
Nexus Trimester - Stephanie Wehner (Delft University of Technology)
Device-independence in quantum cryptography Stephanie Wehner (Delft University of Technology) March 22, 2016 Abstract: While quantum cryptography offers interesting security guarantees, it is challenging to build good quantum devices. In practise, we will therefore typically rely on devi
From playlist Nexus Trimester - 2016 - Secrecy and Privacy Theme

Quantum Cryptography in 6 Minutes
Quantum Cryptography explained simply. Regular encryption is breakable, but not quantum cryptography. Today we'll look at the simplest case of quantum cryptography, quantum key distribution. It uses the Heisenberg Uncertainty Principle to prevent eavesdroppers from cracking the code. Hi
From playlist Physics

Scientists from the Max Planck Institute for the Science of Light have hacked a commercial quantum cryptosystem. In quantum cryptosystems a secret key is shared between two parties. The security is based on the laws of quantum mechanics, whereas in classical schemes security relies only on
From playlist Most popular videos

Summary - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Primality (1 of 2: Fermat's Test)
From playlist Cryptography

Secure Computation Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Anne Broadbent - Information-Theoretic Quantum Cryptography Part 1 of 2 - IPAM at UCLA
Recorded 27 July 2022. Anne Broadbent of the University of Ottawa presents "Information-Theoretic Quantum Cryptography" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: These lectures are an introduction to the interplay between quantum information and cryp
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

Quantum Cryptography | CaltechX and DelftX on edX | Course About Video
Learn how quantum communication provides security that is guaranteed by the laws of nature. Take this course free on edX: https://www.edx.org/course/quantum-cryptography-caltechx-delftx-qucryptox#! ABOUT THIS COURSE How can you tell a secret when everyone is able to listen in? In this co
From playlist Research & Science

Quantum Technologies by Aditi De
KAAPI WITH KURIOSITY QUANTUM TECHNOLOGIES SPEAKER: Aditi De (HRI, Allahabad) WHEN: 3pm to 4pm Sunday, 16 June 2019 WHERE: J. N. Planetarium, Sri T. Chowdaiah Road, High Grounds, Bangalore The quantum theory of nature, formalized in the first few decades of the 20th century, contains e
From playlist Kaapi With Kuriosity (A Monthly Public Lecture Series)

Delegating computation via no-signaling strategies – Yael Kalai – ICM2018
Mathematical Aspects of Computer Science Invited Lecture 14.4 Delegating computation via no-signaling strategies Yael Kalai Abstract: Efficient verification of computation, also known as ‘delegation of computation’, is one of the most fundamental notions in computer science, and in parti
From playlist Mathematical Aspects of Computer Science

Entropy accumulation - O. Fawzi - Workshop 2 - CEB T3 2017
Omar Fawzi / 23.10.17 Entropy accumulation We ask the question whether entropy accumulates, in the sense that the operationally relevant total uncertainty about an n-partite system A=(A1,…An) corresponds to the sum of the entropies of its parts Ai. The Asymptotic Equipartition Property i
From playlist 2017 - T3 - Analysis in Quantum Information Theory - CEB Trimester

https://www.patreon.com/edmundsj If you want to see more of these videos, or would like to say thanks for this one, the best way you can do that is by becoming a patron - see the link above :). And a huge thank you to all my existing patrons - you make these videos possible. Quantum wells
From playlist Optoelectronic and Photonic Devices

IMS Public Lecture: Are Quantum Computers The Next Generation Of Supercomputers?
Reinhard Werner, Technische Universität Braunschweig, Germany
From playlist Public Lectures

True Randomness: Its Origin and Expansion - Yaoyun Shi
True Randomness: Its Origin and Expansion Yaoyun Shi University of Michigan April 21, 2014 How can we produce randomness of almost perfect quality, in large quantities, and under minimal assumptions? This question is fundamental not only to modern day information processing but also to phy
From playlist Mathematics
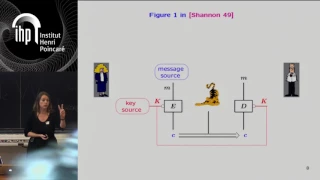
Shannon 100 - 26/10/2016 - Anne CANTEAUT
Comment concevoir un algorithme de chiffrement sûr et efficace : l'héritage de Shannon Anne Canteaut (INRIA) Dans son article fondateur publié en 1949 posant les fondements de la cryptographie, Claude Shannon a énoncé deux méthodes de conception visant à éviter les attaques statistiques
From playlist Shannon 100

Time-Independent Schrödinger Equation | Quantum Mechanics
In this video, we will talk about the time-independent Schrödinger equation in quantum mechanics. If we start with the time-dependent Schrödinger equation, we can get to the time-independent one by performing a separation of variables on the wave function, where we claim that the time depe
From playlist Quantum Mechanics, Quantum Field Theory

Stanford Seminar - Cryptology and Security: the view from 2016 - Whitfield Diffie
"Cryptology and Security: the view from 2016" - Whitfield Diffie, ACM 2015 Turing Award About the talk: On the face of it, the cryptographers have solved their piece of the puzzle but every other aspect of security, from crypto-implementations to operating systems to applications, stinks.
From playlist Engineering

