
Everything You Need to Know About Control Theory
Control theory is a mathematical framework that gives us the tools to develop autonomous systems. Walk through all the different aspects of control theory that you need to know. Some of the concepts that are covered include: - The difference between open-loop and closed-loop control - How
From playlist Control Systems in Practice
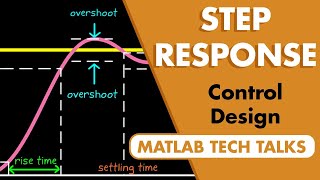
The Step Response | Control Systems in Practice
Check out the other videos in this series: https://www.youtube.com/playlist?list=PLn8PRpmsu08pFBqgd_6Bi7msgkWFKL33b This video covers a few interesting things about the step response. We’ll look at what a step response is and some of the ways it can be used to specify design requirements f
From playlist Control Systems in Practice
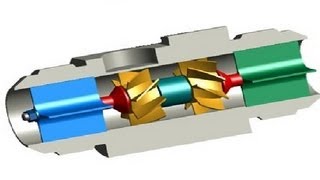
How to do flow test using flow meter in machines.
More details visit: http://www.HowmachineWorks.com/ Plz Join Our Face Book Page. http://www.facebook.com/pages/HowMachineWorks This video give you a clear idea about how to do a flow test using a flow meter on a hydraulic pump.
From playlist Hydraulics and related stuff.

Estimating Transfer Functions and Process Models
Get a Free Trial: https://goo.gl/C2Y9A5 Get Pricing Info: https://goo.gl/kDvGHt Ready to Buy: https://goo.gl/vsIeA5 Estimate continuous-time and discrete-time transfer functions and low-order process models. Use the estimate models for analysis and control design. For more videos, visit
From playlist Control System Design and Analysis
Transfer Functions: Introduction and Implementation
In this video we introduce transfer functions and show how they can be derived from a set of linear, ordinary differential equations. We also examine how to use a transfer function to predict the output of system to a given input. Topics and time stamps: 0:38 – Example using an aircraft
From playlist Control Theory
Nonlinear Plant Control at Different Operating Points
Design and analyze a controller for different operating points of a nonlinear plant simultaneously.For a free Control System toolbox Trial, visit: https://www.mathworks.com/programs/trials/trial_request.html?prodcode=CT&s_eid=PEP_12669 For more info on Control System Toolbox, visit: http:
From playlist Control System Design and Analysis

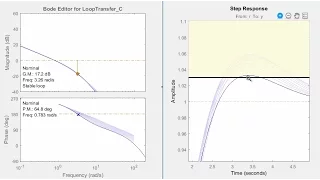
Working with Transfer Functions in MATLAB
Learn how to work with transfer functions using MATLAB® and Control System Toolbox™. This video demonstrates how you can create a transfer function to model a linear-time invariant system. Two transfer functions are combined to create a plant model. You can add a controller, and compute
From playlist Control System Design and Analysis

What Control Systems Engineers Do | Control Systems in Practice
The work of a control systems engineer involves more than just designing a controller and tuning it. Over the course of a project, designing the controller might be a relatively small part of your day-to-day job. Depending on the size and phase of the project, your responsibilities and the
From playlist Control Systems in Practice

CERIAS Security: Signature Analysis Coupled With Slicing Analysis for the Validation of Software 1/3
Clip 1/3 Speaker: Adam Dugger · Arxan What if you could determine exactly where, in any compiled binary, a security threat existed? Answering this question has been the fundamental goal of anti-virus software for many years past, with limited success. Instead, what if you could determin
From playlist The CERIAS Security Seminars 2008

mod-12 lec-12 General Control Valve Analysis
Fundamentals of Industrial Oil Hydraulics and Pneumatics by Prof. R.N. Maiti,Department of Mechanical Engineering,IIT Kharagpur.For more details on NPTEL visit http://nptel.ac.in
From playlist IIT Kharagpur: Fundamentals of Industrial Oil Hydraulics and Pneumatics (CosmoLearning Mechanical Engineering)

OWASP AppSecUSA 2012: Using Interactive Static Analysis for Detection of Software Vulnerabilities
Speaker: Bill Chu We present our work of using interactive static analysis to improve upon static analysis techniques by introducing a new mixed-initiative paradigm for interacting with developers to aid in the detection and prevention of security vulnerabilities. The key difference betwe
From playlist OWASP AppSecUSA 2012
What Are Non-Minimum Phase Systems? | Control Systems in Practice
Check out the other videos in the series: Part 1 - What Does a Controls Engineer Do? https://youtu.be/ApMz1-MK9IQ Part 2 - What Is Gain Scheduling? https://youtu.be/YiUjAV1bhKs Part 3 - What Is Feedforward Control? https://youtu.be/FW_ay7K4jPE Part 4 - Why Time Delay Matters https://youtu.
From playlist Control Systems in Practice
Laser: Static Analysis for Ruby, in Ruby by Michael Edgar
What truly makes Ruby special as a language is its focus on expressivity, flexibility, and dynamism. Yet these same properties - and their widespread use in the community - make even straightforward application code difficult to analyze statically in a meaningful way. Laser seeks to change
From playlist Ruby Conference 2011

mod-35 lec-37 Analysis of Three - Way (Spool and Flapper Nozzle Valve)
Fundamentals of Industrial Oil Hydraulics and Pneumatics by Prof. R.N. Maiti,Department of Mechanical Engineering,IIT Kharagpur.For more details on NPTEL visit http://nptel.ac.in
From playlist IIT Kharagpur: Fundamentals of Industrial Oil Hydraulics and Pneumatics (CosmoLearning Mechanical Engineering)
DEFCON 17: Binary Obfuscation from the Top-Down: Obfuscating Executables Without Writing Assembly
Speaker: Sean "Frank^2" Taylor Security Engineer, Rapid7 Binary obfuscation is commonly applied in malware and by software vendors in order to frustrate the efforts of reverse engineers to understand the underlying code. A common misconception is one must be a master of assembly in order
From playlist DEFCON 17

CERIAS Security: Signature Analysis Coupled With Slicing Analysis for the Validation of Software 2/3
Clip 2/3 Speaker: Adam Dugger · Arxan What if you could determine exactly where, in any compiled binary, a security threat existed? Answering this question has been the fundamental goal of anti-virus software for many years past, with limited success. Instead, what if you could determin
From playlist The CERIAS Security Seminars 2008

CERIAS Security: Information Sharing between Trustworthy and Untrustworthy Partners 4/7
Clip 4/7 Speaker: Bhavani Thuraisingham · The University of Texas at Dallas In summary, the presentation will provide an overview of data mining, the various types of threats and then discuss the applications of data mining for malicious code detection and cyber security. Then we will
From playlist The CERIAS Security Seminars 2007

27c3: Code deobfuscation by optimization (en)
Speaker: Branko Spasojevic Optimization algorithms present an effective way for removing most obfuscations that are used today. Much of the compiler theory can be applied in removing obfuscations and building fast and reliable deobfuscation systems. By understanding traditional optimizati
From playlist 27C3: We come in peace

Adobe Flash animation of a flow control valve. http://www.mekanizmalar.com/menu-pneumatic.html
From playlist Pneumatic and Hydraulics

GTAC 2015: Test Suites and Program Analysis
http://g.co/gtac Slides: https://docs.google.com/presentation/d/1yoOf_fyeN-AtQQQsTemxrranKVBUc9i-VzF_o4OqsJQ/pub Patrick Lam (University of Waterloo) Specializing static analysis techniques for test suites has yielded interesting results. We've previously learned that most tests are simp
From playlist GTAC 2015