
Fundamental concepts of intrusion detection are discussed. Various types of intrusion are analyzed. Password management is explained.
From playlist Network Security

Fundamental concepts of intrusion detection are discussed. Various types of intrusion are analyzed. Password management is explained.
From playlist Network Security

Cryptography is a complex and confusing subject. In this talk you will learn about the core components of cryptography used in software development: securing data with encryption, ensuring data integrity with hashes and digital signatures, and protecting passwords with key derivation funct
From playlist Blockchain

Introduction to the C programming language. Part of a larger series teaching programming. See http://codeschool.org
From playlist The C language

Correctness And Security - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography
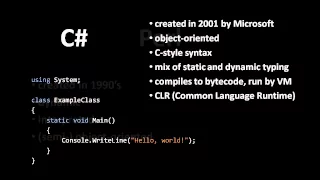
Programming Languages - (part 6 of 7)
How source code becomes a running program, how languages are categorized, and a survey of important languages. Part of a larger series teaching programming. Visit http://codeschool.org
From playlist Programming Languages

MIT 24.900 Introduction to Linguistics, Spring 2022 Instructor: Prof. Norvin W. Richards View the complete course: https://ocw.mit.edu/courses/24-900-introduction-to-linguistics-spring-2022/ YouTube Playlist: https://www.youtube.com/playlist?list=PLUl4u3cNGP63BZGNOqrF2qf_yxOjuG35j This v
From playlist MIT 24.900 Introduction to Linguistics, Spring 2022

The C programming language (unit 2) - 2 of 5 (old version; watch new version instead)
A continuation of discussing the C programming language. This unit goes more into depths on pointers and arrays. Visit http://codeschool.org
From playlist The C language (unit 2)

The C programming language (unit 2) - 4 of 5 (old version; watch new version instead)
A continuation of discussing the C programming language. This unit goes more into depths on pointers and arrays. Visit http://codeschool.org
From playlist The C language (unit 2)

Advanced Bitcoin Scripting -- Part 1: Transactions & Multisig
This is the first part of a more technical talk where Andreas explores Bitcoin script, with examples from the 2nd edition of Mastering Bitcoin, focusing on the use of conditional statements, flow control, guard clauses and time locks. The examples will include advanced multi-signature scri
From playlist Bitcoin Talks by Andreas M. Antonopoulos

Life Onboard The Drug-Busting HMCS Calgary | Warships | Spark
A powerful naval task group has sailed east from ports in Canada to one of the most lawless maritime regions in the world: the Persian Gulf. As a part of a six-part HD documentary series, we follow the daily events and real-life stories of the brave men and women living and working to kee
From playlist Warships

Defending against PowerShell attacks - in theory, and in practice by Lee holmes
Learn how attackers are using PowerShell and how to defend against those attacks.
From playlist PowerShell + DevOps Global Summit 2018

Defending against PowerShell attacks - in theory, and in practice by Lee holmes
Defending against PowerShell attacks - in theory, and in practice by Lee holmes
From playlist PowerShell + DevOps Global Summit 2018

James Kraska “China’s Maritime Militia and International Maritime Law”
James Kraska, U.S. Naval War College. Presented at Conflict in the South China Sea, May 6-7, 2016. An international conference at Yale exploring the history of the ongoing dispute in the South China Sea, featuring speakers from universities and research institutions in Australia, Britain,
From playlist Conflict in the South China Sea, May 6-7, 2016

Rails Conf 2013 Lightning Talks
Help us caption & translate this video! http://amara.org/v/FG9z/
From playlist Rails Conf 2013

PyCon PL 2015: Gynvael Coldwind "Python in a hacker's toolbox"
A classical language set used by a security specialist included assembly and C, sometimes joined by C++ and usually quite a lot of Bash as well. A few years ago it seemed that Perl, and later Ruby, will become the scripting language of choice in the security field, however another contende
From playlist Gynvael's [EN] Talks and Interviews

Micro Militaries - Europe's Tiniest Armies
In modern Europe there are a handful of micro-states, really tiny countries, with equally tiny and archaic armies. Dr. Mark Felton is a well-known British historian, the author of 22 non-fiction books, including bestsellers 'Zero Night' and 'Castle of the Eagles', both currently being de
From playlist Unusual Military Units

PROG2006: Haskell - basic function syntax, pattern matching, guards.
PROG2006 Advanced Programming Haskell: Basics of functions, syntax. Let/in, where, guards, pattern matching. Simple programming katas. Testing with Hspec. Examples/documentation testing.
From playlist PROG2006 - Programming
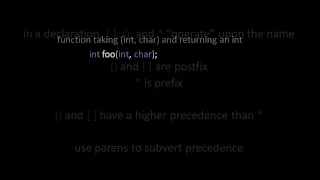
Introduction to the C programming language. Part of a larger series teaching programming. See http://codeschool.org
From playlist The C language

ElixirDaze 2017- Lets Generate Tests by Chris Keathley
ElixirDaze 2017- Lets Generate Tests by Chris Keathley
From playlist ElixirDaze 2017