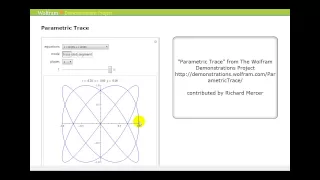
Introduction to Parametric Equations
This video defines a parametric equations and shows how to graph a parametric equation by hand. http://mathispower4u.yolasite.com/
From playlist Parametric Equations
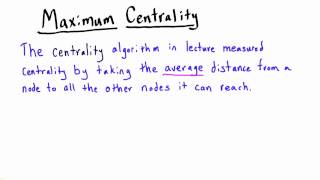
Centrality - Intro to Algorithms
This video is part of an online course, Intro to Algorithms. Check out the course here: https://www.udacity.com/course/cs215.
From playlist Introduction to Algorithms
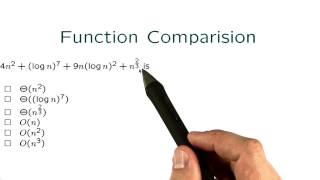
Function Comparision - Intro to Algorithms
This video is part of an online course, Intro to Algorithms. Check out the course here: https://www.udacity.com/course/cs215.
From playlist Introduction to Algorithms

Representing A Graph - Intro to Algorithms
This video is part of an online course, Intro to Algorithms. Check out the course here: https://www.udacity.com/course/cs215.
From playlist Introduction to Algorithms

Newton-Raphson method | Animated and explained | Algorithm for finding roots of a function
The Newton-Raphson method or Newton-Raphson algorithm is a way to numerically determine the roots of some function. It relies on an initial guess where a root of the function might be and then gives an iterative process to find the root. Choosing different starting points one can find all
From playlist Newton-Raphson Algorithm
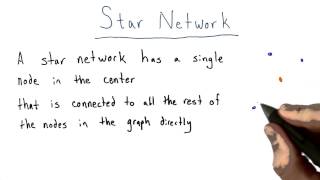
Star Network - Intro to Algorithms
This video is part of an online course, Intro to Algorithms. Check out the course here: https://www.udacity.com/course/cs215.
From playlist Introduction to Algorithms

【PRIM's Algorithm】 Easy & with Example #SoME1
🚀 A short tutorial on how Prim's Algorithm works. Watching this will make you a real Prim-adonna. 😜 📚 Prim's algorithm is a greedy algorithm that finds a minimum spanning tree (=MST) for a weighted undirected graph. This means it finds a subset of the edges that forms a tree that inclu
From playlist Summer of Math Exposition Youtube Videos

Heap Sort - Intro to Algorithms
This video is part of an online course, Intro to Algorithms. Check out the course here: https://www.udacity.com/course/cs215.
From playlist Introduction to Algorithms

Weeds and Protection against them | Crop Production and Management | Don't Memorise
Crops growing in the field seem very calm, but they have to fight a lot with many factors. but who could disturb our crops in the field? to know more about these harmful factors and also to know about the practices carried out once the crops are harvested, do watch this video! To access
From playlist Biology
!!Con 2020 - The Taming of the Clue: Making a Crossword Solver Bot by Chloe Revery
The Taming of the Clue: Making a Crossword Solver Bot by Chloe Revery Have you ever tried to solve a crossword puzzle and walked away stumped? Imagine being a secondhand pen plotter from the 1980s! The humble pen plotter – a robotic arm with pen attachments once used to draw graphs for bu
From playlist !!Con 2020

The Insane Engineering of the A-10 Warthog
Sign up to Nebula here: https://go.nebula.tv/realengineering Patreon: https://www.patreon.com/user?u=2825050&ty=h Facebook: http://facebook.com/realengineering1 Instagram: https://www.instagram.com/brianjamesmcmanus Reddit: https://www.reddit.com/r/RealEngineering/ Twitter: http
From playlist Military

6. Marine Food-Chains: Mercury
Environmental Politics and Law (EVST 255) The military's use of the Puerto Rican island of Vieques as a training site is discussed to highlight the challenges involved in identifying and restoring hazardous sites. Political opposition is faced while attempting to get a site recognized a
From playlist Environmental Politics and Law with John Wargo
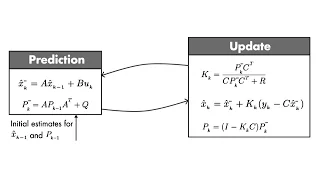
Optimal State Estimator Algorithm | Understanding Kalman Filters, Part 4
Download our Kalman Filter Virtual Lab to practice linear and extended Kalman filter design of a pendulum system with interactive exercises and animations in MATLAB and Simulink: https://bit.ly/3g5AwyS Discover the set of equations you need to implement a Kalman filter algorithm. You’ll l
From playlist Understanding Kalman Filters

HMCS Protecteur Boards Suspicious Somali Fishing Vessel | Warships | Spark
HMCS Protecteur is an auxiliary oil replenisher. Her role in this mission is to provide food fuel and supplies to the warships in the international fleets. At 24,700 tonnes she was built to be a warehouse at sea, sailing through the theatre of operations with her ship’s crew performing two
From playlist Warships

Dr. Bruce Waltke, Psalms, Lecture 2, Psalm 1--Wicket Gate to the Psalter
Biblical eLearning (http://biblicalelearning.org) and Biblical Training (https://www.biblicaltraining.org/book-of-psalms/bruce-waltke) present: Dr. Bruce Waltke on Psalms. A free Digital Psalms Course with multiple lecturers and resources is available at: https://biblicalelearning.org/old
From playlist Dr. Bruce Waltke: Psalms Lectures

PSPP 1.4.0-2 Tutorial Series (Episode 9): One-Way ANOVA
In this PSPP tutorial, I explain how to conduct a One-Way ANOVA (Analysis of Variance), including discussing the output of the source table and reading post-hoc analyses. PSPP: https://www.gnu.org/software/pspp/ NOTE: This tutorial uses the current build of 1.4.0-2 on MacOS. Also part of
From playlist PSPP Tutorials

Black Hat USA 2010: Industrial Bug Mining: Extracting Grading and Enriching the Ore of Exploits 3/4
Speaker: Ben Nagy If bugs are the raw ore of exploits - Rootite, if you like - then we're mining in areas where the Rootite is rare and deeply buried. Industrial scale bug mining starts with very, very fast fuzzing. In contrast to the MS Fuzzing Botnet, we use a dedicated, single purpose
From playlist Black Hat USA 2010

Integrating Your Infrastructure with Chef and How We Did it at HPE - ChefConf 2016
Have you integrated Chef with all the tools in your IT environment? Or putting it a different way, have you integrated your device managers, automated your firmware upgrades, and simplified the provisioning of your bare metal servers and storage with Chef? At Hewlett Packard Enterprise we
From playlist ChefConf 2016
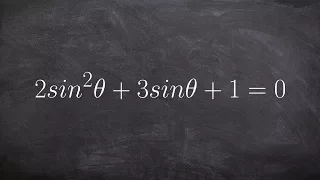
Solve for all of the solutions of an equation when you have to factor
👉 Learn how to solve trigonometric equations. There are various methods that can be used to evaluate trigonometric equations, they include factoring out the GCF and simplifying the factored equation. Another method is to use a trigonometric identity to reduce and then simplify the given eq
From playlist Solve Trigonometric Equations by Factoring

Big O: How Code Slows as Data Grows
Big O notation is a computer science technique for analyzing how code performs as data gets larger. It's a very handy tool for the working programmer, but it's often shrouded in off-putting mathematics. In this talk, I'll teach you what you need to know about Big-O, and how to use it to
From playlist Talks