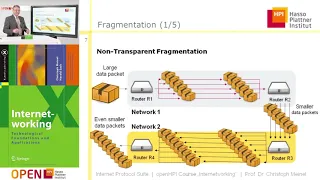
An intro to the core protocols of the Internet, including IPv4, TCP, UDP, and HTTP. Part of a larger series teaching programming. See codeschool.org
From playlist The Internet

Computer Basics 14: Content Delivery Networks
A Content Delivery Network is a system of distributed servers (network) that deliver webpages and other Web content to a user based on the geographic locations of the user, the origin of the webpage and a content delivery server. The goal of a CDN is to establish higher quality network co
From playlist Computer Science and Software Engineering Theory with Briana
From playlist Communications & Network Systems

An intro to the core protocols of the Internet, including IPv4, TCP, UDP, and HTTP. Part of a larger series teaching programming. See codeschool.org
From playlist The Internet
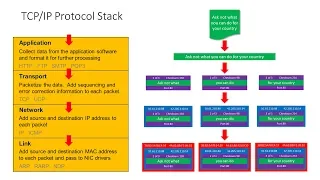
Computer Networks. Part Six: The TCP/IP Protocol Stack and Routers
This is the sixth in a series about computer networks. This video describes the role of a network protocol, and specifically details the TCP/IP suite of protocols. The need for a layered approach to networking software is discussed including the four layer TCP/IP stack and the relevance
From playlist Computer Networks

Our job might be to build web applications, but we can't build apps that rely on networking if we don't know how these networks and the big network that connects them all (this thing called the Internet) actually work. I'll walk through the basics of networking, then dive a lot deeper (fro
From playlist DevOps

!!Con 2017: How Merkle Trees Enable the Decentralized Web! by Tara Vancil
How Merkle Trees Enable the Decentralized Web! by Tara Vancil Decentralized networks operate without relying on a central source of truth, and instead rely on group coordination in order to establish a shared state. Trust is distributed among participants, so to have confidence that each
From playlist !!Con 2017

DevOps Prerequisites Course - Getting started with DevOps
Learn about DevOps with this beginner's course. The course covers the basic prerequisites knowledge needed for your journey into the Cloud and DevOps world. You will learn things like setting up a basic lab environment using VirtualBox, dealing with networking issues, using the Linux comma
From playlist DevOps Courses

Speaker: Thorsten Holz Storm Worm Not only the Web has reached level 2.0, also attacks against computer systems have advanced in the last few months: Storm Worm, a peer-to-peer based botnet, is presumably one of the best examples of this development. Instead of a central command & cont
From playlist 24C3: Full steam ahead

The Splinternet | This Is How The Internet Dies
Support independent research and analysis by joining my Patreon page: https://www.patreon.com/thehatedone Many academics are sounding alarms that the death of the unified global Internet is already happening. More and more countries are voicing their desire for digital sovereignty and te
From playlist Decrypted Lies

Networking Fundamentals - Part 1/2
Course: IMT2681 - Cloud Computing Networking Stack; ISO OSI Model
From playlist Archive - Cloud Computing

Docker Stack, Networking & Security | Docker Concepts Explained | Edureka | Docker Live - 2
🔥Edureka DevOps Certification Courses: https://www.edureka.co/devops-certification-training This Edureka session on ‘Docker Stack, Networking & Security’ will discuss the various fundamental concepts of Docker with examples. 🔹Check out our Playlist: https://bit.ly/2KlsEva
From playlist Edureka Live Classes 2020

Black Hat DC 2010: Exploiting Lawful Intercept to Wiretap the Internet 2/6
Clip 2/6 Speaker: Tom Cross Many governments require telecommunications companies to provide interfaces that law enforcement can use to monitor their customer's communications. If these interfaces are poorly designed, implemented, or managed they can provide a backdoor for attackers to
From playlist Black Hat DC 2010

IMT4130 Introduction to Blockchain Technology
Introduction: Blockchain Technologies, Distributed Ledgers, Peer to Peer networking, public-private key crypto
From playlist Archive - Research in Mobile/Wearable Tech