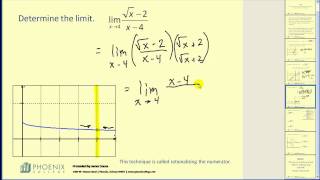
Constraint Enforcement for Improved Safety | Learning-Based Control, Part 2
Learn about the constraints of your system and how you can enforce those constraints so the system does not violate them. In safety-critical applications, constraint enforcement ensures that any control action taken does not result in the system exceeding a safety bound. Constraint enforce
From playlist Learning-Based Control

(ML 11.4) Choosing a decision rule - Bayesian and frequentist
Choosing a decision rule, from Bayesian and frequentist perspectives. To make the problem well-defined from the frequentist perspective, some additional guiding principle is introduced such as unbiasedness, minimax, or invariance.
From playlist Machine Learning

This video covers the laws of limits and how we use them to evaluate a limit. These laws are especially handy for continuous functions. More theorems about limits are introduced in later videos. For more videos visit http://www.mysecretmathtutor.com
From playlist Calculus

This is How You Use the Chain Rule in Calculus
This is How You Use the Chain Rule in Calculus
From playlist Random calculus problems:)
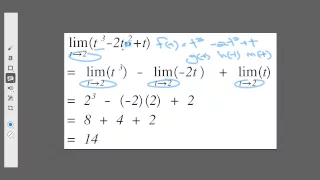
Describing the common laws of limits. Knowing these will greatly simplify your calculations of limits.
From playlist Life Science Math: Limits in calculus

Computing Limits from a Graph with Infinities
In this video I do an example of computing limits from a graph with infinities.
From playlist Limits

A02 Independence of the solution set
The independence of a linear system. How to make sure that a set of solutions are not constant multiples of each other.
From playlist A Second Course in Differential Equations
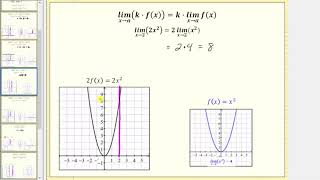
This video covers the properties of limits and verifies them graphically.
From playlist Limits

Twitch Talks - Convex Optimization
Presenter: Rob Knapp Wolfram Research developers demonstrate the new features of Version 12 of the Wolfram Language that they were responsible for creating. Previously broadcast live on September 26, 2019 at twitch.tv/wolfram. For more information, visit: https://www.wolfram.com/language/
From playlist Twitch Talks

Part IV: Matrix Algebra, Lec 5 | MIT Calculus Revisited: Multivariable Calculus
Part IV: Matrix Algebra, Lecture 5: Maxima and Minima in Several Variables Instructor: Herbert Gross View the complete course: http://ocw.mit.edu/RES18-007F11 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT Calculus Revisited: Multivariable Calculus

O'Reilly Webcast: View Updating: How to Make it Work
Ever since the relational view concept was first invented, view updating has been a contentious issue. Support in today's SQL products is ad hoc and meager at best. The SQL standard is even more impenetrable in this area than it usually is. Even the research literature is weak on this topi
From playlist O'Reilly Webcasts 2

Rasa Reading Group: Task-Oriented Dialogue as Dataflow Synthesis (Part 2)
This week we'll continue reading, "Task-Oriented Dialogue as Dataflow Synthesis" (Transactions of the Association for Computational Linguistics, 8, 556-571, 2020) by Jacob Andreas, John Bufe, David Burkett, Charles Chen, Josh Clausman, Jean Crawford, Kate Crim, Jordan DeLoach, Leah Dorner,
From playlist Rasa Reading Group

MIT CMS.608 Game Design, Spring 2014 Instructor: Philip Tan, MIT Students View the complete course: https://ocw.mit.edu/CMS-608S14 YouTube Playlist: https://www.youtube.com/playlist?list=PLUl4u3cNGP63YWzCDORR965yCmHiCKF9Z Making usable games and putting restraints on player actions. Lice
From playlist MIT CMS.608 Game Design, Spring 2014

CERIAS Security: Automatic Signature Generation for Unknown Vulnerabilities 3/5
Clip 3/5 Speaker: Weidong Cui · Microsoft In this talk, I will present a new approach to automatically generate a vulnerability signature for an unknown vulnerability, given a zero-day attack instance. Our approach is based on two systems we developed: Tupni and ShieldGen. Tupni ta
From playlist The CERIAS Security Seminars 2008

Live CEOing Ep 538: Language Design in Wolfram Language [WithLock, Dataset & More]
In this episode of Live CEOing, Stephen Wolfram discusses upcoming improvements and features to the Wolfram Language. If you'd like to contribute to the discussion in future episodes, you can participate through this YouTube channel or through the official Twitch channel of Stephen Wolfram
From playlist Behind the Scenes in Real-Life Software Design

Lecture 9 | MIT 6.832 Underactuated Robotics, Spring 2009
Lecture 9: Trajectory optimization Instructor: Russell Tedrake See the complete course at: http://ocw.mit.edu/6-832s09 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.832 Underactuated Robotics, Spring 2009

Model Aircraft Design Optimization with MATLAB
Guilherme and Connell go through the “Aircraft Design Optimization with the Fixed-Wing Object” example shipped with Aerospace Toolbox in R2022b. The example uses the rules for the Regular Class aircraft of the 2020–2021 Society of Automotive Engineers (SAE®) Aero Design competition and opt
From playlist Aerospace: Student Tutorials and Videos
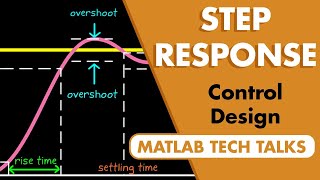
The Step Response | Control Systems in Practice
Check out the other videos in this series: https://www.youtube.com/playlist?list=PLn8PRpmsu08pFBqgd_6Bi7msgkWFKL33b This video covers a few interesting things about the step response. We’ll look at what a step response is and some of the ways it can be used to specify design requirements f
From playlist Control Systems in Practice

IMT2681 - Cloud Technologies: Heroku
IMT2681 - Cloud Technologies: Heroku, Web Server Intro to horizontal scaling, Heroku architecture, managing the apps API design, choices, statelessness.
From playlist Archive - Cloud Computing