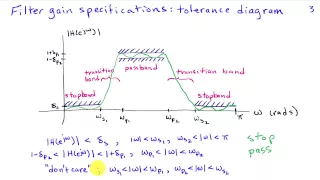
Introduction to Frequency Selective Filtering
http://AllSignalProcessing.com for free e-book on frequency relationships and more great signal processing content, including concept/screenshot files, quizzes, MATLAB and data files. Separation of signals based on frequency content using lowpass, highpass, bandpass, etc filters. Filter g
From playlist Introduction to Filter Design

Quantization and Coding in A/D Conversion
http://AllSignalProcessing.com for more great signal-processing content: ad-free videos, concept/screenshot files, quizzes, MATLAB and data files. Real sampling systems use a limited number of bits to represent the samples of the signal, resulting in quantization of the signal amplitude t
From playlist Sampling and Reconstruction of Signals
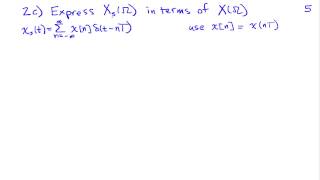
Frequency Domain Interpretation of Sampling
http://AllSignalProcessing.com for more great signal-processing content: ad-free videos, concept/screenshot files, quizzes, MATLAB and data files. Analysis of the effect of sampling a continuous-time signal in the frequency domain through use of the Fourier transform.
From playlist Sampling and Reconstruction of Signals

Primitive Roots - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Data Compression: Run Length Encoding (RLE)
This computer science video is about the lossless data compression technique known as Run Length Encoding (RLE). It begins by mentioning the benefits of data compression, and the difference between lossy and lossless compression formats. It then explains how the technique of run length e
From playlist Images

Key Distribution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

An intro to the core protocols of the Internet, including IPv4, TCP, UDP, and HTTP. Part of a larger series teaching programming. See codeschool.org
From playlist The Internet

WebAssembly: The What, Why and How
WebAssembly is a portable, size, and load-time efficient binary format for the web. It is an emerging standard being developed in the WebAssembly community group, and supported by multiple browser vendors. This talk details what WebAssembly is, the problems it is trying to solve, exciting
From playlist Talks
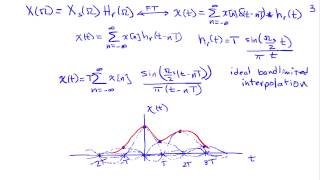
Reconstruction and the Sampling Theorem
http://AllSignalProcessing.com for more great signal-processing content: ad-free videos, concept/screenshot files, quizzes, MATLAB and data files. Analysis of the conditions under which a continuous-time signal can be reconstructed from its samples, including ideal bandlimited interpolati
From playlist Sampling and Reconstruction of Signals

Publishing (Perfect) Python Packages on PyPi
Always wanted to publish a package on PyPI, but didn't know where to start? This talk is for you! Starting with nothing, we'll build a package and publish it on PyPI using current best practices. Learn how to structure your project and your code. Discover what goes in your coderequirement
From playlist Python

DjangoCon US 2018 - Packaging Django Apps for Distribution on PyPI by Laura Hampton
DjangoCon US 2018 - Packaging Django Apps for Distribution on PyPI by Laura Hampton One of the strengths of Django is that it allows you to use apps created by other developers, so you don’t have to spend time rewriting something that someone else has already written. However, creating Py
From playlist DjangoCon US 2018

Huffman Codes: An Information Theory Perspective
Huffman Codes are one of the most important discoveries in the field of data compression. When you first see them, they almost feel obvious in hindsight, mainly due to how simple and elegant the algorithm ends up being. But there's an underlying story of how they were discovered by Huffman
From playlist Data Compression
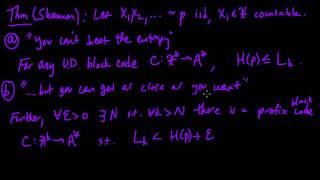
(IC 3.9) Source coding theorem (optimal lossless compression)
Proof of Shannon's "Source coding theorem", characterizing the entropy as the best possible lossless compression (using block codes) for a discrete memoryless source. A playlist of these videos is available at: http://www.youtube.com/playlist?list=PLE125425EC837021F
From playlist Information theory and Coding

(IC 3.7) Block codes for compression
Introduction to the idea of encoding a sequence of source symbols using blocks, rather than a single symbol at a time. A playlist of these videos is available at: http://www.youtube.com/playlist?list=PLE125425EC837021F
From playlist Information theory and Coding

Nexus Trimester - Joerg Kliewer (New Jersey Institute of Technology)
Lossy Compression with Privacy Constraints: Optimality of Polar Codes Joerg Kliewer (New Jersey Institute of Technology) April 01, 2016
From playlist Nexus Trimester - 2016 - Secrecy and Privacy Theme

(IC 5.10) Generalizing arithmetic coding to non-i.i.d. models
Arithmetic coding can accommodate essentially any probabilistic model of the source, in a very natural way. A playlist of these videos is available at: http://www.youtube.com/playlist?list=PLE125425EC837021F
From playlist Information theory and Coding

The Future Of Software Development
From autonomous vehicles, 3D printed rocket engines, and “affordable” consumer-owned satellites to rapid advances in AI and secure, decentralized electronic currencies, the past several years have shown us that the only prediction we can confidently make about the future is that it will ar
From playlist Software Development

2. Compression: Huffman and LZW
MIT 6.02 Introduction to EECS II: Digital Communication Systems, Fall 2012 View the complete course: http://ocw.mit.edu/6-02F12 Instructor: George Verghese This lecture covers examples of Huffman coding and limitations of coding. Lempel-Ziv-Welch is introduced as an adaptive variable-leng
From playlist MIT 6.02 Introduction to EECS II: Digital Communication Systems, Fall 2012

Randomness - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography
