
In this video, you’ll learn more about formatting text in Word 2010. Visit https://www.gcflearnfree.org/word2010/formatting-text/1/ for our text-based lesson. This video includes information on: • Changing the font and font color • Highlighting text • Using the Bold, Italic, and Underline
From playlist Microsoft Word 2010

Excel - Number Formatting Secrets - Podcast 2044
Microsoft Excel - Number Formatting Secrets. Number formatting is a façade: Excel stores one thing, shows us another. For example: use decrease decimals to show a rounded version of the number. Excel still stores all of the decimals, but simplifies the display. There are 11 number formats
From playlist Full Advanced Excel Course - Free

Excel - Replace Destroys Formatting - Podcast 2054
Today's trick is from Katie Sullivan on the Word team There are a few cases where Microsoft Word can do things better than Excel It is possible in Excel to format part of a cell by selecting a word in Edit mode and applying formatting. But, if you use Find & Replace and anything is changed
From playlist Full Advanced Excel Course - Free

Excel 2007: Customize Your Spreadsheet
In this video, you’ll learn more about formatting text and customizing your spreadsheet in Excel 2007. Visit https://www.gcflearnfree.org/excel2007/formatting-text/1/ for our text-based lesson. This video includes information on: • Using the Bold, Italic, and Underline commands • Changing
From playlist Microsoft Excel 2007

Excel Tutorial - Customizing numeric formats
Learn tips for creating your numeric formats in Excel. Explore more Microsoft Excel courses and advance your skills on LinkedIn Learning: https://www.linkedin.com/learning/topics/microsoft-excel?trk=sme-youtube_M140599-02-01_learning&src=yt-other This is an excerpt from "Excel 2016: Advan
From playlist Microsoft Excel

How To Convert PDF To Excel | PDF To Excel Conversion | Import PDF To Excel | Simplilearn
This video is based on PDF to Excel Conversion. In multiple scenarios, you might have to Import PDF to Excel for storing PDF data in the form of an Excel Table. In this Excel tutorial, We will help you to learn how to convert PDF to Excel in a step by step way. This video will include the
From playlist Microsoft Excel Tutorial Videos 🔥[2022 Updated]

How To Convert PDF To Excel | PDF To Excel Conversion | Import PDF To Excel | Simplilearn
This video is based on PDF to Excel Conversion. In multiple scenarios, you might have to Import PDF to Excel for storing PDF data in the form of an Excel Table. In this Excel tutorial, We will help you to learn how to convert PDF to Excel in a step by step way. This video will include the
From playlist Microsoft Excel Tutorial Videos 🔥[2022 Updated]

Excel Busn Math 04: The Importance Of Formatting In Math
Download Excel Start File: https://people.highline.edu/mgirvin/YouTubeExcelIsFun/Busn135Ch00.xls Download Excel Finished File: https://people.highline.edu/mgirvin/YouTubeExcelIsFun/Busn135Ch00Finished.xls Learn about formatting in Excel and how it affects Math Calculations. See Currency, N
From playlist Excel Payroll & Time Tricks

Kernel Recipes 2018 - TPM enabling the Crypto Ecosystem for enhanced Security - James Bottomley
For decades, all laptops have come with a TPM. Now with Microsoft forcing the transition to the next generation, Linux faces a challenge in that all the previous TPM 1.2 tools don’t work with 2.0. Having to create new tools for TPM 2.0 also provides the opportunity to integrate the TPM
From playlist Kernel Recipes 2018

DeepSec 2007: Doppelgänger - novel protection against unknown file format vulnerabilities
Thanks to the DeepSec organisation for making these videos available and let me share the videos on YouTube. Speaker: Rich Smith, Hewlett-Packard Labs, Trusted Systems Lab The presentation intends to discuss the development of a general technique for protection against unknown threats t
From playlist DeepSec 2007

In this video, you’ll learn more about formatting text in Word 2013. Visit https://www.gcflearnfree.org/word2013/formatting-text/1/ for our text-based lesson. This video includes information on: • Changing the font size and color • Using the Bold, Italic, and Underline commands • Changing
From playlist Microsoft Word 2013

Black Hat USA 2010: Voyage of the Reverser: A Visual Study of Binary Species 3/5
Speakers: Greg Conti, Sergey Bratus When analyzing large binary objects such as process memory dumps, proprietary data files, container file formats, and network flow payloads, security researchers are limited by the tiny textual window a hex editor and common command line utilities typic
From playlist REVERSE ENGINEERING REDUX
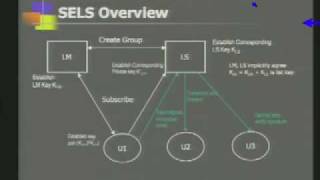
CERIAS Security: Minimizing Trust Liabilities in Secure Group Messaging Infrastructures 2/5
Clip 2/5 Speaker: Himanshu Khurana · University of Illinois at Urbana-Champaign Large-scale collaborative applications are characterized by a large number of users and other processing end entities that are distributed over geographically disparate locations. Therefore, these applicat
From playlist The CERIAS Security Seminars 2005 (1)

Symmetric Key Cryptography And Asymmetric Key Cryptography | Cryptography Tutorial | Simplilearn
🔥Advanced Executive Program In Cybersecurity: https://www.simplilearn.com/pgp-advanced-executive-program-in-cyber-security?utm_campaign=SymmetricKeyCryptographyAndAsymmetricKeyCryptography&utm_medium=Descriptionff&utm_source=youtube 🔥Caltech Cybersecurity Bootcamp(US Only): https://www.sim
From playlist Cyber Security Playlist [2023 Updated]🔥

Privacy-Preserving Machine Learning with Fully Homomorphic Encryption
A Google TechTalk, presented by Jordan Fréry, 2023-01-17 ABSTRACT: In today's digital age, protecting privacy has become increasingly difficult. However, new developments such as Fully Homomorphic Encryption (FHE) provide a means of safeguarding sensitive client information. We are excite
From playlist Differential Privacy for ML

Top Hashing Algorithms In Cryptography | MD5 and SHA 256 Algorithms Explained | Simplilearn
In this video on Top Hashing Algorithms In Cryptography, we will cover the technical aspects of hashing while going through some well-known hash functions and algorithms at the end. We cover the basics of cryptography and its applications. We also have detailed MD5 and SHA265 Explained sec
From playlist Cyber Security Playlist [2023 Updated]🔥

AES and DES Algorithm Explained | Difference between AES and DES | Network Security | Simplilearn
In today's video on AES and DES algorithm explained, we cover a major aspect of network security in encryption standards.The origins and working of both the data encryption standard and advanced encryption standard are covered. We also look into the applications and differences between AES
From playlist Cyber Security Playlist [2023 Updated]🔥

29C3: The future of protocol reversing and simulation applied on ZeroAccess botnet (EN)
Speakers: Frédéric Guihéry | Georges Bossert Mapping your enemy Botnet with Netzob Have you ever been staring for nights at binary or hexadecimal data flows extracted from an USB channel? Don't you remember yourself searching for some patterns and similarities in this fuc*g mess of zeros
From playlist 29C3: Not my department

Convert Text to Time Values with Text Functions (Data Cleansing Part 1)
Sign up for our Excel webinar, times added weekly: https://www.excelcampus.com/blueprint-registration/ This is the first video in a series of solutions for our Data Cleansing Challenge. In this video I explain how to use text functions to convert the time stored as text into numeric time
From playlist Tips & Shortcuts

Linear Algebra 15p: The Inverse of a Linear Transformation
https://bit.ly/PavelPatreon https://lem.ma/LA - Linear Algebra on Lemma http://bit.ly/ITCYTNew - Dr. Grinfeld's Tensor Calculus textbook https://lem.ma/prep - Complete SAT Math Prep
From playlist Part 3 Linear Algebra: Linear Transformations