Link: https://www.geogebra.org/m/ATnqfej6
From playlist Geometry: Dynamic Interactives!

Isosceles Triangle Theorems: Dynamic Illustrations WITHOUT WORDS or NUMBERS
Link: https://www.geogebra.org/m/Au4rzFcJ BGM: Andy Hunter
From playlist Geometry: Dynamic Interactives!
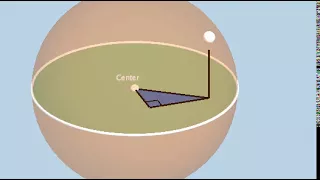
Link: https://www.geogebra.org/m/D4hmNy9M
From playlist 3D: Dynamic Interactives!
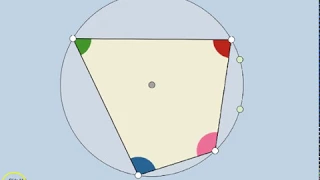
Inscribed Angle Theorems + Corollaries!
Links: https://www.geogebra.org/m/kxgHfpBT#chapter/65779
From playlist Geometry: Dynamic Interactives!

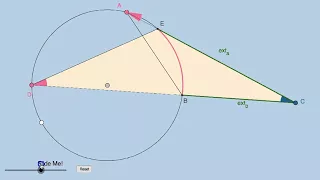
Exterior Angles of Polygons: Revisited
Link: https://www.geogebra.org/m/xDrd5X3w
From playlist Geometry: Dynamic Interactives!
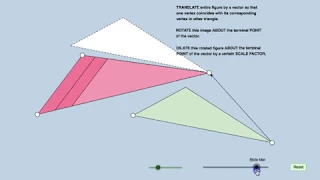
Similar Figures Definition: Dynamic Illustration
Link: https://www.geogebra.org/m/EeXdSpJB
From playlist Geometry: Dynamic Interactives!
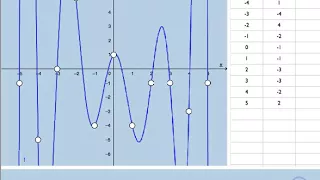
Quiz: Composition of Functions (Graph & Table)
Link: https://www.geogebra.org/m/QgN7nwCh
From playlist Algebra 1: Dynamic Interactives!

Live Meetup - Running HashiCorp Vault on Kubernetes
Broadcasted live on Twitch -- Watch live at https://www.twitch.tv/brookzerker
From playlist Denver Node.js meetup
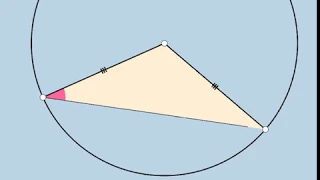
Isosceles Triangle: Dynamic Illustrations without Words
GeoGebra Resource Link: https://www.geogebra.org/m/Au4rzFcJ
From playlist Geometry: Dynamic Interactives!
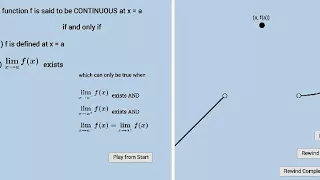
Continuity Definnition: Dynamic Illustration
Link: https://www.geogebra.org/m/xeA7M94B
From playlist Calculus: Dynamic Interactives!

DEFCON 16: Snort Plug-in Development: Teaching an Old Pig New Tricks
Speaker: Ben Feinstein, Security Researcher, SecureWorks Counter Threat Unit Snort has become a standard component of many IT security environments. Snort is mature and widely deployed, and is no longer viewed as new or exciting by the industry. However, with such widespread deployment, e
From playlist DEFCON 16

DevOpsDays Silicon Valley 2018 - Modern Security With Microservices And The Cloud by Seth Vargo
DevOpsDays Silicon Valley 2018 Modern Security With Microservices And The Cloud by Seth Vargo
From playlist DevOpsDays Silicon Valley 2018

Electric Circuits with Relays and with Wolfram Mathematica and Cloud
In this talk, Milana Santos talks about designing online courseware for electrical engineering students using the Wolfram Language and the Wolfram Cloud. At Polytechnical School of Universidade de São Paulo, most courses about electrical circuits and equipment are accomplished by practical
From playlist Wolfram Technology Conference 2020
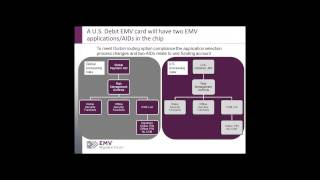
EMV 101: Fundamentals of EMV Chip Payment
Commonly used globally in place of magnetic stripe, EMV chip technology helps to reduce card fraud in a face-to-face card-present environment; provides global interoperability; and enables safer and smarter transactions across contact and contactless channels. EMV implementation was initia
From playlist Payments

CERIAS Security: Dynamic and Efficient Key Management for Access Hierarchies 3/6
Clip 3/6 Speaker: Marina Blanton · Purdue University Hierarchies arise in the context of access control whenever the set of users can be modeled as a set of partially ordered classes (i.e., represented as a directed graph). In such systems, a user that belongs to a particular class in
From playlist The CERIAS Security Seminars 2006

Kubernetes Live - 1 | Kubernetes Tutorial For Beginners | Kubernetes Training | Edureka
🔥Kubernetes Certification Training: https://www.edureka.co/kubernetes-certification This Edureka video will help you understand the most popular orchestration tool which is known as Kubernetes. 🔹DevOps Tutorial Blog Series: https://goo.gl/P0zAfF -----------------------------------------
From playlist Edureka Live Classes 2020

DevOpsDays Boston 2018 - Vault At Scale by Matt Surabian
DevOpsDays Boston 2018 - Vault At Scale by Matt Surabian As an organization with 25 production environments and over 6,000 containerized applications we have a lot of secrets to manage. Enough to run 12 geographically distributed HA Vault deployments across multiple cloud providers. Even
From playlist DevOpsDays Boston 2018

Notebooks and CDFs as Learning Support for an Engineering Course
To learn more about Wolfram Technology Conference, please visit: https://www.wolfram.com/events/technology-conference/ Speaker: Milana Santos Wolfram developers and colleagues discussed the latest in innovative technologies for cloud computing, interactive deployment, mobile devices, and
From playlist Wolfram Technology Conference 2018

GTAC 2013: Testing for Educational Gaming and Educational Gaming for Testing
http://g.co/gtac2013 Slides: http://goo.gl/wb3nm Tao Xie, North Carolina State University This talk presents Pex4Fun (http://www.pexforfun.com/), which leverages automated test generation to underpin automatic grading in an online programming system that can scale to hundreds of thousand
From playlist GTAC 2013
Vertical Angles Theorem (Interactive Student Discovery Without Words)
Link: https://www.geogebra.org/m/TY7ex9B9
From playlist Geometry: Dynamic Interactives!