
CERIAS Security: John Oritz: Steganography 2/6
Clip 2/6 Speaker: John Oritz · SRA International Steganography is a discipline of computer science whose aim is to conceal the existence of information. Steganography synergizes various technologies including data compression, digital signal processing, information theory, data networks,
From playlist The CERIAS Security Seminars 2008

CERIAS Security: John Oritz: Steganography 3/6
Clip 3/6 Speaker: John Oritz · SRA International Steganography is a discipline of computer science whose aim is to conceal the existence of information. Steganography synergizes various technologies including data compression, digital signal processing, information theory, data networks,
From playlist The CERIAS Security Seminars 2008

CERIAS Security: John Oritz: Steganography 6/6
Clip 6/6 Speaker: John Oritz · SRA International Steganography is a discipline of computer science whose aim is to conceal the existence of information. Steganography synergizes various technologies including data compression, digital signal processing, information theory, data networ
From playlist The CERIAS Security Seminars 2008

CERIAS Security: John Oritz: Steganography 4/6
Clip 4/6 Speaker: John Oritz · SRA International Steganography is a discipline of computer science whose aim is to conceal the existence of information. Steganography synergizes various technologies including data compression, digital signal processing, information theory, data networks,
From playlist The CERIAS Security Seminars 2008

Steganography Tutorial - Hide Messages In Images
Steganography is the hiding of a secret message within an ordinary message and the extraction of it at its destination. Steganography takes cryptography a step further by hiding an encrypted message so that no one suspects it exists. Ideally, anyone scanning your data will fail to know it
From playlist Ethical Hacking & Penetration Testing - Complete Course

CERIAS Security: John Oritz: Steganography 5/6
Clip 5/6 Speaker: John Oritz · SRA International Steganography is a discipline of computer science whose aim is to conceal the existence of information. Steganography synergizes various technologies including data compression, digital signal processing, information theory, data networ
From playlist The CERIAS Security Seminars 2008

Motorcycle camera - Raw footage 1/2
Raw footage from Dr Alex Stedmon's motorcycle camera test. One of two videos. For more information about Dr Stedmon's work and research, visit http://www.test-tube.org.uk/morestuff/bikesim_index.htm As part of his research into motorcycle ergonomics, Dr Alex Stedmon has been experimenti
From playlist Motorcycle research

Motorcycle camera - Raw footage 2/2
Raw footage from Dr Alex Stedmon's motorcycle camera test. One of two videos. For more information about Dr Stedmon's work and research, visit http://www.test-tube.org.uk/morestuff/bikesim_index.htm As part of his research into motorcycle ergonomics, Dr Alex Stedmon has been experimenti
From playlist Motorcycle research

GCSE Science Revision Chemistry "Chromatography"
Find my revision workbook here: https://www.freesciencelessons.co.uk/workbooks Image credit: Coloured pens By RRRST (Own work) [CC BY-SA 4.0 (http://creativecommons.org/licenses/by-sa/4.0)], via Wikimedia Commons
From playlist 9-1 GCSE Chemistry Paper 2 Chemical Analysis

Constructing The Second Largest Ship In The French Navy | Extreme Constructions | Spark
The Thunder Boat (Tonnerre) is the second-largest ship of the Marine Nationale. The structure is fitted with revolutionary equipment, with a range of high technologies, and is able to operate in a range of situations, as it did during Cyclone Irma in 2017 and Beirut in August 2020. This s
From playlist Documentaries To Fall Asleep To

CERIAS Security: John Oritz: Steganography 1/6
Clip 1/6 Speaker: John Oritz · SRA International Steganography is a discipline of computer science whose aim is to conceal the existence of information. Steganography synergizes various technologies including data compression, digital signal processing, information theory, data networks,
From playlist The CERIAS Security Seminars 2008
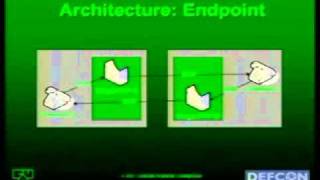
DEFCON 15: Real-time Steganography with RTP
Speaker: I)ruid Computer Academic Underground Real-time Transfer Protocol (RTP) is used almost ubiquitously by Voice over IP technologies to provide an audio channel for calls. As such, it provides ample opportunity for creation of a covert communications channel due to it's very nature a
From playlist DEFCON 15

Lecture 32: Steganography (hidden messages) - Richard Buckland UNSW
Extension lecture introducing steganography (hidden messages). Security via obscurity. Hidden messages in book Godel Escher Bach. In film Starship Troopers. In games. In cryptography. In teaching. Digital watermarking. SETI. Are we in a simulation? Extension lectures are for firs
From playlist CS1: Higher Computing - Richard Buckland UNSW

Blackhat Europe 2010: Steganography and Vulnerabilities in Popular Archives Formats 1/8
Clip 1/8 Speakers: Mario Vuksan, Tomislav Pericin & Brian Karney Exploiting archive formats can lead to steganographic data hiding and to processing errors with serious forensic consequences. These formats are very interesting as they are commonly found on every PC, Apple or Linux machine
From playlist Black Hat Europe 2010

!!Con 2022 - Shhh, Meet Me at Midnight!!! (Audio Steganography in Python) by Marlene Mhangami
Shhh, Meet Me at Midnight!!! (Audio Steganography in Python) The term ‘Audio Steganography’ is derived from the Greek words steganos, meaning “covered,” and graphein, meaning “to write”. It refers to the art of enabling secret communication that uses interesting methods to hide informatio
From playlist !!Con 2022