find the Inverse of a Function

Anne Broadbent - Information-Theoretic Quantum Cryptography Part 1 of 2 - IPAM at UCLA
Recorded 27 July 2022. Anne Broadbent of the University of Ottawa presents "Information-Theoretic Quantum Cryptography" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: These lectures are an introduction to the interplay between quantum information and cryp
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

👉 Learn how to show that two functions are inverses. The composition of two functions is using one function as the argument (input) of another function. In simple terms composition of two functions is putting one function inside another function. The composition of two functions that are i
From playlist Find the Inverse of a Function
Fang Song - Introduction to quantum computing Part 2 of 3 - IPAM at UCLA
Recorded 26 July 2022. Fang Song of Portland State University presents "Introduction to quantum computing II" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: This lecture will focus on two major (families of) quantum algorithms: period finding (a.k.a. Hidd
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

Determining if two functions that are exactly the same have the same inverse
👉 Learn how to show that two functions are inverses. The composition of two functions is using one function as the argument (input) of another function. In simple terms composition of two functions is putting one function inside another function. The composition of two functions that are i
From playlist Find the Inverse of a Function

Cyber Security Live - 1 | Cyber Security Tutorial For Beginners | Cyber Security Training | Edureka
🔥Cyber Security Training: https://www.edureka.co/cybersecurity-certification-training This Edureka video on Cyber Security gives an introduction to the Cyber Security world and talks about its basic concepts. You get to know different kinds of attacks in today's IT world and how cybersecur
From playlist Edureka Live Classes 2020

Verifying two linear equations are inverses of each other
👉 Learn how to show that two functions are inverses. The composition of two functions is using one function as the argument (input) of another function. In simple terms composition of two functions is putting one function inside another function. The composition of two functions that are i
From playlist Find the Inverse of a Function

Some detail about cyclic groups and their application to cryptography, especially Diffie Hellman Key Exchange.
From playlist PubKey

CERIAS Security: Survivable routing in wireless ad hoc networks 1/6
Clip 1/6 Speaker: Cristina Nita-Rotaru · Purdue University In an ad hoc wireless network nodes not in direct range communicate via intermediate nodes. Thus, a significant concern is the ability to route in the presence of Byzantine failures which include nodes that drop, fabricate, mo
From playlist The CERIAS Security Seminars 2005 (1)

Nexus Trimester - Huijia Lin (University of California, Santa Barbara)
Zero Knowledge Huijia Lin (University of California, Santa Barbara) March 28, 2016 Abstract: Zero-knowledge protocols, introduced by Goldwasser, Micali, and Rackoff [STOC 1985], are fascinating constructs in cryptography: They provide the paradoxical guarantee that a player, the prover,
From playlist Nexus Trimester - 2016 - Secrecy and Privacy Theme

Cybersecurity Tutorial | Demo On Man In The Middle Attack | Cybersecurity Training | Edureka
🔵Edureka Cyber Security Masters Program: https://bit.ly/3pfHHIN 🔥Edureka CompTIA Security+ Certification Training: https://bit.ly/3nxeVRl This "Cybersecurity tutorial" video presented by edureka gives an indepth information about the Cyber Security world and talks about its basic concepts.
From playlist Cyber Security Training for Beginners | Edureka

Adeline Roux-Langlois : Using structured variants in lattice-based cryptography - Lecture 2
CONFERENCE Recording during the thematic meeting : « Francophone Computer Algebra Days» the March 07, 2023 at the Centre International de Rencontres Mathématiques (Marseille, France) Filmmaker : Guillaume Hennenfent Find this video and other talks given by worldwide mathematicians on CIR
From playlist Mathematical Aspects of Computer Science

2022 I E Block Community Lecture: AI and Cryptography
July 13, 2022 How is Artificial Intelligence (AI) changing your life and the world? How can you expect your data to be kept secure and private in an AI-driven future? Kristin Lauter of Meta AI Research gives the I. E. Block Community Lecture titled "Artificial Intelligence and Cryptograph
From playlist SIAM Conference Videos
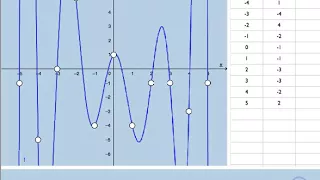
Quiz: Composition of Functions (Graph & Table)
Link: https://www.geogebra.org/m/QgN7nwCh
From playlist Algebra 1: Dynamic Interactives!
