Fundamental concepts of intrusion detection are discussed. Various types of intrusion are analyzed. Password management is explained.
From playlist Network Security

Latches and Flip-Flops 3 - The Gated D Latch
This is the third in a series of videos about latches and flip-flops. These bi-stable combinations of logic gates form the basis of computer memory, counters, shift registers, and more. In particular, this video covers the gated D latch, otherwise known as the data latch or simply the D
From playlist Latches and Flip-Flops

Fundamental concepts of intrusion detection are discussed. Various types of intrusion are analyzed. Password management is explained.
From playlist Network Security

Latches and Flip-Flops 2 - The Gated SR Latch
This is the second in a series of computer science videos about latches and flip-flops. These bi-stable combinations of logic gates form the basis of computer memory, counters, shift registers, and more. In particular, this video covers the gated set-reset latch. It begins by reviewing
From playlist Latches and Flip-Flops

What Is Intrusion Detection System? | Intrusion Detection System (IDS) | Cyber Security |Simplilearn
🔥Advanced Executive Program In Cybersecurity: https://www.simplilearn.com/pgp-advanced-executive-program-in-cyber-security?utm_campaign=WhatIsIntrusionDetectionSystem&utm_medium=Descriptionff&utm_source=youtube 🔥Caltech Cybersecurity Bootcamp(US Only): https://www.simplilearn.com/cybersecu
From playlist Cyber Security Playlist [2023 Updated]🔥

Latches and Flip-Flops 4 – The Clocked D Latch
This is the fourth in a series of videos about latches and flip-flops. These bi-stable combinations of logic gates form the basis of computer memory, counters, shift registers, and more. In particular, this video covers the clocked D latch, that is, a D latch controlled by a computer clo
From playlist Latches and Flip-Flops

Vacuum Tube Computer P.13 – Building a NAND Gate to Control the Input Enable Register
In this episode we start work on building the unit that’s going to connect the instruction register with the ALU. But, in order to do so, we need to build one more type of logic gate – the NAND gate. So come along as we take a look at the gates we’ve used so far and how we’re going to go a
From playlist Vacuum Tube Computer

How do we use transistors to create switches that can transmit arbitrary signals, whether analog or digital? The answer is the transmission gate. Also known as "pass transistor logic", the transmission gate allow for signals to be passed through or blocked depending on the control signal t
From playlist Digital Electronics

24C3: Why Silicon-Based Security is still that hard: Deconstructing Xbox 360 Security
Speakers: Michael Steil, Felix Domke Console Hacking 2007 The Xbox 360 probably is the video game console with the most sophisticated security system to date. Nevertheless, is has been hacked, and now Linux can be run on it. This presentation consists of two parts. In the first par
From playlist 24C3: Full steam ahead

#BrianGreene #Neuroscience #Brain How does the brain retrieve memories, articulate words, and focus attention? Recent advances have provided a newfound ability to decipher, sharpen, and adjust electrical signals relevant to speech, attention, memory and emotion. Join Brian Greene and leadi
From playlist WSF Latest Releases

DeepSec 2011: Windows Pwn 7 OEM - Owned Every Mobile?
Speaker: Alex Plaskett The talk aims to provide an introduction into the Windows Phone 7 (WP7) security model to allow security professionals and application developers understand the unique platform security features offered. Currently very little public information is available about Wi
From playlist DeepSec 2011

Disruptive technologies uproot culture, can precipitate wars and even topple empires. By this measure, human history has seen nothing like the Internet. Pioneers of the digital revolution examine the Internet’s brief but explosive history and reveal nascent projects that will shortly reinv
From playlist Technology

Bitcoin: Money As A Content Type and the Grand Arc of Technology
In this talk, Andreas discusses the evolution of technology along a "grand arc", from grandiosity, to... grandparents. He also looks at how bitcoin expresses money as a content type, changing the nature of payments into a form of generic communication. Chapters 0:00 Introduction 0:57 Bitc
From playlist English Subtitles - aantonop Videos with subtitles in English

Black Hat USA 2010: The Emperor Has No Clothes: Insecurities in Security Infrastructure 3/4
Speakers: Ben Feinstein, Jeff Jarmoc, Dan King Your security infrastructure (firewalls, IDS/IPS devices, management consoles, etc.) holds a very sensitive position of trust. This equipment is relied upon to reliably perform security critical functions under potentially hostile conditions.
From playlist Black Hat USA 2010

O'Reilly Webcast: OS X Mountain Lion and iPhone 5: Pogue's Take
David Pogue, author of OS X Mountain Lion: The Missing Manual and the upcoming iPhone: The Missing Manual, 6th Ed., is deeply immersed in Apple's latest. He's ready to share the juiciest morsels of Lionized goodness. And David will also share his thoughts on the new iPhone 5 and IOS 6. Ple
From playlist O'Reilly Webcasts 2

Ethereum Q&A: What Happens if there are Bugs?
What happens if there are bugs in Ethereum smart contracts? Are smart contract developers the new middlemen? What happened during the Bancor hack? Are Ethereum smart contracts and tokens secure? Could someone make centralised contracts still based on the ERC-20 standard? Chapters 0:00 Wha
From playlist English Subtitles - aantonop Videos with subtitles in English

This Australian encryption ban is the dumbest law in history
Australia just declared end-to-end encryption illegal by requiring companies to provide access to plain text communications through a new Assistance and Access Bill that passed just before Christmas. This is a dangerous attack on the Internet freedom. The Assistance and Access Bill, known
From playlist Decrypted Lies

Decentralised public key infrastructure
Speaker - Tim Hobson, The Alan Turing Institute About the event This hybrid conference brought together prominent academics and key players in the field of digital identity from government and industry sectors. The event focused on the socio-technical infrastructure opportunities and ch
From playlist Turing trustworthy digital identity international conference 2022
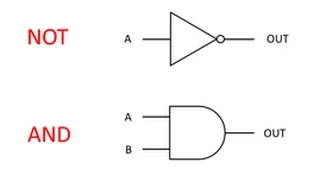
This is a beginner's introduction to logic gates. It starts with an historical mention of the development of two state devices including valves and transistors, and how these led to the silicon chip. It then goes on to describe the nature and behaviour of the three main logic gates NOT, A
From playlist Logic Gates