Coding Math: Episode 51 - Pseudo Random Number Generators Part I
Back to School Special. This short series will discuss pseudo random number generators (PRNGs), look at how they work, some algorithms for PRNGs, and how they are used. Support Coding Math: http://patreon.com/codingmath Source Code: https://jsbin.com/nifutup/1/edit?js,output Earlier Sourc
From playlist Episodes

Sources Of Randomness - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Pseudorandom Number Generation and Stream Ciphers
Fundamental concepts of Pseudorandom Number Generation are discussed. Pseudorandom Number Generation using a Block Cipher is explained. Stream Cipher & RC4 are presented.
From playlist Network Security
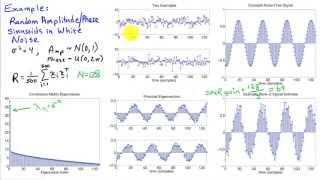
http://AllSignalProcessing.com for more great signal processing content, including concept/screenshot files, quizzes, MATLAB and data files. Representing multivariate random signals using principal components. Principal component analysis identifies the basis vectors that describe the la
From playlist Random Signal Characterization

Biased Generator - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Guenaëlle De Julis et Kévin Layat
Adjustements in Statistical Methodology for Testing Randomness of Physical Sources
From playlist Journées Codage et Cryptographie 2014

Prng Implementation - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Sonia Belaïd - Schémas symétriques prouvés sûrs contre les attaques par canaux auxiliaires
Schémas symétriques prouvés sûrs contre les attaques par canaux auxiliaires
From playlist Journées Codage et Cryptographie 2014

Nexus Trimester - David Woodruff (IBM Almaden) 2/2
New Algorithms for Heavy Hitters in Data Streams 2/2 David Woodruff (IBM Almaden) March 09, 2016 Abstract: An old and fundamental problem in databases and data streams is that of finding the heavy hitters, also known as the top-k, most popular items, frequent items, elephants, or iceberg
From playlist 2016-T1 - Nexus of Information and Computation Theory - CEB Trimester

Pseudorandom Generators for CCO[p]CCO[p] and the Fourier Spectrum... - Shachar Lovett
Shachar Lovett Institute for Advanced Study October 5, 2010 We give a pseudorandom generator, with seed length O(logn)O(logn), for CC0[p]CC0[p], the class of constant-depth circuits with unbounded fan-in MODpMODp gates, for prime pp. More accurately, the seed length of our generator is O(
From playlist Mathematics

A simple RL setup to find counterexamples to conjectures in mathematics: Adam Zsolt Wagner
Machine Learning for the Working Mathematician: Week Seven 7 April 2022 Adam Zsolt Wagner, A simple RL setup to find counterexamples to conjectures in mathematics Seminar series homepage (includes Zoom link): https://sites.google.com/view/mlwm-seminar-2022
From playlist Machine Learning for the Working Mathematician

Black Hat USA 2010: Understanding the Windows SMB NTLM Weak Nonce Vulnerability 3/5
Speakers: Hernan Ochoa, Agustin Azubel In February 2010, we found a vulnerability in the SMB NTLM Windows Authentication mechanism that have been present in Windows systems for at least 14 years (from Windows NT 4 to Windows Server 2008). You probably haven't heard about this vulnerabilit
From playlist BH USA 2010 - OS WARS

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Clip 5/7 Speaker: Erik Tews What has changed in DECT security after one year After dedected.org was published on 25C3, lots has changed in DECT security. For more information go to: http://events.ccc.de/congress/2009/Fahrplan/events/3648.en.html
From playlist 26C3: Here be dragons day 3
A Friendly Introduction to Generative Adversarial Networks (GANs)
Code: http://www.github.com/luisguiserrano/gans What is the simplest pair of GANs one can build? In this video (with code included) we build a pair of ONE-layer GANs which will generate some simple 2x2 images (faces). Grokking Machine Learning Book: https://www.manning.com/books/grokking-
From playlist Introduction to Deep Learning

22C3: Covert channels in TCP/IP: attack and defense
Speaker: Steven J. Murdoch Creation and detection of IP steganography for covert channels and device fingerprinting This talk will show how idiosyncrasies in TCP/IP implementations can be used to reveal the use of several steganography schemes, and how they can be fixed. The analysis can
From playlist 22C3: Private Investigations

Verónica Becher: Independence of normal words
Abstract : Recall that normality is a elementary form of randomness: an infinite word is normal to a given alphabet if all blocks of symbols of the same length occur in the word with the same asymptotic frequency. We consider a notion of independence on pairs of infinite words formalising
From playlist Logic and Foundations

Unity Tutorial | How To Create Physics Based Mobile Game In Unity | Session 11 | #unity | #gamedev
Don’t forget to subscribe! In this Unity game development tutorial, you will learn to create a Physics Based Mobile Game In Unity. This Unity tutorial is about the ways to make a Physics Based game for Mobile in Unity. The end product will be a full-fledged mobile game with touch contro
From playlist Create Physics Based Mobile Game In Unity

Randomness - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography