
Extended Fundamental Theorem of Calculus
Please Subscribe here, thank you!!! https://goo.gl/JQ8Nys Extended Fundamental Theorem of Calculus. You can use this instead of the First Fundamental Theorem of Calculus and the Second Fundamental Theorem of Calculus. - Formula - Proof sketch of the formula - Six Examples
From playlist Calculus

12_1_1 Introduction to Taylor Polynomials
An introduction to expand a function into a Taylor polynomial.
From playlist Advanced Calculus / Multivariable Calculus

C34 Expanding this method to higher order linear differential equations
I this video I expand the method of the variation of parameters to higher-order (higher than two), linear ODE's.
From playlist Differential Equations

12_2_1 Taylor Polynomials of Multivariable Functions
Now we expand the creation of a Taylor Polynomial to multivariable functions.
From playlist Advanced Calculus / Multivariable Calculus

Euler's method for solving non-separable differential equation by approximation.
From playlist Advanced Calculus / Multivariable Calculus

[Calculus] Newton's Method || Lecture 36
Visit my website: http://bit.ly/1zBPlvm Subscribe on YouTube: http://bit.ly/1vWiRxW Hello, welcome to TheTrevTutor. I'm here to help you learn your college courses in an easy, efficient manner. If you like what you see, feel free to subscribe and follow me for updates. If you have any que
From playlist Calculus 1

Calculus: Newton's Method uses tangent lines to approximate the zeros of a function. We estimate sqrt(3), derive the method, and note some issues with its application.
From playlist Calculus Pt 1: Limits and Derivatives

HAR 2009: Flipping the Phishing Con Game - Design and Implementation of FishPhucker 5/5
Clip 5/5 Speaker: Dominik Birk Anti-Phishing Extension Numerous counter-measures against phishing have been evaluated in recent years. Users have been educated; authenticity in Bank websites was improved and out-of-band authentication methods were established, but phishing remains
From playlist Hacking at Random (HAR) 2009
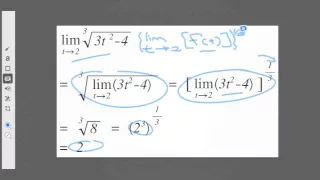
4 Calculating some interesting limits
Now that we have got the ball rolling, let's do some examples.
From playlist Life Science Math: Limits in calculus

HAR 2009: Flipping the Phishing Con Game - Design and Implementation of FishPhucker 2/5
Clip 2/5 Speaker: Dominik Birk Anti-Phishing Extension Numerous counter-measures against phishing have been evaluated in recent years. Users have been educated; authenticity in Bank websites was improved and out-of-band authentication methods were established, but phishing remains
From playlist Hacking at Random (HAR) 2009

Differential Equations | Exact Equations and Integrating Factors Example 2
We give an example of converting a non-exact differential equation into an exact equation. We use this to solve the differential equation.
From playlist Numerical Methods for Differential Equations

HAR 2009: Flipping the Phishing Con Game - Design and Implementation of FishPhucker 4/5
Clip 4/5 Speaker: Dominik Birk Anti-Phishing Extension Numerous counter-measures against phishing have been evaluated in recent years. Users have been educated; authenticity in Bank websites was improved and out-of-band authentication methods were established, but phishing remains
From playlist Hacking at Random (HAR) 2009

Sriram Sankararaman: "Evolutionary Models in Population Genomics"
Computational Genomics Summer Institute 2016 "Evolutionary Models in Population Genomics" Sriram Sankararaman, UCLA Institute for Pure and Applied Mathematics, UCLA July 22, 2016 For more information: http://computationalgenomics.bioinformatics.ucla.edu/
From playlist Computational Genomics Summer Institute 2016

HAR 2009: Flipping the Phishing Con Game - Design and Implementation of FishPhucker 1/5
Clip 1/5 Speaker: Dominik Birk Anti-Phishing Extension Numerous counter-measures against phishing have been evaluated in recent years. Users have been educated; authenticity in Bank websites was improved and out-of-band authentication methods were established, but phishing remains
From playlist Hacking at Random (HAR) 2009

6. Maximum Likelihood Estimation (cont.) and the Method of Moments
MIT 18.650 Statistics for Applications, Fall 2016 View the complete course: http://ocw.mit.edu/18-650F16 Instructor: Philippe Rigollet In this lecture, Prof. Rigollet continued on maximum likelihood estimators and talked about Weierstrass Approximation Theorem (WAT), and statistical appli
From playlist MIT 18.650 Statistics for Applications, Fall 2016

ICTS Special Colloquium by Bruce Walsh
Second Bangalore School on Population Genetics and Evolution URL: http://www.icts.res.in/program/popgen2016 DESCRIPTION: Just as evolution is central to our understanding of biology, population genetics theory provides the basic framework to comprehend evolutionary processes. Population
From playlist Second Bangalore School on Population Genetics and Evolution

Toeplitz Matrices and Determinants Under the Impetus of the Ising Model - Percy Deift
Percy Deift Courant Institute, NYU January 28, 2013 This is the first of two talks in which the speaker will discuss the development of the theory of Toeplitz matrices and determinants in response to questions arising in the analysis of the Ising model of statistical mechanics. The first t
From playlist Mathematics

HAR 2009: Flipping the Phishing Con Game - Design and Implementation of FishPhucker 3/5
Clip 3/5 Speaker: Dominik Birk Anti-Phishing Extension Numerous counter-measures against phishing have been evaluated in recent years. Users have been educated; authenticity in Bank websites was improved and out-of-band authentication methods were established, but phishing remains
From playlist Hacking at Random (HAR) 2009

[RoBERT & ToBERT] Hierarchical Transformers for Long Document Classification | AISC
For slides and more information on the paper, visit https://aisc.ai.science/events/2019-12-02 Discussion lead: Salman Ali
From playlist Natural Language Processing

Ex: Newton's Method to Approximate Zeros -- 2 Iterations
This video provides an example of how to approximate zeros or roots of a polynomial equation using Newton's Method. Two iterations are provided. Site: http://mathispower4u.com
From playlist Newton’s Method and L’Hopital’s Rule