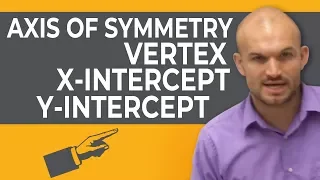
How to analyze a quadratic function to graph
👉 Learn the basics to understanding graphing quadratics. A quadratic equation is an equation whose highest exponent in the variable(s) is 2. To graph a quadratic equation, we make use of a table of values and the fact that the graph of a quadratic is a parabola which has an axis of symmetr
From playlist Graph a Quadratic in Standard Form | Essentials

How to determine the domain and range of a quadratic using its vertex
👉 Learn the basics to understanding graphing quadratics. A quadratic equation is an equation whose highest exponent in the variable(s) is 2. To graph a quadratic equation, we make use of a table of values and the fact that the graph of a quadratic is a parabola which has an axis of symmetr
From playlist Graph a Quadratic in Standard Form | Essentials

Finding the axis of symmetry for a parabola and graph
👉 Learn the basics to understanding graphing quadratics. A quadratic equation is an equation whose highest exponent in the variable(s) is 2. To graph a quadratic equation, we make use of a table of values and the fact that the graph of a quadratic is a parabola which has an axis of symmetr
From playlist Graph a Quadratic in Standard Form | Essentials

Sketching the graph of a polynomial using the zeros and multiplicity
👉 Learn how to use the tools needed to graph a polynomial function in factored form. A polynomial in factored form is when the polynomial is written as a product of its linear factors. Each linear factor represents an x-intercept and the power of the factor represents the multiplicity. Wh
From playlist Graph a Polynomial Function in Factored Form

Zeros, graphing, multiplicity polynomial
👉 Learn how to use the tools needed to graph a polynomial function in factored form. A polynomial in factored form is when the polynomial is written as a product of its linear factors. Each linear factor represents an x-intercept and the power of the factor represents the multiplicity. Wh
From playlist Graph a Polynomial Function in Factored Form

Differentially Private Algorithms: Some Primitives and Paradigms - Kunal Talwar
Differential Privacy Symposium: Four Facets of Differential Privacy Saturday, November 12, 2016 https://www.ias.edu/differential-privacy More videos on http://video.ias.edu
From playlist Differential Privacy Symposium - November 12, 2016

Learn how to graph the parent graph of a quadratic equation in standard form using a table
👉 Learn the basics to understanding graphing quadratics. A quadratic equation is an equation whose highest exponent in the variable(s) is 2. To graph a quadratic equation, we make use of a table of values and the fact that the graph of a quadratic is a parabola which has an axis of symmetr
From playlist Graph a Quadratic in Standard Form | Essentials

CERIAS Security: Safely Analyzing Sensitive Network Data 6/6
Clip 6/6 Speaker: Gerome Miklau · University of Massachusetts, Amherst Our recent work investigates the properties of a network that can be accurately studied without threatening the privacy of individuals and their connections. We adopt the rigorous condition of differential privacy, an
From playlist The CERIAS Security Seminars 2009

DP-SGD Privacy Analysis is Tight!
A Google TechTalk, presented by Milad Nasr, 2020/08/21 ABSTRACT: Differentially private stochastic gradient descent (DP-SGD) provides a method to train a machine learning model on private data without revealing anything specific to that particular dataset. As a tool, differential privacy
From playlist Differential Privacy for ML
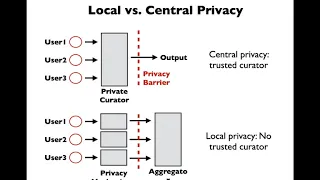
Profile-based Privacy for Locally Private Computations
A Google TechTalk, 2020/7/30, presented by Kamalika Chaudhuri, UCSD ABSTRACT: Differential privacy has emerged as a gold standard in privacy-preserving data analysis. A popular variant commonly used for federated learning is local differential privacy, where the data holder is the trusted
From playlist 2020 Google Workshop on Federated Learning and Analytics

CERIAS Security: Safely Analyzing Sensitive Network Data 5/6
Clip 5/6 Speaker: Gerome Miklau · University of Massachusetts, Amherst Our recent work investigates the properties of a network that can be accurately studied without threatening the privacy of individuals and their connections. We adopt the rigorous condition of differential privacy, an
From playlist The CERIAS Security Seminars 2009

Sketch the graph of the polynomial by hand using zeros, multiplicity and end behavior
👉 Learn how to use the tools needed to graph a polynomial function in factored form. A polynomial in factored form is when the polynomial is written as a product of its linear factors. Each linear factor represents an x-intercept and the power of the factor represents the multiplicity. Wh
From playlist Graph a Polynomial Function in Factored Form
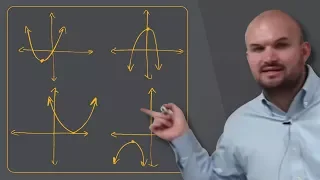
How do the solutions of a quadratic relate to the x intercepts of the graph
👉 Learn the basics to understanding graphing quadratics. A quadratic equation is an equation whose highest exponent in the variable(s) is 2. To graph a quadratic equation, we make use of a table of values and the fact that the graph of a quadratic is a parabola which has an axis of symmetr
From playlist Graph a Quadratic in Standard Form | Essentials

Determine the multiplicity and zeros and graph of a polynomial
👉 Learn how to use the tools needed to graph a polynomial function in factored form. A polynomial in factored form is when the polynomial is written as a product of its linear factors. Each linear factor represents an x-intercept and the power of the factor represents the multiplicity. Wh
From playlist Graph a Polynomial Function in Factored Form

Privacy-preserving algorithms for decentralised collaborative learning: Dr Aurélien Bellet
Short bio I am a tenured researcher at Inria, where I am part of the Magnet Team (MAchine learninG in information NETworks). I am also affiliated with CRIStAL (UMR CNRS 9189), a research center of the University of Lille. Prior to joining Inria, I was a postdoctoral researcher at the Uni
From playlist Turing Seminars

CERIAS Security: Safely Analyzing Sensitive Network Data 4/6
Clip 4/6 Speaker: Gerome Miklau · University of Massachusetts, Amherst Our recent work investigates the properties of a network that can be accurately studied without threatening the privacy of individuals and their connections. We adopt the rigorous condition of differential privacy, an
From playlist The CERIAS Security Seminars 2009

CERIAS Security: Safely Analyzing Sensitive Network Data 3/6
Clip 3/6 Speaker: Gerome Miklau · University of Massachusetts, Amherst Our recent work investigates the properties of a network that can be accurately studied without threatening the privacy of individuals and their connections. We adopt the rigorous condition of differential privacy, an
From playlist The CERIAS Security Seminars 2009

CERIAS Security: Safely Analyzing Sensitive Network Data 1/6
Clip 1/6 Speaker: Gerome Miklau · University of Massachusetts, Amherst Our recent work investigates the properties of a network that can be accurately studied without threatening the privacy of individuals and their connections. We adopt the rigorous condition of differential privacy, an
From playlist The CERIAS Security Seminars 2009

What is a reflection for a quadratic graph
👉 Learn the basics to understanding graphing quadratics. A quadratic equation is an equation whose highest exponent in the variable(s) is 2. To graph a quadratic equation, we make use of a table of values and the fact that the graph of a quadratic is a parabola which has an axis of symmetr
From playlist Graph a Quadratic in Standard Form | Essentials

Composition: The Key to Differential Privacy is Success - Guy Rothblum
Differential Privacy Symposium: Four Facets of Differential Privacy Saturday, November 12, 2016 https://www.ias.edu/differential-privacy More videos on http://video.ias.edu
From playlist Differential Privacy Symposium - November 12, 2016