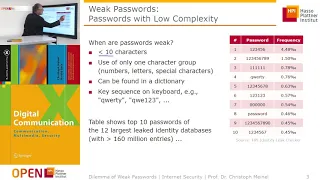
Fundamental concepts of intrusion detection are discussed. Various types of intrusion are analyzed. Password management is explained.
From playlist Network Security

Fundamental concepts of intrusion detection are discussed. Various types of intrusion are analyzed. Password management is explained.
From playlist Network Security

Cryptography is a complex and confusing subject. In this talk you will learn about the core components of cryptography used in software development: securing data with encryption, ensuring data integrity with hashes and digital signatures, and protecting passwords with key derivation funct
From playlist Blockchain

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Logic: The Structure of Reason
As a tool for characterizing rational thought, logic cuts across many philosophical disciplines and lies at the core of mathematics and computer science. Drawing on Aristotle’s Organon, Russell’s Principia Mathematica, and other central works, this program tracks the evolution of logic, be
From playlist Logic & Philosophy of Mathematics

What are Non-Classical logics?
Some of the general classes of non-classical logics I touch in this videos are linear logic, relevant logic, modal logic, many-valued logics, minimal logic, paraconsistent logics and so on and so forth. Let me know if I should dive deeping into a certain scene? https://en.wikipedia.org/wi
From playlist Programming

PROG2006: Advanced Programming Haskell 3b - Basic syntax: * function guards, function patterns * case, if expressions * intersperse, intercalate
From playlist PROG2006 - Programming

Latches and Flip-Flops 3 - The Gated D Latch
This is the third in a series of videos about latches and flip-flops. These bi-stable combinations of logic gates form the basis of computer memory, counters, shift registers, and more. In particular, this video covers the gated D latch, otherwise known as the data latch or simply the D
From playlist Latches and Flip-Flops

Steganography Tutorial - Hide Messages In Images
Steganography is the hiding of a secret message within an ordinary message and the extraction of it at its destination. Steganography takes cryptography a step further by hiding an encrypted message so that no one suspects it exists. Ideally, anyone scanning your data will fail to know it
From playlist Ethical Hacking & Penetration Testing - Complete Course

EEVblog #354 - CityRail PA Amp Teardown
Forum Topic: http://www.eevblog.com/forum/blog-specific/eevblog-354-cityrail-pa-amp-teardown Teardown Tuesday. What's inside an Sydney CityRail Train PA Amplifier. And an extensive tutorial on the design of the power amplifier system from the designer himself, Doug Ford: http://www.dfad.co
From playlist Electronics Teardowns

Category theory for JavaScript programmers #22: Curry-Howard isomorphism
http://jscategory.wordpress.com/source-code/
From playlist Category theory for JavaScript programmers

mod-25 lec-26 Introduction to Fluid Logic
Fundamentals of Industrial Oil Hydraulics and Pneumatics by Prof. R.N. Maiti,Department of Mechanical Engineering,IIT Kharagpur.For more details on NPTEL visit http://nptel.ac.in
From playlist IIT Kharagpur: Fundamentals of Industrial Oil Hydraulics and Pneumatics (CosmoLearning Mechanical Engineering)

Role-Based User Permissions in Firebase
Role-based user authorization or access control, will give you fine-grained control over user permissions for Firebase users. In this lesson we are going to give Firebase users 3 different roles - reader, author, and admin. Full Lesson: https://angularfirebase.com/lessons/role-based-perm
From playlist Firebase

PROG2006: Haskell - basic function syntax, pattern matching, guards.
PROG2006 Advanced Programming Haskell: Basics of functions, syntax. Let/in, where, guards, pattern matching. Simple programming katas. Testing with Hspec. Examples/documentation testing.
From playlist PROG2006 - Programming

At-scale Formal Verification for Industrial Semiconductor Designs - Professor Tom Melham
https://www.turing-gateway.cam.ac.uk/sites/default/files/asset/doc/1707/Big%20Proof%20Day%20Melham%2019-07-2017.pdf #TuringSeminars
From playlist Turing Seminars

35. Alternative Breeding Strategies
Principles of Evolution, Ecology and Behavior (EEB 122) Breeding strategies differ both among males and females of the same species as well as among different species. The difference in breeding strategies among members of the same species can usually be linked to frequency dependence.
From playlist Evolution, Ecology and Behavior with Stephen C. Stearns

How to Play Chess | Must-Know Tactical Patterns in Chess | The Great Courses
Learn more about this course and sign up for a FREE trial of The Great Courses Plus here: https://wondrium.com/youtube/lp/t2/generic?utm_source=Video&utm_medium=Youtube&utm_campaign=145615 From the basics of the game to advanced strategy and tactics, and everything in between, How to Play
From playlist Latest Uploads

Learn how you can use Stateflow® variant transitions to generate code for different software configurations. - Modeling and Simulation | Developer Tech Showcase Playlist: https://www.youtube.com/playlist?list=PLn8PRpmsu08p-wNaS4A7D5VsIVdtqlN-7 - Developer Tips & Tricks Videos: https://www
From playlist Modeling and Simulation | Developer Tech Showcase

Cryptography is a complex and confusing subject. In this talk you will learn about the core components of cryptography used in software development: securing data with encryption, ensuring data integrity with hashes and digital signatures, and protecting passwords with key derivation funct
From playlist Blockchain