
[c][explained] Demystifying Pointers — Function Pointers
Find the complete program on https://www.notion.so/theteachr/Function-Pointers-9848de630cae47a7ad1ca5552d23a66d.
From playlist Demystifying Pointers

Definite Integral Using Limit Definition
Please Subscribe here, thank you!!! https://goo.gl/JQ8Nys Definite Integral Using Limit Definition. In this video we compute a definite integral using the limit definition.
From playlist Calculus

Pointers in C / C++ [Full Course]
Pointers in C and C++ are often challenging to understand. In this course, they will be demystified, allowing you to use pointers more effectively in your code. The concepts you learn in this course apply to both C and C++. ✏️ Course developed by Harsha and Animesh from MyCodeSchool. 🔗 R
From playlist C / C++

Using parent graphs to understand the left and right hand limits
👉 Learn how to evaluate the limit of an absolute value function. The limit of a function as the input variable of the function tends to a number/value is the number/value which the function approaches at that time. The absolute value function is a function which only takes the positive val
From playlist Evaluate Limits of Absolute Value

이번 강의는 ' C언어 15강 포인터와 배열 ' 편입니다. 소스코드: http://iotcenter.seoul.go.kr/655
From playlist c언어

Evaluating Limits Definition of Derivative
I work through 2 example evaluating the limit definition of a derivative. Check out http://www.ProfRobBob.com, there you will find my lessons organized by chapters within each subject. If you'd like to make a donation to support my efforts look for the "Tip the Teacher" button on my chann
From playlist Calculus (New)

[c][explained] Demystifying Pointers — What are they?
The addresses and variable locations shown in the video will not be valid in an actual program. The concept goes deeper into understanding memory alignment. I'll drop a link here when I'm done making a video on that. I'd like to thank all the people that have spent their time to correct m
From playlist Demystifying Pointers

The Tame Algebra - Yuval Flicker
Yuval Flicker The Ohio State University December 7, 2009 For more videos, visit http://video.ias.edu
From playlist Mathematics

3. Buffer Overflow Exploits and Defenses
MIT 6.858 Computer Systems Security, Fall 2014 View the complete course: http://ocw.mit.edu/6-858F14 Instructor: James Mickens In this lecture, Professor Mickens discusses topics related to buffer overflow exploits, including baggy bounds handling, mitigation approaches, and return-orient
From playlist MIT 6.858 Computer Systems Security, Fall 2014

How to evaluate the limit of a function by observing its graph
👉 Learn how to evaluate the limit of an absolute value function. The limit of a function as the input variable of the function tends to a number/value is the number/value which the function approaches at that time. The absolute value function is a function which only takes the positive val
From playlist Evaluate Limits of Absolute Value

For more information and to download the video visit: http://bit.ly/30C3_info Playlist 30C3: http://bit.ly/30c3_pl Speaker: Andreas Bogk Violation of memory safety is still a major source of vulnerabilities in everyday systems. This talk presents the state of the art in compiler instrume
From playlist 30C3

Evaluate the left and right hand limit by graphing the function
👉 Learn how to evaluate the limit of an absolute value function. The limit of a function as the input variable of the function tends to a number/value is the number/value which the function approaches at that time. The absolute value function is a function which only takes the positive val
From playlist Evaluate Limits of Absolute Value

Vlog #004: C++/Python methods in memory
If you instantiate an object of a class, is the method bytecode copied to the object as well? If not, then how do virtual methods work?
From playlist Gynvael's Vlog

Lecture 4 - Elementary Data Structures
This is Lecture 4 of the CSE373 (Analysis of Algorithms) course taught by Professor Steven Skiena [http://www3.cs.stonybrook.edu/~skiena/] at Stony Brook University in 2016. The lecture slides are available at: https://www.cs.stonybrook.edu/~skiena/373/newlectures/lecture4.pdf More infor
From playlist CSE373 - Analysis of Algorithms 2016 SBU

Recent progress in query complexity I & II - Pei Wu
Computer Science/Discrete Mathematics Seminar II Topic: Recent progress in query complexity I & II Speaker: Pei Wu Affiliation: Member, School of Mathematics Date: October 5, 2021 The query model is one of the most basic computational models. In contrast to the Turing machine model, fu
From playlist Mathematics

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security
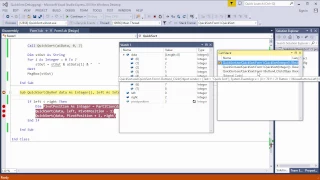
Quicksort 4 – VB.NET Implementation
This video describes a recursive VB.NET implementation of a quicksort. It follows on from previous quicksort videos that covered algorithms for partitioning a list, and pseudocode for a program that calls itself recursively to process successively smaller partitions, until the original li
From playlist Sorting Algorithms

Pointers In C Explained | What Are Pointers in C? | C Pointers | C Language Tutorial | Simplilearn
This video by Simplilearn will explain to you about Pointers In C. This C Programming tutorial will explain to you What Are Pointers in C with an example. how to declare and initialize pointers In C. C pointer to an array, C Pointer to function, and pointer to pointer The video will cover
From playlist C++ Tutorial Videos

27c3: I Control Your Code (en)
Speaker: Mathias Payer Attack Vectors Through the Eyes of Software-based Fault Isolation Unsafe languages and an arms race for new bugs calls for an additional line of defense in software systems. User-space virtualization uses dynamic instrumentation to detect different attack vectors a
From playlist 27C3: We come in peace
