
Double Hash - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Learn how to read key-value pairs from a text file into a HashMap.
From playlist Intermediate Java

Provide Scarcity Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

This video introduces big strings and provides the formulas need to determine the total number of n-bit strings and how to determine the number of n-bit strings with a given weight.
From playlist Counting (Discrete Math)

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Symmetric Key Cryptography: Cryptographic Techniques
This is the fifth in a series about cryptography; an extremely important aspect of computer science and cyber security. It reviews how the XOR logical operation can be used to encrypt at the bit level in symmetric key cryptography, then shows how this can be combined with permutation step
From playlist Cryptography

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

One Time Pad - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography
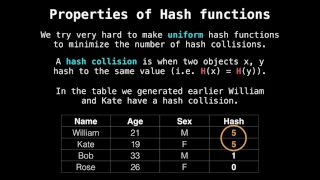
Related Videos: Hash table intro/hash function: https://www.youtube.com/watch?v=2E54GqF0H4s Hash table separate chaining: https://www.youtube.com/watch?v=T9gct6Dx-jo Hash table separate chaining code: https://www.youtube.com/watch?v=Av9kwXkuQFw Hash table open addressing: https://www.youtu
From playlist Data structures playlist
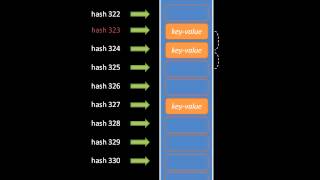
Introductory coverage of fundamental data structures. Part of a larger series teaching programming. Visit http://codeschool.org
From playlist Data Structures

RubyConf 2018 - Let's subclass Hash - what's the worst that could happen? by Michael Herold
RubyConf 2018 - Let's subclass Hash - what's the worst that could happen? by Michael Herold Have you ever been tempted to subclass a core class like Hash or String? Or have you read blog posts about why you shouldn't do that, but been left confused as to the specifics? As a maintainer of
From playlist RubyConf 2018

How HashMap works in Java? With Animation!! whats new in java8 tutorial
How does java hashmap work ? HashMap is one of the most popular java.util data structures. Its one of the associative array implementations, here I have explained its internals in simple terms using an animation. Java8 adds a bit of enhancement to HashMap by using a balanced tree when ther
From playlist Software Development Lectures
This is Lecture 6 of the CSE373 (Analysis of Algorithms) course taught by Professor Steven Skiena [http://www3.cs.stonybrook.edu/~skiena/] at Stony Brook University in 2016. The lecture slides are available at: https://www.cs.stonybrook.edu/~skiena/373/newlectures/lecture6.pdf More infor
From playlist CSE373 - Analysis of Algorithms 2016 SBU

Why Hashes Will Be Faster in Ruby 2.0 by Pat Shaughnessy,
In this micro talk, I'll review the basic theory behind hash functions and hash tables, show you the new internal data structures that Ruby 2.0 uses to save keys and values, and present some performance data that proves this optimization exists and how much time it will actually save you.
From playlist GORUCO 2012
HashDB - Malware API Hashing Obfuscation Solved Forever (Not Clickbait)
Join us for the release of HashDB a free community-source solution to malware API hashing! Expand for more... ----- OALABS DISCORD https://discord.gg/6h5Bh5AMDU OALABS PATREON https://www.patreon.com/oalabs OALABS TIP JAR https://ko-fi.com/oalabs OALABS GITHUB https://github.com/OALabs
From playlist Open Analysis Live!

Cryptography is a complex and confusing subject. In this talk you will learn about the core components of cryptography used in software development: securing data with encryption, ensuring data integrity with hashes and digital signatures, and protecting passwords with key derivation funct
From playlist Blockchain



