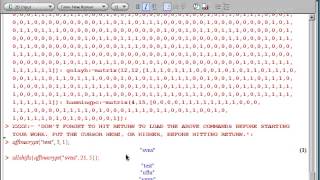
Advanced Access Content System
Encrypted Title Key
Encrypted Title Key is an encrypted key that belongs to anticopy Advanced Access Content System (AACS). This key is included in the Media Key Block system and is an important part of the content protection process of Blu-ray and HD-DVD contents. (Wikipedia).