
Reliability 1: External reliability and rater reliability and agreement
In this video, I discuss external reliability, inter- and intra-rater reliability, and rater agreement.
From playlist Reliability analysis

Can You Validate These Emails?
Email Validation is a procedure that verifies if an email address is deliverable and valid. Can you validate these emails?
From playlist Fun

Unless you've been living under a rock for the past 30 years or so, you probably know what a fax machine is. For decades, fax machines were used worldwide as the main way of electronic document delivery. But this happened in the 1980s. Humanity has since developed far more advanced ways to
From playlist Security

Convincing Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Mod-01 Lec-36 The social construction of knowledge: Adaptation and Revolution
History of Economic Theory by Dr. Shivakumar, Department of Humanities and Social Sciences IIT Madras, For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist IIT Madras: History of Economic Theory | CosmoLearning.org Economics
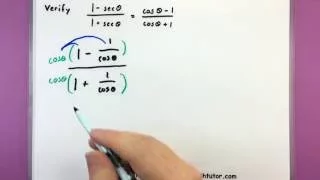
Trigonometry - Proving trig identities
Once you start getting a few more formulas and identities, you can use these to verify other identities. Watch this video for a few examples and some good tips when you have to verify a trigonometric identity. For more videos please visit http://www.mysecretmathtutor.com
From playlist Trigonometry

CERIAS Security: Protocols and Systems for Privacy Preserving Protection of Digital Identity 4/5
Clip 4/5 Speaker: Abhilasha Bhargav-Spantzel In this presentation I introduce a number of techniques that address the above problems. The approach is based on the concept of privacy preserving multi-factor identity verification. The main technique consists of verifying multiple identifie
From playlist The CERIAS Security Seminars 2007

I describe How to Detect a Liar. This information was created by combining info from numerous texts and figuring out what every expert agrees on. You'll learn to spot lying in men, women, politicans, etc.
From playlist Negotiation Tutorials
Trusted CI Webinar: SmartProvenance: A Distributed, Blockchain Based Data Provenance
Originally recorded February 26, 2018 Slides: http://hdl.handle.net/2142/99078 Blockchain technology has evolved from being an immutable ledger of transactions for cryptocurrencies to a programmable interactive environment for building distributed reliable applications. Although the bloc
From playlist Center for Applied Cybersecurity Research (CACR)

CERIAS Security: Protocols and Systems for Privacy Preserving Protection of Digital Identity 3/5
Clip 3/5 Speaker: Abhilasha Bhargav-Spantzel In this presentation I introduce a number of techniques that address the above problems. The approach is based on the concept of privacy preserving multi-factor identity verification. The main technique consists of verifying multiple identi
From playlist The CERIAS Security Seminars 2007

Fundamental concepts of intrusion detection are discussed. Various types of intrusion are analyzed. Password management is explained.
From playlist Network Security

Top 50 Software Testing Interview Questions & Answers | Software Testing Training | Edureka
** Test Automation Engineer Masters Program : https://www.edureka.co/masters-program/automation-testing-engineer-training ** This Edureka video on Top 50 Software Testing Interview Question and Answers will help you to prepare yourself for Software Testing Interviews. It covers questions f
From playlist Software Testing Training Videos | Edureka

Rolando Somma - The Quantum Linear Systems Problem - IPAM at UCLA
Recorded 24 January 2022. Rolando Somma of Los Alamos National Laboratory presents "The Quantum Linear Systems Problem" at IPAM's Quantum Numerical Linear Algebra Workshop. Abstract: The goal of the quantum linear systems problem (QLSP) is to prepare a quantum state proportional to the sol
From playlist Quantum Numerical Linear Algebra - Jan. 24 - 27, 2022

An Overview of EMV for the US Market
ACI Worldwide software powers electronic transactions for financial institutions, processors and retailers around the world - all the time, without fail. http://www.aciworldwide.com/emv ---------WEBINAR TRANSCRIPTION-------------- Today's topic is EMV: An Overview with Some US Considerat
From playlist Payments

CGSR | China’s Nuclear Modernization and its Implications | Tong Zhao
Recent open-source research reveals that China may be massively building up its nuclear forces at an unprecedented speed and scale in its history. Using publicly available information, this presentation will discuss potential drivers of China's nuclear modernization and how China's pursuit
From playlist Center for Global Security Research

Mod-01 Lec-32 Transaction cost and Economic Anthropology approaches
History of Economic Theory by Dr. Shivakumar, Department of Humanities and Social Sciences IIT Madras, For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist IIT Madras: History of Economic Theory | CosmoLearning.org Economics

Stanford Seminar - The Power of Visual Representations
Fanny Chevalier University of Toronto February 18, 2022 When designing visual content in user interfaces, it is crucial to recognize that the choice of the representations used to display information and concepts plays a critical role in how we perceive, interpret, learn and reason abou
From playlist Stanford Seminars

OWASP AppSec 2010: BitFlip: Determine a Data's Signature Coverage from Within the Application 2/2
Clip 2/2 Speaker: Henrich Christopher Poehls, University of Passau - ISL Despite applied cryptographic primitives applications are working on data that was not protected by them. We show by abstracting the message flow between the application and the underlying wire, that protection is
From playlist OWASP AppSec 2010

MIT 14.04 Intermediate Microeconomic Theory, Fall 2020 Instructor: Prof. Robert Townsend View the complete course: https://ocw.mit.edu/courses/14-04-intermediate-microeconomic-theory-fall-2020/ YouTube Playlist: https://www.youtube.com/watch?v=XSTSfCs74bg&list=PLUl4u3cNGP63wnrKge9vllow3Y2
From playlist MIT 14.04 Intermediate Microeconomic Theory, Fall 2020

CERIAS Security: Integrity for Outsourced Content Publishing and Database Queries 6/6
Clip 6/6 Speaker: Danfeng Yao · Brown University In outsourced content publishing, the data owner gives the content to a service provider who answers requests from users. Similarly, in outsourced databases, the data owner delegates a service provider to answer queries. Outsourcing ena
From playlist The CERIAS Security Seminars 2006