
Defcon 2015 20 20T261 20The 20Completion 20Back 1
From playlist DEFCON 15

DEFCON 14: Trusted Computing: Could it be SATAN?
Speaker: Bruce Potter, The Shmoo Group Abstract: Trusted computing is not inherently evil. It sounds scary, but it's true. While the public perception of trusted computing is that content providers will use trusted computing to enforce their digital rights and take away our civil libertie
From playlist DEFCON 14

DEFCON 16: Compromising Windows Based Internet Kiosks
Speaker: Paul Craig, Principal Security Consultant, Security-Assessment.com Internet Kiosks have become common place in today's Internet centric society. Public Internet Kiosks can be found everywhere, from Airports, Train stations, Libraries and Hotels to corporate lobbies and street cor
From playlist DEFCON 16

DEFCON 15: Biting tha Hand that Feeds You - Storing and Serving Malicous Content
Speakers: Billy Rios Senior Security Researcher, VeriSign Nathan McFeters Senior Security Advisor, Ernst & Young Whats in a name? How do you know you should "trust" the content you are receiving? In today's World Wide Web, we place a lot of "trust" into domain names. For many, domain name
From playlist DEFCON 15

Does it really matter what browser I choose?
You have a choice of browsers to select from. What makes a browser more - or less - secure? Learn some ways to assess a browser's security.
From playlist Internet Safety
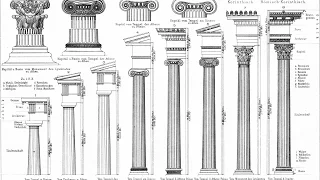
A conversation with Dr. Steven Zucker & Dr. Beth Harris In classical architecture, the Orders consist of variations of an assembly of parts made up of a column (usually with a base), a capital, and an entablature. These structural units may be repeated and combined to form the elevation o
From playlist Art of the ancient Mediterranean | Art History | Khan Academy

Johannes Vermeer, The Art of Painting
Johannes Vermeer, The Art of Painting, 1666-69, oil on canvas, 130 x 110 cm (Kunsthistorisches Museum, Vienna). Speakers: Dr. Steven Zucker & Dr. Beth Harris . Created by Beth Harris and Steven Zucker.
From playlist Baroque to Neoclassical art in Europe | Art History | Khan Academy

Couture, Romans of the Decadence
Thomas Couture, Romans of the Decadence, 1847 (Musée d'Orsay, Paris) Speakers: Dr. Beth Harris & Dr. Steven Zucker For more art history videos visit smarthistory.org. Created by Beth Harris and Steven Zucker.
From playlist Art in 19th century Europe | Art History | Khan Academy

Defcon14 V36 Geers and Eisen IPv6 World Update
From playlist DEFCON 14

Gustave Caillebotte, Paris Street; Rainy Day
Gustave Caillebotte, Paris Street; Rainy Day, 1877, oil on canvas 83-1/2 x 108-3/4 inches / 212.2 x 276.2 cm (The Art Institute of Chicago). View this work up close on the Google Art Project. Created by Beth Harris and Steven Zucker.
From playlist Art in 19th century Europe | Art History | Khan Academy

This video provided three examples of how to write a given function as a composition of functions. Site: http://mathispower4u.com Blog: http://mathispower4u.wordpress.com
From playlist Determining Composite Functions and Composite Function Values

Nude woman (Venus of Willendorf)
Nude Woman (Venus of Willendorf), c. 28,000-25,000 B.C.E., Limestone, 4 1/4" high (Naturhistorisches Museum, Vienna). Created by Beth Harris and Steven Zucker.
From playlist Prehistoric art in Europe and West Asia | Art History | Khan Academy

DEFCON 13: Internet Survivability, Threats and Efforts
Speakers: Paul Vixie Gadi Evron In this lecture we will begin with a brief introduction on a couple of the common or not so common threats that exist to the Internet and Internet infrastructure today, provide with some statistics and discuss the harm rather than potential risks. We wil
From playlist DEFCON 13

Speakers: Dr. Beth Harris and Dr. Steven Zucker.
From playlist Art history basics | Art History | Khan Academy

Data Science @Stanford Russ Altman 11/18/2015
Russ Altman discusses extracting genomics knowledge from text and using it for novel inference at the November 18, 2015 Data Science @Stanford seminar.
From playlist Data Science @ Stanford

Frans Hals, Malle Babbe, c. 1633, oil on canvas, 78.50 x 66.20 cm (Gemäldegalerie, Staatliche Museen zu Berlin). Created by Beth Harris and Steven Zucker.
From playlist Baroque to Neoclassical art in Europe | Art History | Khan Academy

Ex: Solve a System of Three Equations Using a Matrix Equation
This video explains how to solve a system of three linear equations with three unknowns using a matrix equation. Site: http://mathispower4u Blog: http://mathispower4u.wordpress.com
From playlist Matrix Equations

DEFCON 20: Shared Values, Shared Responsibility
Speaker: GENERAL KEITH B. ALEXANDER COMMANDER, US CYBER COMMAND (USCYBERCOM) AND DIRECTOR, NATIONAL SECURITY AGENCY/CHIEF, CENTRAL SECURITY SERVICE (NSA/CSS) We as a global society are extremely vulnerable and at risk for a catastrophic cyber event. Global society needs the best and brig
From playlist DEFCON 20

