
Network Security: Classical Encryption Techniques
Fundamental concepts of encryption techniques are discussed. Symmetric Cipher Model Substitution Techniques Transposition Techniques Product Ciphers Steganography
From playlist Network Security

Network Security, Part 2 : Public Key Encryption
Fundamental concepts of public key encryption are discussed. RSA encryption method explained with an example. Confidentiality of message is presented.
From playlist Cryptography, Security

SSH Authentication - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Message Authentication Codes: Part 1
Message Authentication MACs based on Hash Functions: HMAC MACs based on Block Ciphers: DAA and CMAC Authenticated Encryption: CCM and GCM Pseudorandom Number Generation Using Hash Functions and MACs
From playlist Network Security

Message Authentication Codes: Part 2
Message Authentication MACs based on Hash Functions: HMAC MACs based on Block Ciphers: DAA and CMAC Authenticated Encryption: CCM and GCM Pseudorandom Number Generation Using Hash Functions and MACs
From playlist Network Security

Public Key Cryptography & RSA: Part 1
Fundamental concepts of Public Key Encryption are discussed. RSA Public Encryption is presented. Optimization of Private Key operations is analyzed. Public Key Encryption Symmetric vs. Public-Key RSA Public Key Encryption RSA Key Construction Optimizing Private Key Operations RSA Securit
From playlist Network Security

Network Security, Part 1 : Basic Encryption Techniques
Fundamental concepts of network security are discussed. It provides a good overview of secret Key and public key Encryption. Important data encryption standards are presented.
From playlist Network Security

Fundamental concepts of IPSec are discussed. Authentication Header is explained. Encapsulating Security Payload (ESP) and Internet Key Exchange (IKE) are analyzed.
From playlist Network Security

Anne Broadbent - Information-Theoretic Quantum Cryptography Part 2 of 2 - IPAM at UCLA
Recorded 27 July 2022. Anne Broadbent of the University of Ottawa presents "Information-Theoretic Quantum Cryptography" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: These lectures are an introduction to the interplay between quantum information and cryp
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography
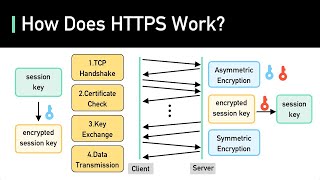
To get better at system design, subscribe to our weekly newsletter: https://bit.ly/3tfAlYD Checkout our bestselling System Design Interview books: Volume 1: https://amzn.to/3Ou7gkd Volume 2: https://amzn.to/3HqGozy ABOUT US: Covering topics and trends in large-scale system design, from
From playlist Computer Science Fundamentals

Stanford Seminar - The TLS 1.3 Protocol
"The TLS 1.3 Protocol" - Eric Rescorla of Mozilla and RTFM, Inc. About the talk: Transport Layer Security (TLS) is used for securing everything from Web transactions (HTTPS) to voice and video calls (DTLS-SRTP). However, the basic design of TLS dates back to the mid 1990s and the protocol
From playlist Engineering

TraversalConf 2019: Your Data is Showing by Madison Kerndt
TraversalConf 2019: Your Data is Showing by Madison Kerndt
From playlist TraversalConf 2019

In this PHP Security video tutorial I go over the most vulnerable ways hackers attack websites. Website Authentication Cracking and Client Side Manipulation with Intercepting Proxy.
From playlist PHP Security

Whatsapp vs Signal vs Telegram - What is the best Messaging App?
Matt tries to go through and find the best messaging app for Linux users. -----💲💲 Support the Show 💲💲-- http://patreon.com/thelinuxcast -- Follow us 🐧🐧 -- http://twitter.com/thelinuxcast http://twitter.com/mtwb Subscribe at http://thelinuxcast.org Contact us thelinuxcast@gmail.com htt
From playlist Versus

OWASP AppSecUSA 2012: Reverse Engineering Secure HTTP API's With an SSL Proxy
Speakers: Alejandro Caceres and Mark Haase The proliferation of mobile devices has led to increased emphasis on native applications, such as Objective-C applications written for iOS or Java applications written for Android. Nonetheless, these native client applications frequently use HTTP
From playlist OWASP AppSecUSA 2012

Mathematics in Cryptography III - Toni Bluher
2018 Program for Women and Mathematics Topic: Mathematics in Cryptography III Speaker: Toni Bluher Affiliation: National Security Agency Date: May 24, 2018 For more videos, please visit http://video.ias.edu
From playlist Mathematics

Certificates - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

NOTACON 8: Keeping secrets for iOS developers
Speaker: Randy Beiter iOS applications frequently miss the mark on securing data whether the user's or the application's itself. Are you using SSL for talking to a remote API but embedding the credentials for the service cleartext in your application bundle? Securing user data behind a st
From playlist Notacon 8

